CVE-2026-20045: Remote Code Execution in Cisco Unified Communications Products

Cisco has disclosed CVE-2026-20045, a critical remote code execution vulnerability affecting multiple Unified Communications products. The flaw has been confirmed as actively exploited in the wild, prompting emergency patches and a swift response from the U.S. Cybersecurity and Infrastructure Security Agency (CISA), which added the vulnerability to its Known Exploited Vulnerabilities catalog on January 21, 2026.
The flaw allows unauthenticated remote attackers to inject arbitrary commands into affected systems, resulting in full device compromise under specific conditions. Given the role Unified Communications servers play inside enterprise networks, exploitation carries consequences far beyond service disruption.
Technical Overview
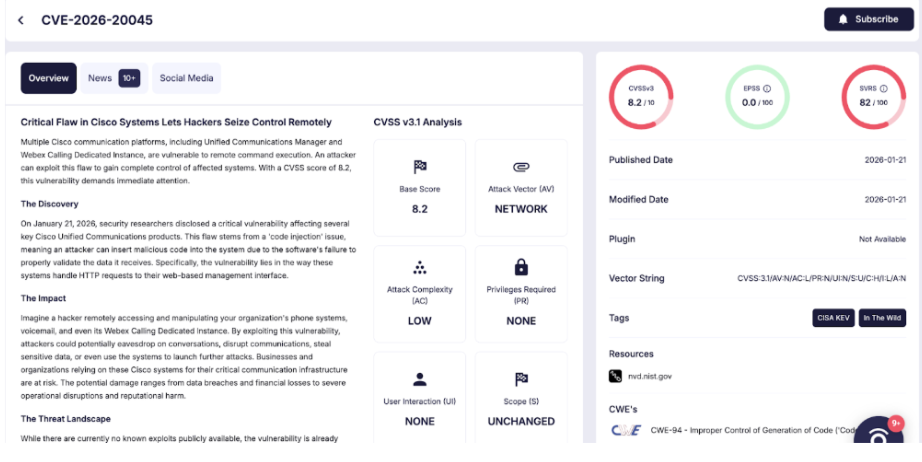
CVE-2026-20045 is a remote code execution vulnerability stemming from improper validation of user-supplied input in HTTP requests sent to Cisco’s web-based management interface. The vulnerability carries a CVSS v3.1 base score of 8.2, classified as High severity, though Cisco has elevated its internal rating to Critical due to the potential for privilege escalation to root access.
The vulnerability resides in the web management interface of affected Cisco Unified Communications products. When processing HTTP requests, the application fails to adequately sanitize user input, allowing specially crafted requests to inject malicious commands into the underlying operating system. The attack vector requires no authentication, meaning any remote attacker with network access to the management interface can attempt exploitation.
Attack Methodology
Successful exploitation follows a multi-stage approach. An unauthenticated attacker constructs a sequence of HTTP requests containing malicious payloads designed to bypass input validation controls. These crafted requests target specific endpoints in the web-based management interface where insufficient sanitization occurs. Upon successful injection, the attacker gains initial access at the user level of the underlying operating system.
From this foothold, the attacker can then escalate privileges to root through additional exploitation techniques. Root-level access provides complete control over the affected system, including the ability to modify configurations, access sensitive data, deploy persistent backdoors, or pivot to other systems within the network perimeter.
Affected Products and Versions
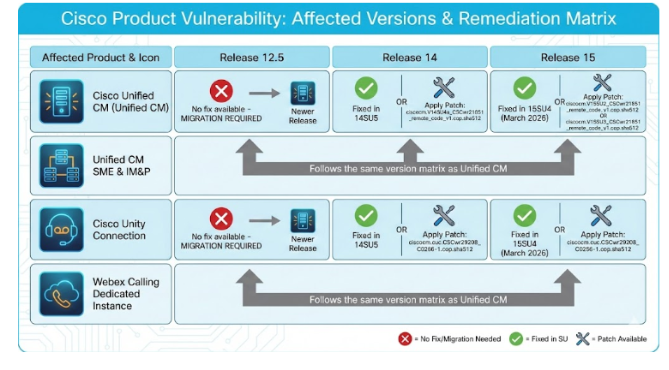
Cisco Unified Communications Manager (Unified CM)
- Release 12.5: No fix available – migration to fixed release required
- Release 14: Fixed in 14SU5 or apply patch ciscocm.V14SU4a_CSCwr21851_remote_code_v1.cop.sha512
- Release 15: Fixed in 15SU4 (March 2026) or apply patch ciscocm.V15SU2_CSCwr21851_remote_code_v1.cop.sha512 or ciscocm.V15SU3_CSCwr21851_remote_code_v1.cop.sha512
Unified CM Session Management Edition (SME)
- Same version matrix as Unified CM
Unified CM IM & Presence Service (IM&P)
- Same version matrix as Unified CM
Cisco Unity Connection
- Release 12.5: No fix available – migration required
- Release 14: Fixed in 14SU5 or apply patch ciscocm.cuc.CSCwr29208_C0266-1.cop.sha512
- Release 15: Fixed in 15SU4 (March 2026) or apply patch ciscocm.cuc.CSCwr29208_C0266-1.cop.sha512
Webex Calling Dedicated Instance
- Same version matrix as Unified CM
Organizations running Release 12.5 face the most significant remediation challenge as no patches exist for this version. Migration to a supported release represents the only viable mitigattion path.
