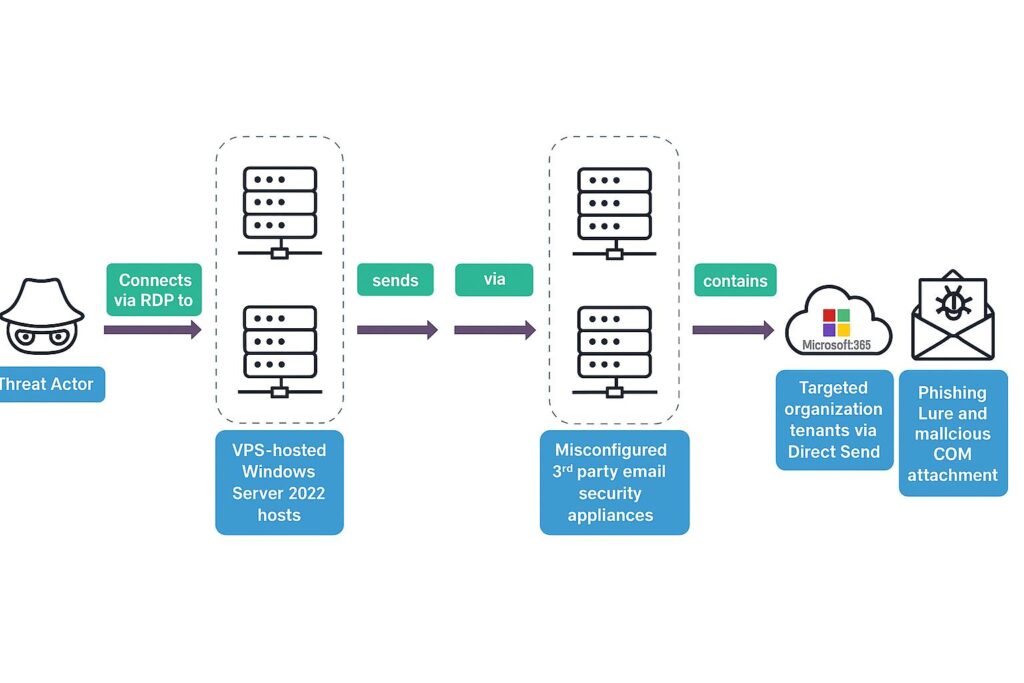
Microsoft 365’s Direct Send Exploited to Bypass Defenses with Internal Phishing

Microsoft’s Direct Send functionality has emerged as a critical attack vector in sophisticated phishing operations, with threat actors exploiting the SMTP relay mechanism to bypass authentication controls and deliver malicious payloads through trusted Microsoft infrastructure. Recent analysis reveals over 70 confirmed organizational compromises since May 2025, demonstrating the scalability and effectiveness of this attack methodology.
Direct Send Architecture and Inherent Vulnerabilities
Direct Send operates as an SMTP smart host service accessible via smtp.office365.com on ports 25 and 587, designed to facilitate email transmission from network devices and applications without requiring OAuth2 authentication or legacy authentication protocols. The service accepts SMTP connections that meet basic RFC 5321 compliance without validating sender identity or implementing rate limiting controls.
The fundamental security flaw lies in the service’s design philosophy: Microsoft’s implementation prioritizes compatibility over security, accepting any properly formatted SMTP transaction that originates from an IP address associated with a Microsoft 365 tenant. This creates a trust boundary violation where external actors can leverage Microsoft’s reputation and infrastructure to deliver malicious content.
Technical Configuration Requirements:
SMTP Server: smtp.office365.com
Ports: 25 (non-encrypted), 587 (STARTTLS)
Authentication: None required
Connection Limits: 10,000 messages per day per tenant
Rate Limiting: 30 messages per minute per connection
The absence of SPF alignment checks for Direct Send traffic means that threat actors can craft messages with arbitrary From headers while maintaining delivery through Microsoft’s infrastructure, effectively bypassing domain-based message authentication reporting and conformance (DMARC) policies.
Attack Methodology and Technical Implementation
Cybercriminals have developed sophisticated PowerShell-based frameworks that automate the exploitation of Direct Send functionality. These frameworks typically implement multi-threaded SMTP client connections with built-in retry logic and error handling to maximize delivery success rates.
Core Attack Components:
SMTP Client Implementation: Attackers use System.Net.Mail.SmtpClient in PowerShell or custom Python scripts with the smtplib library to connect to Microsoft’s smart host. Their implementations include connection pooling and session management to evade Microsoft’s basic rate limiting.
