The Oracle Cloud Supply Chain Hack

Background
A major cybersecurity breach has sent shockwaves through global enterprises, as reports emerge of a massive supply chain hack affecting Oracle Cloud. Over 6 million records have allegedly been exfiltrated, impacting more than 140,000 tenants worldwide. While Oracle has officially denied these claims, cybersecurity firms continue to raise alarms, citing potential risks to government entities and enterprises. With 604 domains suspected to be impacted under the .ae and .gov.ae namespaces, it is imperative for organizations in the UAE to take proactive measures to mitigate potential threats.
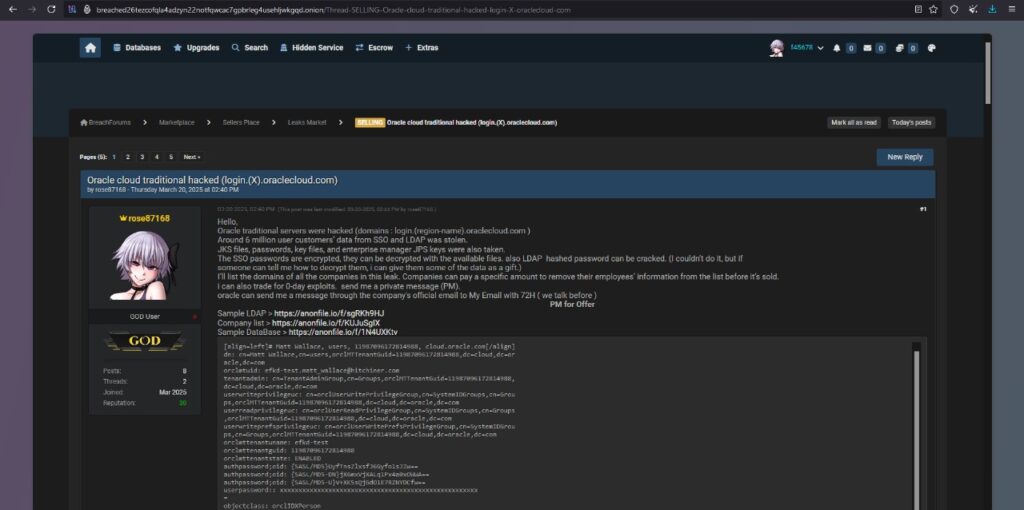
The Alleged Breach: What We Know
According to cybersecurity intelligence sources, threat actors have put up for sale a vast trove of data allegedly stolen from Oracle Cloud. If true, this breach poses significant risks, particularly to enterprises relying on Oracle’s cloud-based solutions for critical business operations. The breach reportedly involves sensitive credentials, authentication tokens, and possibly personally identifiable information (PII) stored within compromised Oracle Cloud environments.
Immediate Mitigation Steps Organizations
Given the uncertainty surrounding Oracle’s official stance, organizations should take immediate proactive measures:
1. Raise a Security Ticket with Oracle
Organizations should contact Oracle Support immediately and request official communication to determine whether their specific tenant, including edb.gov.ae and other UAE-based entities, is affected. This will provide clarity on the scope of exposure and recommended Oracle-endorsed remediation measures.
2. Secure LDAP and Cloud Credentials
– Immediately reset all LDAP user account passwords, especially those used for integration with Oracle services.
– Enforce strong password policies and mandatory Multi-Factor Authentication (MFA) to minimize unauthorized access.
– If using SASL/MD5 hashes for authentication, regenerate them or migrate to a more secure alternative.
3. Rotate Tenant-Specific Identifiers
– Reach out to Oracle to rotate unique tenant identifiers such as `orclmttenantguid` and `orclmttenantuname`.
– Implement access control mechanisms that limit exposure to tenant credentials.
4. Regenerate Certificates and Secrets
– If Single Sign-On (SSO), Security Assertion Markup Language (SAML), or OpenID Connect (OIDC) secrets or certificates are in use, organizations must revoke, regenerate, and replace them immediately.
– Implement stringent certificate lifecycle management to avoid prolonged exposure.
5. Strengthen Security Policies
– Adopt a zero-trust security model and enforce least-privilege access controls.
– Enable robust logging mechanisms to detect unauthorized activities related to Oracle Cloud services.
– Rotate all Oracle-related cloud and Active Directory (AD) credentials.
– If any Oracle-integrated service connects to AD, isolate or disable it until security measures are confirmed.
Contact for More Information
For further details or assistance, reach out to [email protected]