Active Directory PKI Abuse: Detecting Privilege Escalation Through ADCS
Active Directory Certificate Services (ADCS) serves as the backbone for Public Key Infrastructure (PKI) in enterprise environments, managing digital certificates that secure communications, authenticate users, and enable encrypted transactions. However, misconfigured ADCS implementations create significant security vulnerabilities that attackers exploit for privilege escalation and persistent access.
The challenge lies in detecting these attacks effectively. Unlike traditional password-based attacks, certificate abuse leverages legitimate PKI functionality, making malicious activity harder to spot. Certificates can remain valid for extended periods, providing attackers with long-term access even after password resets or account lockdowns.
The Detection Challenge
ADCS attacks exploit various misconfigurations in certificate templates and Certificate Authority settings. Attackers typically follow a predictable pattern: they enumerate the PKI infrastructure, identify vulnerable certificate templates, request certificates with elevated privileges, and use those certificates for authentication and lateral movement.
The most common attack vectors include:
ESC1 Attacks: Exploiting certificate templates that allow low-privileged users to specify alternative subject names, effectively impersonating high-privileged accounts like domain administrators.
ESC8 Attacks: Leveraging NTLM relay techniques against ADCS web enrollment interfaces to request certificates for compromised machine accounts.
Golden Certificate Attacks: Creating forged certificates using compromised Certificate Authority private keys, providing persistent administrative access.
Essential Logging Configuration
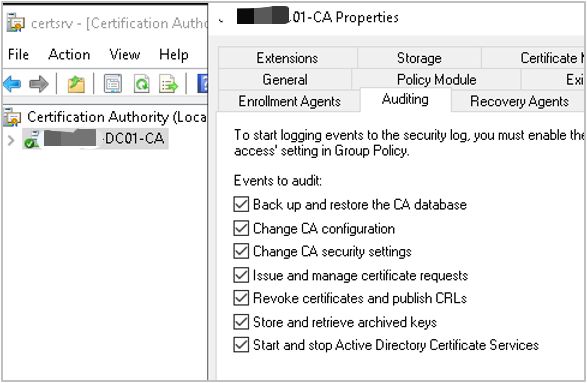
Before implementing detection strategies, organizations must enable comprehensive ADCS auditing. By default, ADCS logging remains disabled, creating blind spots in security monitoring.
To enable proper logging:
- Certificate Authority Auditing: Access the Certificate Authority management console (certsrv.msc), navigate to CA Properties > Auditing tab, and enable all event categories including certificate requests, issuance, and template modifications.
- Domain Controller Event Logging: Configure Event ID 5136 on domain controllers to monitor certificate template modifications and security descriptor changes.
- Process Creation Monitoring: Enable Event ID 4688 with command-line auditing to detect suspicious PowerShell commands and certificate-related tool usage.
Key Detection Indicators
Security teams should monitor specific Windows Security Event IDs that indicate potential ADCS abuse:
Primary Certificate Events:
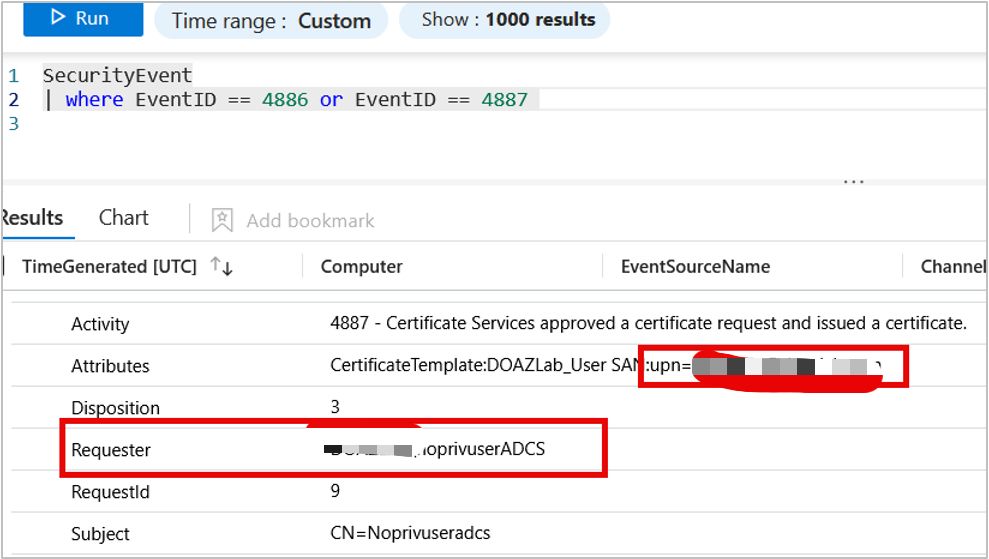
- Event ID 4886: Certificate Services received a certificate request
- Event ID 4887: Certificate Services approved and issued a certificate
- Event ID 4768: Kerberos authentication ticket requested
When these events occur in close succession, they often indicate certificate-based authentication abuse. The critical detection point involves analyzing the relationship between the certificate requester and the certificate subject.