Message Crafting Engine: Advanced template systems produce RFC 5322-compliant messages with carefully designed headers that simulate legitimate organizational emails. This involves manipulating Message-ID patterns, X-Mailer headers, and MIME boundaries to mirror typical organizational email formats.
Payload Delivery Mechanisms: The main attack methods involve PDF attachments with embedded JavaScript or QR codes that link to credential harvesting sites. These PDFs are often generated dynamically with unique identifiers to dodge signature detection and facilitate campaign tracking.
Example PowerShell Implementation Framework:
$SmtpClient = New-Object System.Net.Mail.SmtpClient(“smtp.office365.com”, 587)
$SmtpClient.EnableSsl = $true
$SmtpClient.DeliveryMethod = [System.Net.Mail.SmtpDeliveryMethod]::Network
$SmtpClient.UseDefaultCredentials = $false
Real-World Example: Direct Send in Action
Multiple environments have reported alerts indicating abnormal behavior, specifically labeled as “Activity from stale geolocation to the organization.”
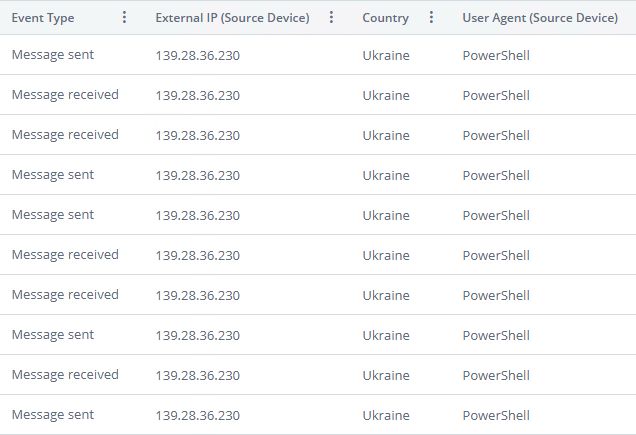
In one notable instance, an alert was triggered by activity originating from a Ukrainian IP address. This was an unusual and unexpected location for the affected tenant. Unlike typical geolocation-related alerts that coincide with login attempts, this incident involved no authentication activity at all. Only outbound email traffic was observed.
Even more suspiciously, the emails appeared to be sent by users to themselves, with PowerShell listed as the sending agent.
This combination of factors, including unexpected geolocation, lack of login activity, self-addressed emails, and script-based email generation, closely aligns with known patterns of Direct Send abuse. The ability to send spoofed messages that appear internal without any form of authentication makes this technique both stealthy and dangerous.
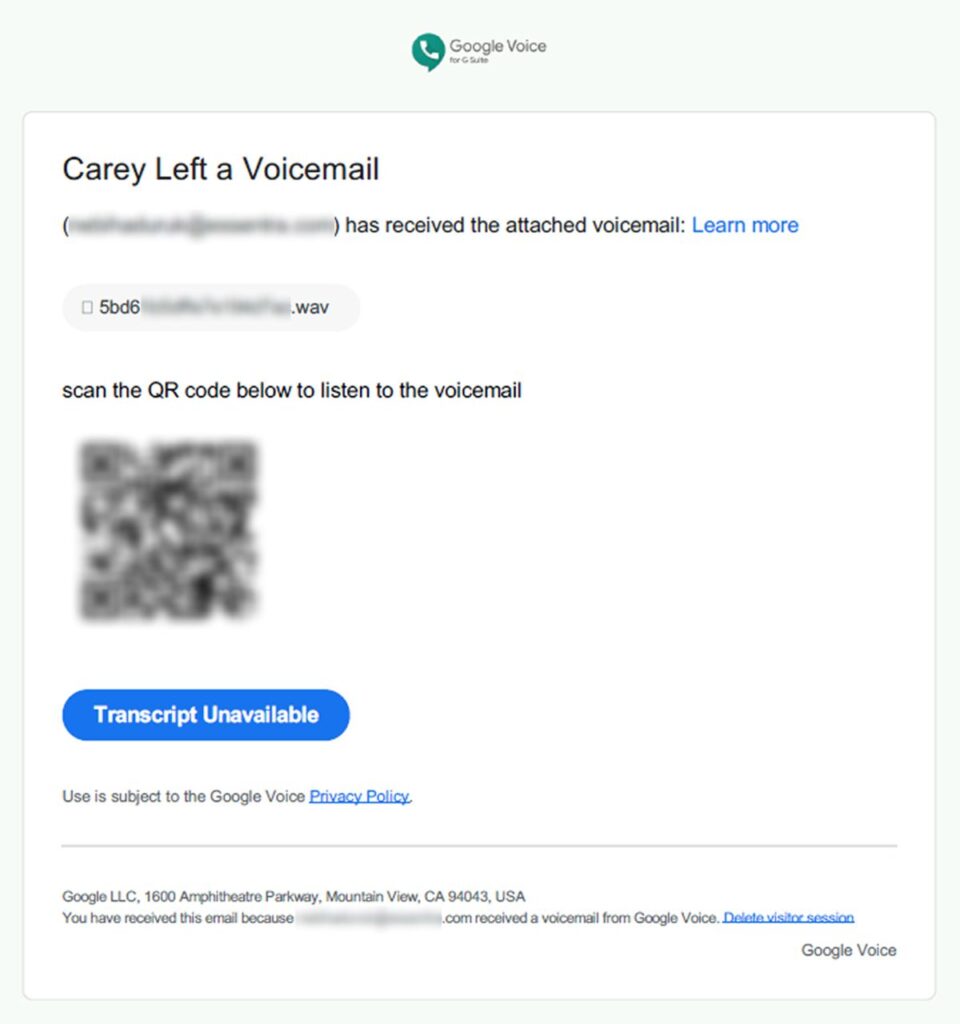
Additional forensic analysis showed that the emails were designed to look like voicemail alerts and included a PDF attachment. This PDF featured a QR code that, when scanned, redirected recipients to a fake login page intended to steal Microsoft 365 credentials.
