Hunting
Cyber
Adversaries
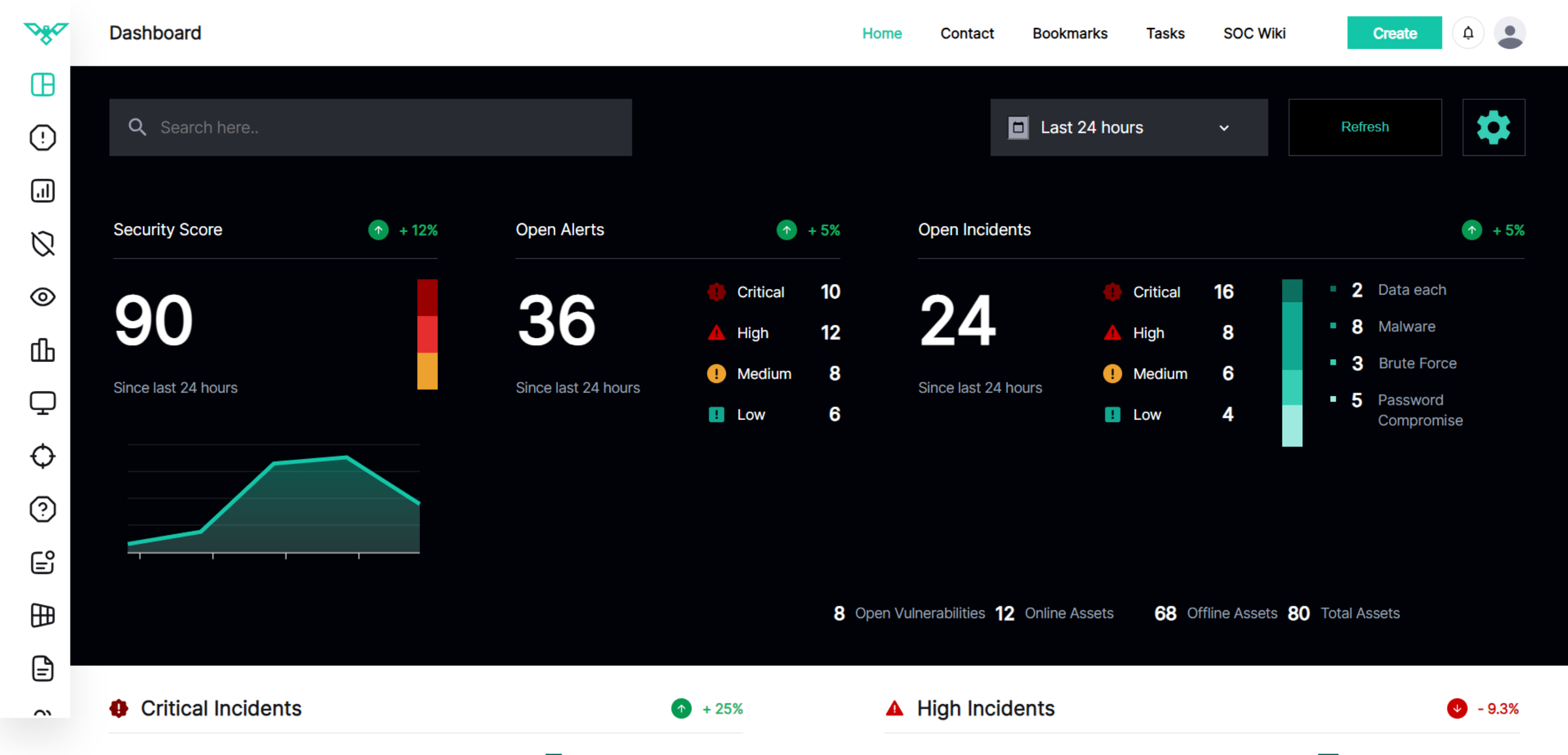
HawkEye in Numbers
Logs Processed Per Week
Users Protected and Growing
Detection Use Cases
Coverage
HawkEye - Your Cyber Guardian
HawkEye Managed CSOC and XDR powered by DTS Solution helps you stay ahead of the cyber threat and adversary landscape.
We strategize, develop, build, and manage your security operations from our state-of-the-art Next Generation Cybersecurity Operations Center.
We continuously monitor your digital assets whilst detecting and protecting from threat actors. Our aim is always to stay one-step ahead of an ever-changing threat and adversary cyberspace and delivering the necessary in-depth visibility you need without having to develop and build cyber capabilities, so that you can focus on your core business.