Template Modification Events:
- Event ID 4899: Certificate template was updated
- Event ID 4900: Certificate template security was updated
These events signal potential template tampering, which attackers use to create vulnerable certificate configurations.
Authentication Anomalies: Monitor Kerberos authentication events (4768, 4769) for unusual patterns, particularly authentication requests using certificates with mismatched user principals or unexpected certificate-based logons.
Detection Strategies and Implementation
1. Subject Name Mismatch Detection
The most reliable detection method involves identifying discrepancies between certificate requesters and certificate subjects. In legitimate scenarios, users request certificates for themselves. Attackers exploiting ESC1 vulnerabilities request certificates for other users, typically privileged accounts.
Implement queries that correlate certificate request events (4886) with issuance events (4887), flagging cases where the requester differs from the certificate subject. This pattern strongly indicates privilege escalation attempts.
2. Timeline Analysis
Certificate abuse attacks follow predictable timing patterns. Attackers request certificates and immediately use them for authentication, creating clustered events within short timeframes. Monitor for certificate issuance followed by Kerberos authentication within minutes, particularly when involving privileged accounts.
3. Behavioral Analytics
Establish baselines for normal certificate request patterns in your environment. Flag anomalies such as:
- Certificate requests from service accounts that typically don’t request certificates
- Requests for certificates with extended validity periods
- Certificate requests outside normal business hours
- Multiple certificate requests from the same source in short periods
4. Template Configuration Monitoring
Continuously monitor certificate template configurations for dangerous settings combinations:
- Client Authentication enabled with Enrollee Supplies Subject
- Templates requiring no manager approval or authorized signatures
- Any Purpose Extended Key Usage configurations
- Templates with weak access control permissions
Advanced Detection Techniques
PowerShell and Tool Detection
Monitor for suspicious PowerShell commands and certificate-related tools:
- certreq.exe usage with unusual parameters
- PowerShell cmdlets like Install-AdcsCertificationAuthority
- Third-party tools like Certify or Certipy in network traffic or process creation logs
Network Traffic Analysis
ADCS attacks generate distinctive network patterns:
- Unusual certificate enrollment requests to CA servers
- HTTP/HTTPS traffic to certificate enrollment endpoints from unexpected sources
- LDAP queries targeting certificate template containers in Active Directory
Certificate Store Monitoring
Track certificate installations on endpoints, particularly:
- Certificates installed outside normal deployment mechanisms
- Certificates with suspicious issuers or subject names
- High-privilege certificates installed on low-privilege systems
Implementing Automated Detection
Security Information and Event Management (SIEM) platforms provide excellent foundations for ADCS detection. Create correlation rules that:
- Aggregate Related Events: Combine certificate request, issuance, and authentication events into single incidents for comprehensive analysis.
- Score Risk Factors: Assign risk scores based on multiple factors, including requester-subject mismatches, timing patterns, and involved accounts’ privilege levels.
- Generate Contextual Alerts: Provide security analysts with complete attack timelines, affected accounts, and potential impact assessments.
Example detection logic for Microsoft Sentinel:
SecurityEvent
| where EventID in (4886, 4887, 4768)
| extend ParsedData = parse_xml(EventData)
| project TimeGenerated, EventID, Computer, Account, SubjectUserName, RequesterName
| where RequesterName != SubjectUserName and SubjectUserName contains “admin”
| summarize Events = make_list(EventID) by bin(TimeGenerated, 5m), RequesterName, SubjectUserName
| where array_length(Events) >= 2
Response and Mitigation
When ADCS privilege escalation is detected:
- Immediate Response: Identify and revoke suspicious certificates, reset compromised account passwords, and isolate affected systems.
- Impact Assessment: Determine the scope of access gained by attackers and identify potentially compromised systems or data.
- Forensic Analysis: Collect detailed logs, certificate artifacts, and system images for comprehensive incident analysis.
- Remediation: Address underlying misconfigurations, implement security hardening measures, and enhance monitoring capabilities.
Strengthening ADCS Security
Prevention remains the best defense against ADCS abuse:
Template Hardening: Review and secure certificate templates, removing dangerous configuration combinations and implementing proper access controls.
Permission Management: Apply the principle of least privilege to certificate enrollment permissions and CA administrative access.
Regular Auditing: Conduct periodic assessments of ADCS configurations using tools like PSPKIAudit to identify potential vulnerabilities.
Monitoring Enhancement: Implement comprehensive logging and real-time alerting for certificate-related activities.
Conclusion
ADCS privilege escalation detection requires comprehensive logging, sophisticated analysis techniques, and an understanding of attack patterns. Organizations that implement proper monitoring capabilities can identify certificate abuse early and prevent significant security breaches.
The key to successful detection lies in correlating multiple event sources, understanding normal certificate usage patterns, and maintaining vigilance for the subtle indicators that distinguish legitimate PKI operations from malicious certificate abuse. By implementing these detection strategies, security teams can protect their organizations from one of the most persistent and dangerous Active Directory attack vectors.
Remember that certificate-based attacks provide long-term persistence, making rapid detection and response crucial for limiting attacker access and preventing extensive damage to organizational security posture.