Header analysis confirmed the suspicion that the attacker was using Direct Send to impersonate internal users without authentication.
The following indicators were observed:
- Received: from [127.0.0.1] (139.28.36[.]230) by company.mail.protection.outlook.com
- authentication-results: spf=softfail (sender IP is 139.28.36[.]230) smtp.mailfrom=company.com; dkim=none (message not signed) header.d=none; dmarc=fail action=oreject
- x-ms-exchange-crosstenant-id: [tenant-id]
The message was sent from an external IP address, failed both SPF and DMARC checks, and had no DKIM signature. Despite these red flags, the email was successfully delivered through the Microsoft 365 smart host. This clearly illustrates how Direct Send can be exploited when proper protections are not in place.
Protocol-Level Evasion Techniques
Advanced threat actors implement several protocol-level evasion techniques to avoid detection and maximize campaign effectiveness:
Header Manipulation: Attackers craft Message-ID headers that follow Microsoft Exchange’s standard format patterns (typically including timestamp and server identifiers) to blend with legitimate organizational email flow. This includes replicating X-MS-Exchange headers and threading identifiers.
MIME Structure Optimization: Messages utilize multipart/mixed or multipart/related MIME structures with specific boundary patterns that match organizational email templates, reducing the likelihood of content-based filtering triggers.
Timing and Volume Distribution: Sophisticated campaigns implement distributed sending patterns that mirror normal organizational communication flows, avoiding the bulk sending patterns that typically trigger behavioral analysis systems.
TLS Implementation: Connections utilize STARTTLS with specific cipher suite preferences that match legitimate Microsoft 365 client implementations, avoiding network-level detection based on TLS fingerprinting.
Advanced Detection Methodologies
Traditional perimeter security solutions fail to identify Direct Send abuse due to the legitimate origin of the SMTP infrastructure. Effective detection requires implementation of advanced behavioral analysis and content inspection techniques:
SMTP Flow Analysis: Organizations should implement deep packet inspection of SMTP transactions to identify anomalous connection patterns, including unusual source IP geolocation, connection frequency deviations, and non-standard client implementations.
Message Header Forensics: Advanced analysis of Received headers can reveal inconsistencies in message routing paths. Legitimate Direct Send messages typically contain specific X-MS-Exchange headers and routing identifiers that malicious messages may lack or incorrectly implement.
Content Entropy Analysis: Machine learning models trained on organizational communication patterns can identify statistical anomalies in message content, vocabulary usage, and structural formatting that indicate external threat actor involvement.
Behavioral Analytics Implementation: Time-series analysis of email sending patterns can identify sudden volume spikes or unusual sending distributions that correlate with phishing campaign activity.
Network-Level Mitigation Strategies
Exchange Transport Rules Configuration: Implement advanced transport rules that inspect Direct Send messages for specific indicators of compromise, including unusual attachment types, suspicious URL patterns, and anomalous sender behavior patterns.