Evidence of Active Exploitation
Cisco confirmed active exploitation of CVE-2026-20045 prior to public disclosure, qualifying it as a zero-day vulnerability. CISA’s addition to the KEV catalog validates this threat, mandating federal agencies to remediate affected systems by February 11, 2026. While specific attribution remains undisclosed, the exploitation pattern suggests reconnaissance for exposed management interfaces followed by targeted attacks against vulnerable endpoints.
Security researchers have observed scanning activity targeting Cisco Unified Communications infrastructure, indicating broader attacker interest beyond isolated incidents. The absence of authentication requirements significantly lowers the barrier to exploitation, making any internet-exposed management interface a potential target.
Attack Surface Analysis
The primary attack vector involves network access to the web-based management interface. Organizations that expose these interfaces to the internet face immediate risk. Even internal deployments remain vulnerable if an attacker has gained network access through other means, such as phishing, supply chain compromise, or exploitation of perimeter devices.
The vulnerability’s exploitation does not require user interaction or complex social engineering. Attackers only need the ability to send HTTP requests to the management interface. This characteristic makes CVE-2026-20045 particularly dangerous in environments where management interfaces are accessible from untrusted network segments.
For organizations implementing threat detection and response capabilities, monitoring HTTP traffic patterns to Unified Communications management interfaces becomes critical. Anomalous request sequences, unusual header values, or requests from unexpected source IP addresses may indicate exploitation attempts.
Remediation Strategy
Immediate patching represents the most effective mitigation. Organizations should prioritize systems based on exposure level, applying patches first to internet-facing instances, then to internal production systems, and finally to development or staging environments.
For Release 12.5 systems where no patch exists, migration planning should begin immediately. Organizations should assess migration timelines, test compatibility with dependent systems, and develop rollback procedures. During the migration window, implementing compensating controls becomes essential.
Network-level controls provide defense-in-depth. Restricting management interface access through firewall rules, implementing IP allowlisting for authorized administrator addresses, and deploying network segmentation to isolate Unified Communications infrastructure all reduce exposure. However, these controls should supplement, not replace, patching efforts.
Organizations should conduct thorough log reviews for signs of compromise. Examining web server logs for unusual HTTP requests, reviewing authentication logs for unexpected access patterns, and analyzing system logs for privilege escalation attempts can reveal historical exploitation. Cyber threat intelligence platforms can provide indicators of compromise associated with CVE-2026-20045 exploitation to correlate against internal telemetry.
Detection and Response
Security teams should implement monitoring for exploitation indicators. HTTP request analysis should focus on requests containing shell metacharacters, command injection patterns, path traversal sequences, or encoded payloads. Network intrusion detection systems can be configured with signatures targeting known exploitation patterns.
Endpoint detection and response (EDR) solutions should monitor for unauthorized process execution, privilege escalation attempts, and suspicious system calls originating from web server processes. These behaviors may indicate successful exploitation even when network-based detection fails.
For organizations leveraging managed security operations center services, correlation of threat intelligence feeds with internal events becomes crucial. Managed SOC providers with threat hunting capabilities can proactively search for indicators across customer environments, identifying compromises before attackers achieve their objectives.
Conclusion
CVE-2026-20045 represents a significant threat to Cisco Unified Communications deployments. The combination of unauthenticated remote code execution, confirmed active exploitation, and the potential for complete system compromise demands immediate action. Organizations must prioritize patching, implement compensating controls where patches cannot be immediately applied, and conduct retrospective analysis to identify potential compromises.
The vulnerability underscores the critical importance of restricting access to management interfaces, maintaining current patch levels, and deploying layered security controls. As threat actors continue to target enterprise communications infrastructure, organizations must adopt proactive security measures that combine timely patching, continuous monitoring, and threat intelligence to defend against both known and emerging threats.
For comprehensive protection against vulnerabilities like CVE-2026-20045, organizations should consider implementing robust threat detection and response capabilities backed by continuous threat intelligence monitoring and expert security operations support.