HawkEye – Fully Managed 24/7 CSOC and XDR
HawkEye Cyber Security Operations Center (CSOC) and XDR powered by DTS Solution is based out of Dubai and Abu Dhabi, United Arab Emirates (UAE) and with regional coverage of Europe, Middle East and Africa.
Cyber Threat Detection with Advanced Machine-Learning
Utilizes Regression, Random Forest, KNN and Naive Bayes based algorithms for threat classification and prediction. Our library of use-cases is unmatched and augmented with autonomous behavior analytics. We pinpoint indicators before they materialize.
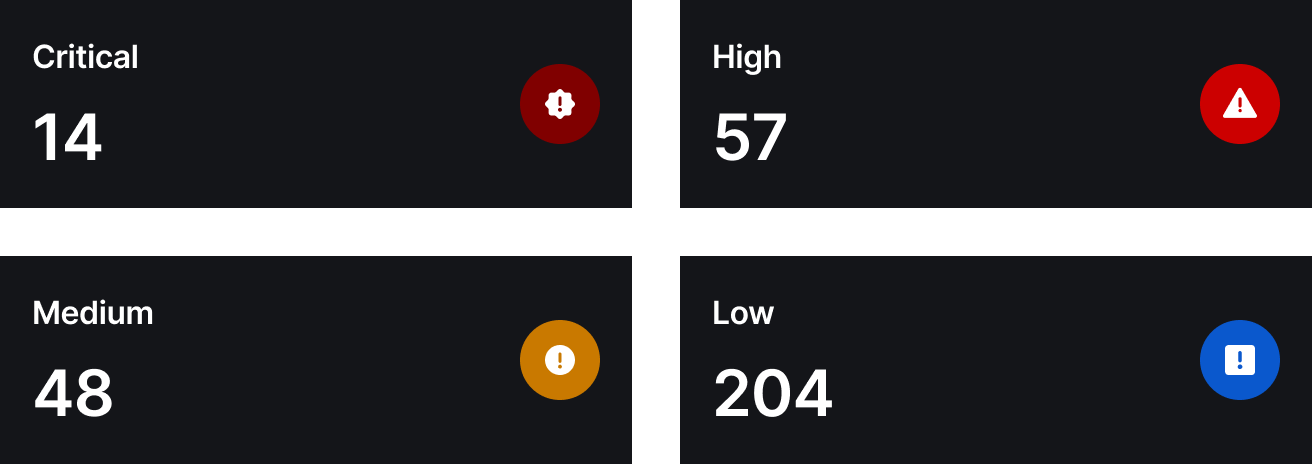
Leaders in SecOps and Threat Intel Fusion
HawkEye is powered by an elite team of cybersecurity professionals, threat intelligence analysts and hunters who have been in the tradecraft for decades. An elite team that is driven by passion to defend and protect.
HawkEye presence across the region means we capture IOCs identified across different environments, multiple attack vectors and share the intelligence across all our clients. This enables us to predict, prepare, detect, and respond to targeted, geographic and industry-based attacks before they materialize.
Cybersecurity is in our DNA
Cybersecurity Knowledge Graph and Multi-Event Correlation
We leverage a sophisticated Cybersecurity Knowledge Graph to elevate its threat detection and response capabilities. Our Knowledge Graph serves as a comprehensive repository that interlinks various cyber threat data points and entities, enabling our platform to understand and analyze the complex relationships between them.
We use advanced Multi-Event Correlation technique that synergizes with the Knowledge Graph. This approach involves aggregating and analyzing multiple security events from diverse sources to identify patterns that may indicate sophisticated cyber attacks.