New-TransportRule -Name “Direct Send Anomaly Detection” -SubjectOrBodyContainsWords @(“voicemail”,”fax”,”urgent”) -AttachmentHasExecutableContent $true -RejectMessageReasonText “Suspicious Direct Send Pattern Detected”
SPF Record Hardening: Configure SPF records with explicit IP address specifications and fail policies to prevent unauthorized sending through external infrastructure while maintaining Direct Send functionality for legitimate devices.
v=spf1 include:spf.protection.outlook.com ip4:192.168.1.0/24 -all
DMARC Policy Implementation: Deploy strict DMARC policies with forensic reporting enabled to gain visibility into unauthorized domain usage attempts, though Direct Send may bypass standard DMARC evaluation.
Advanced Threat Protection Configuration: Configure Microsoft Defender for Office 365 with custom detection rules that analyze message patterns, attachment characteristics, and sender behavior specific to Direct Send abuse.
Infrastructure Hardening and Access Controls
Network Segmentation: Implement network segmentation that restricts SMTP outbound connections to authorized devices and applications, preventing unauthorized systems from establishing Direct Send connections.
Certificate-Based Authentication: Where possible, migrate from Direct Send to authenticated SMTP submission using application-specific passwords or certificate-based authentication to eliminate the authentication bypass vulnerability.
Monitoring and Logging Enhancement: Deploy comprehensive SMTP transaction logging with correlation analysis to identify unauthorized usage patterns and establish baseline behavior profiles for legitimate Direct Send usage.
Endpoint Detection Integration: Integrate SMTP connection monitoring with endpoint detection and response (EDR) solutions to identify potentially compromised systems attempting to establish unauthorized email connections.
Recommended actions for Microsoft 365 customers
Here are some tips for protecting your organization:
- Determine if your organization is actively using Direct Send; if appropriate, enable “Reject Direct Send” via PowerShell: Set-OrganizationConfig -RejectDirectSend $true
- Audit mail flow rules for accepted unauthenticated relay IPs; monitor message headers for spoofing attempts that are flagged by Microsoft with compauth=fail
- Enforce email authentication (SPF, DKIM, DMARC) with strict DMARC reject and SPF hard fail policies, where possible, by partnering with a trusted service like HAWKEYE Email Fraud Defense to ensure deliverability of legitimate email
IOCs
Indicator | Notes |
CN=WIN-BUNS25TD77J | CN used by attacker-controlled Windows Server 2022 hosts |
IP Address | Notes |
163.5.112[.]86 | Attacker-controlled Windows Server 2022 host used to initiate SMTP connection |
163.5.160[.]28 | Attacker-controlled Windows Server 2022 host used to initiate SMTP connection |
163.5.160[.]119 | Attacker-controlled Windows Server 2022 host used to initiate SMTP connection |
163.5.160[.]143 | Attacker-controlled Windows Server 2022 host used to initiate SMTP connection |
163.5.169[.]53 | Attacker-controlled Windows Server 2022 host used to initiate SMTP connection |
How HAWKEYE Can Help
HAWKEYE‘s Managed CSOC and XDR powered by DTS Solution combines advanced machine learning algorithms including Regression, Random Forest, KNN and Naive Bayes for threat classification and prediction. Our sophisticated Cybersecurity Knowledge Graph and Multi-Event Correlation capabilities enable us to identify Direct Send abuse patterns by analyzing complex relationships between threat data points and correlating multiple security events from diverse sources.
Our state-of-the-art Next Generation Cybersecurity Operations Center provides 24×7 managed threat detection and response services, with HawkAI leveraging data-driven insights to identify and neutralize potential cyber threats before they escalate into significant issues. Our elite team of cybersecurity professionals, threat intelligence analysts, and hunters have decades of experience in detecting sophisticated email-based attacks like Direct Send exploitation.
HAWKEYE’s presence means we capture IOCs identified across different environments and multiple attack vectors, sharing intelligence across all clients to predict, prepare, detect, and respond to targeted attacks before they materialize. We help organizations defend against cyber threats and malicious threat actors by hunting adversaries from the outside and from within.
Conclusion
The exploitation of Microsoft Direct Send represents a fundamental shift in email-based attack methodologies, demonstrating how threat actors adapt to exploit legitimate business functionality. The technical sophistication of these attacks, combined with their ability to bypass traditional security controls, requires organizations to implement advanced detection and mitigation strategies.
Security professionals must recognize that the convenience features of cloud email platforms often introduce security trade-offs that require careful evaluation and additional protective controls. The Direct Send vulnerability highlights the importance of implementing defense-in-depth strategies that account for trust boundary violations and authentication bypass mechanisms.
Organizations seeking to protect against these advanced email threats require comprehensive security solutions that combine technical controls, behavioral analysis, and threat intelligence capabilities. HAWKEYE provides advanced threat detection and response capabilities specifically designed to identify and mitigate sophisticated phishing campaigns that exploit cloud infrastructure vulnerabilities.