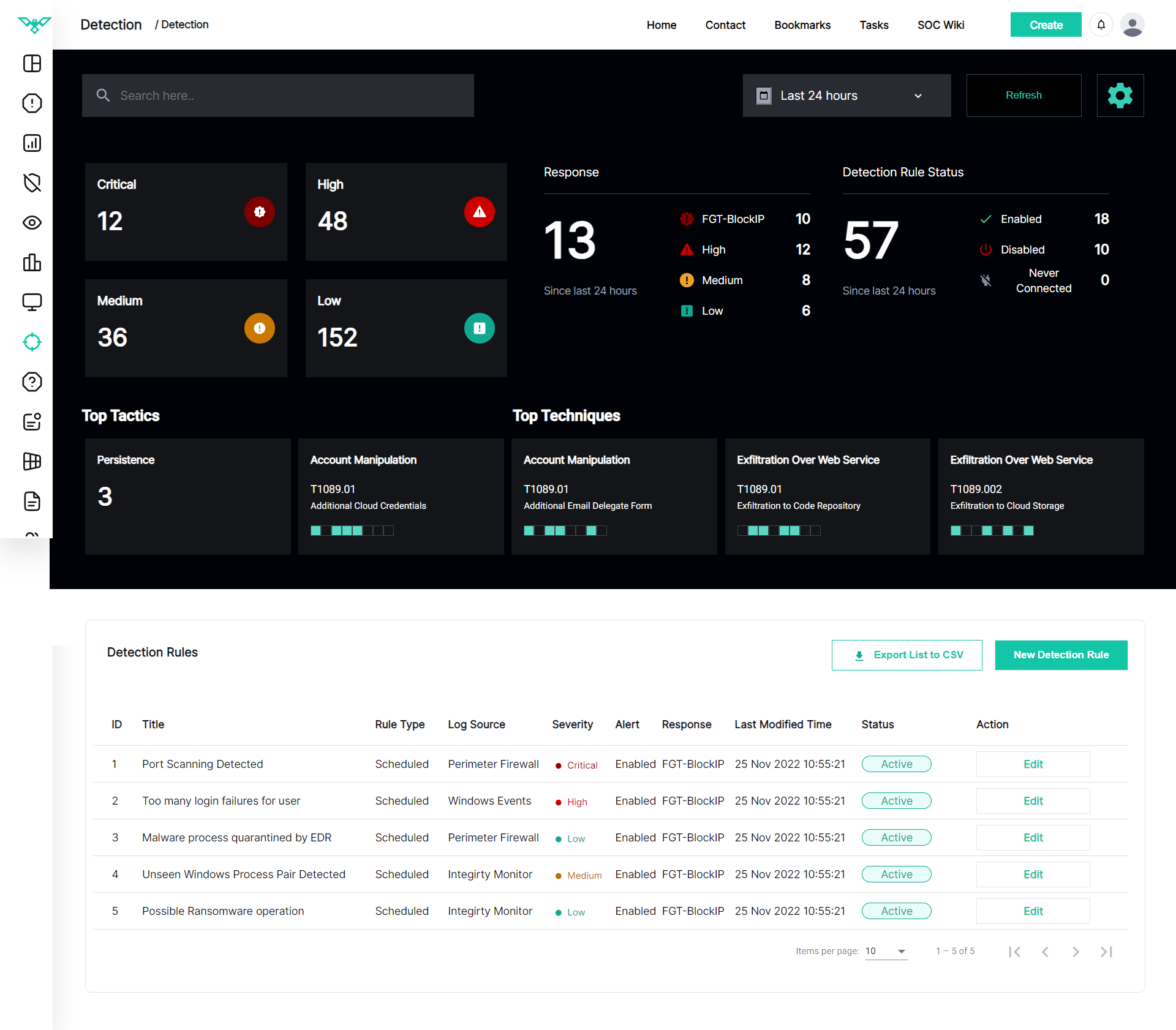
Managed Detection and Response (MDR)






Hackers Don't Sleep, Neither Do We.
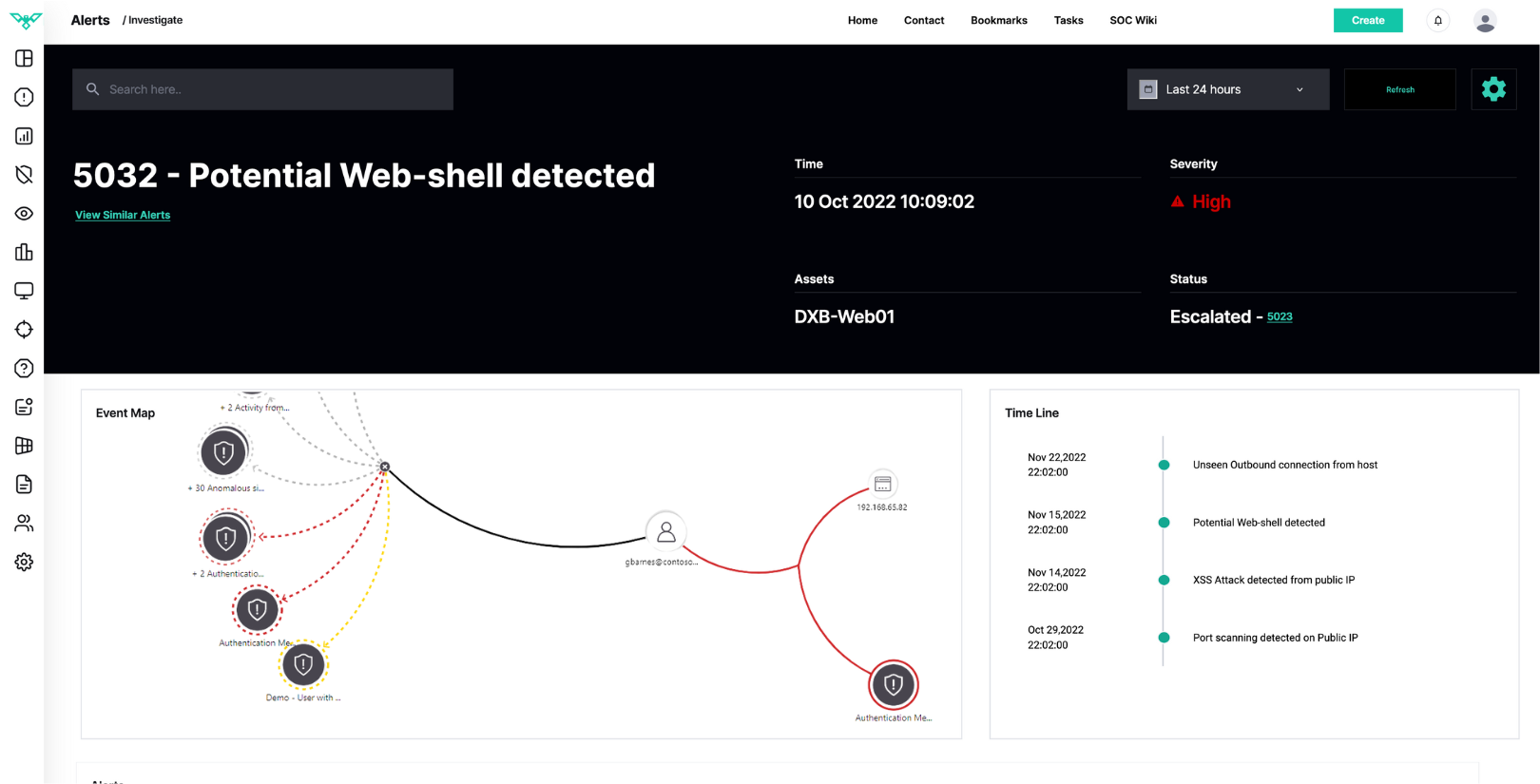
Hunting Cyber Adversaries with HawkEye
Extended Threat Detection and Response powered by DTS Solution
HawkEye - Key Features
HawkEye Managed 24×7 CSOC and XDR service provider is your trusted cybersecurity guardian with the expertise to support your business goals and minimize the impact of cyber-attacks.
We believe HawkEye Managed CSOC as a Service powered by DTS is best placed to support you through the SOC setup and continuous operations.
Real-Time Monitoring
- 24×7 Managed CSOC and XDR
- NG-SIEM, UEBA and Open XDR
- Machine Learning driven CSOC
- Proactive and Predictive Cybersecurity Monitoring
- Deep Security Analytics leveraging Big Data
- Security Events and Log Correlation
- Managed Extended Detection and Response (XDR)
Cyber Threat Management
- Threat Hunting as a Service
- Threat Adversary Detection
- Use Case Development
- Attack Surface Management
- Threat Intelligence
- OSINT and DARKINT
- Brand Monitoring
- Managed Endpoint Detection and Response
- Managed Phishing and Security Awareness
- Vulnerability Risk Prioritization
Incident Management
- Incident Management Process and Plan
- Incident Notification and Response
- Security Incident Response Triage
- Managed SOAR – Security Automation and Orchestration
- Incident Digital Playbooks
- Breach Attack Simulation
- Managed Digital Forensics
Operational Compliance
- CSOC Policies, Processes and Procedures
- Compliance Monitoring Hardening Policy
- Compliance Change Management
- Monitoring Configuration
- Management Monitoring
- Security Audit Monitoring
- 3rd Party Access Monitoring
- Supply Chain Risk Monitoring
- Privileged Access and Activity Monitoring
- Developer Access and Activity Monitoring
- Application, Infrastructure, and cloud Threat Modeling




HawkEye - Operation Model
Outsourced Remote Monitoring – Managed / Hybrid
(Customer-Owned SIEM)
01
Staff Augmentation (Dedicated and onshore)
02
Staff Augmentation (Shared and offshore)
SOC-as-a-Service – Managed / Hybrid
(Cloud SIEM and XDR)
01
SOC-as-a-Service (Shared Multi-Tenant SIEM Platform)
02
SOC-as-a-Service (Dedicated SIEM Platform)
HawkEye - Threat Analytics Capabilities
- Perimeter Monitoring
- Network Security
- Systems Security
- Application Security
- Database Security
- Endpoint Security
- Identity and Access Control
- Malware Hunting
- Vulnerability Management
- Cloud Security Monitoring
- Threat Intelligence
- Vulnerability Disclosure
- Managed Detection and Response
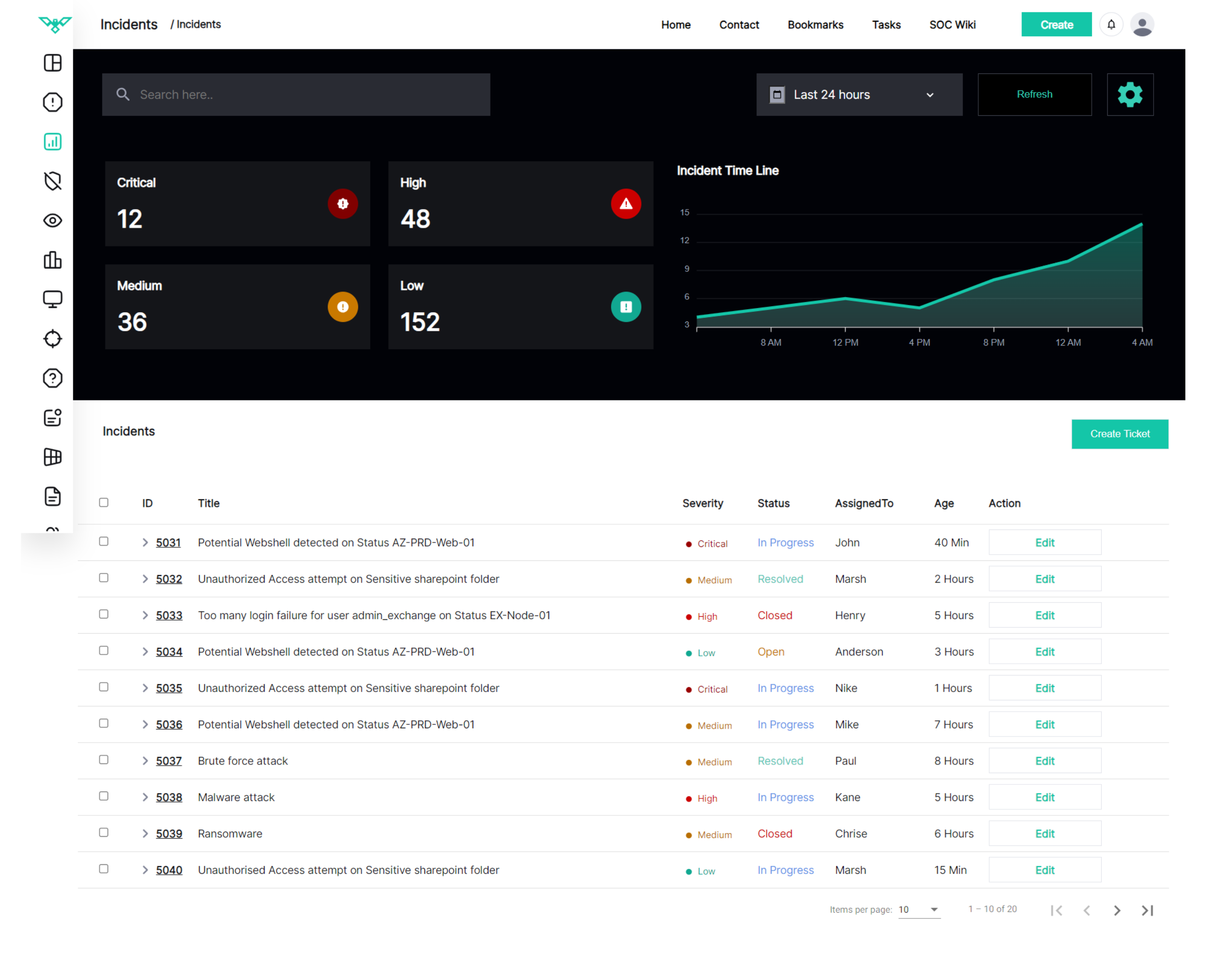
- Incident Response Team
Last message

The Process
We will perform an onsite discovery workshop with the customer to understand the current inherent risk profile based on a series of questions that has been designed to understand current maturity, threat level, exposure and organizational and business value.
The score is then bench-marked across our recommended package matrix to define which service model would be the most appropriate based on the inherent risk profile and types of advanced cyber security monitoring services required.