Recent CrowdStrike Outage and It Being Abused
Background
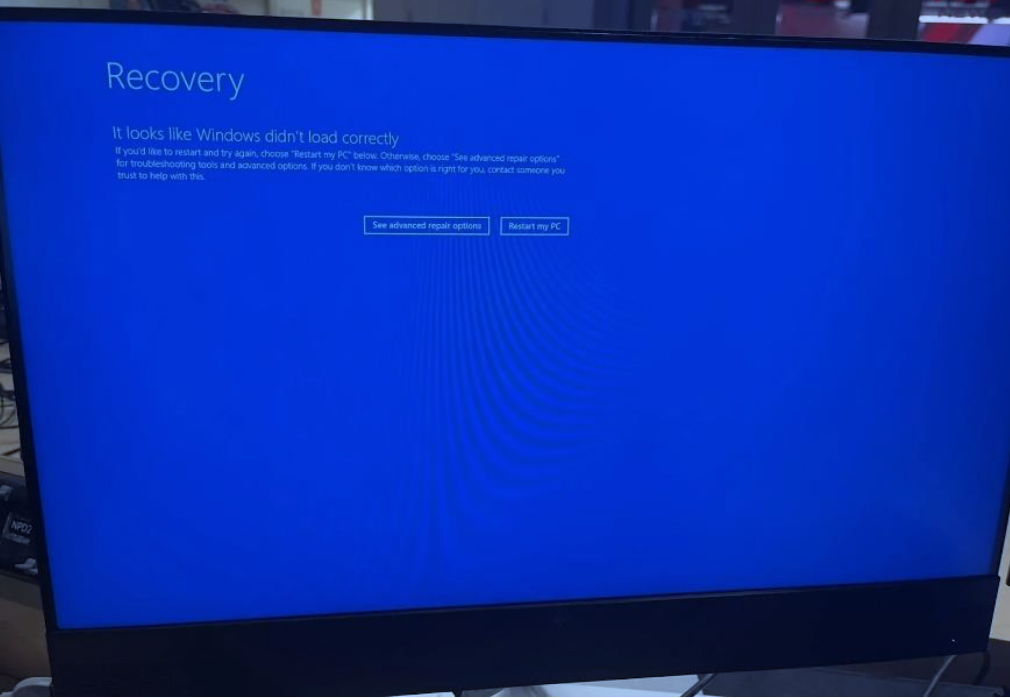
On 19th July 2024, Friday, a critical disruption was unintentionally caused across several infrastructures and organizations by a regular software update from CrowdStrike. The infamous Blue Screen of Death (BSOD), which the update generated, rendered many systems unusable. Although not initially categorized as a cybersecurity incident, the occurrence serves as a reminder of how fragile digital security is and how easily disruptions like this may turn into major security risks.
Outage Details
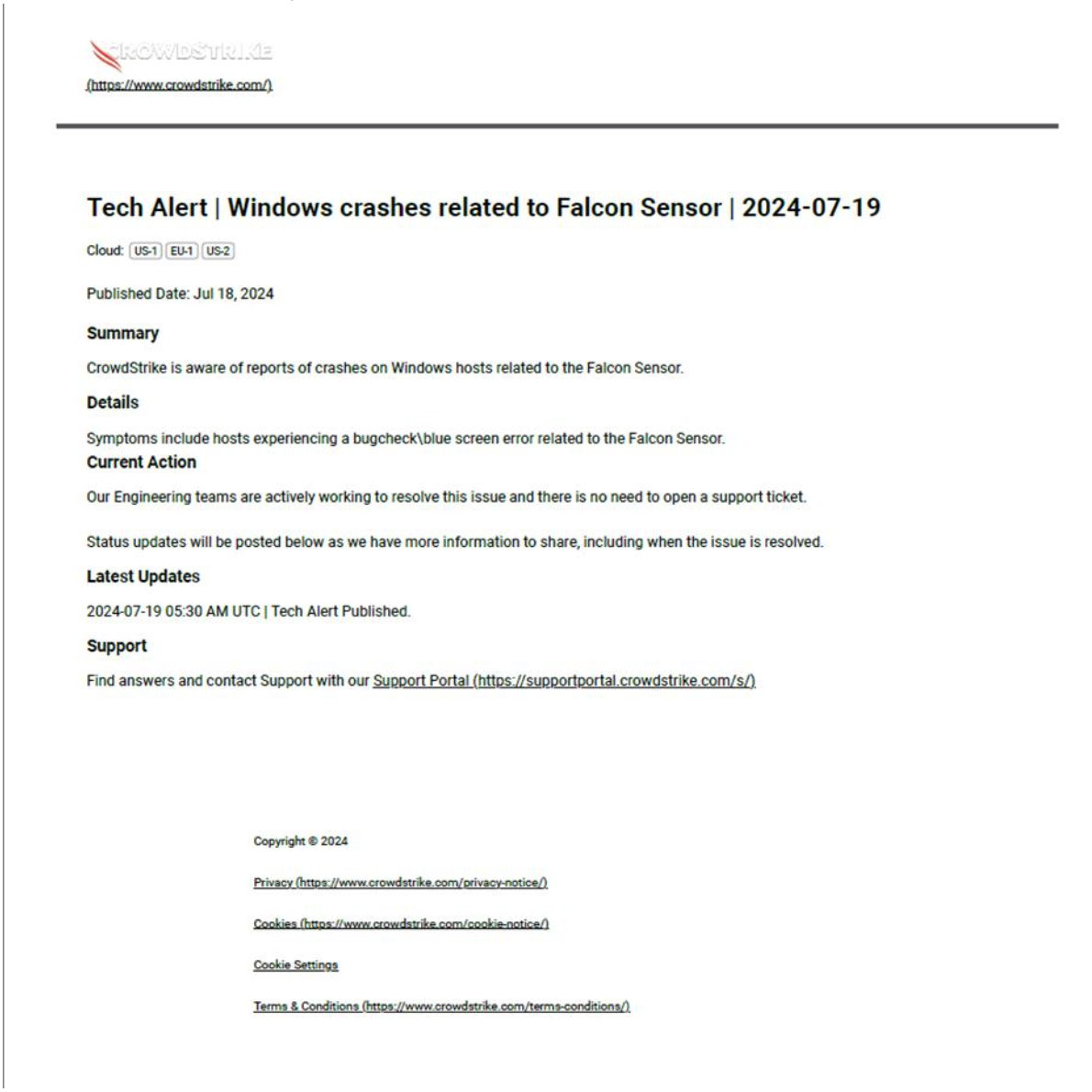
To make sure that its Falcon Sensor devices are safeguarding against the most recent attacks, CrowdStrike releases content updates on a regular basis. Every report indicates that the update is a component of that deployment cycle.
However, some faulty code in the upgrade caused Windows devices to display the feared Blue Screen of Death. The impacted device was unresponsive even after restarting, causing activities at banks, airlines, hospitals, and other organizations to be disrupted and halting thousands of businesses globally.
Because CrowdStrike’s defensive tools are so widely utilized, this error caused several issues. According to a statement from CEO George Kurtz, it wasn’t even a cyberattack.
Remediation
There isn’t a global remedy available right now to bulk execute the suggested script. The manual cleanup required for each host will result in longer remediation times—weeks as opposed to days or hours.
Customers of CrowdStrike will not be able to download the reverted update file unless they forcefully shut down and reboot their systems. The following workarounds are advised if the system crashes repeatedly.
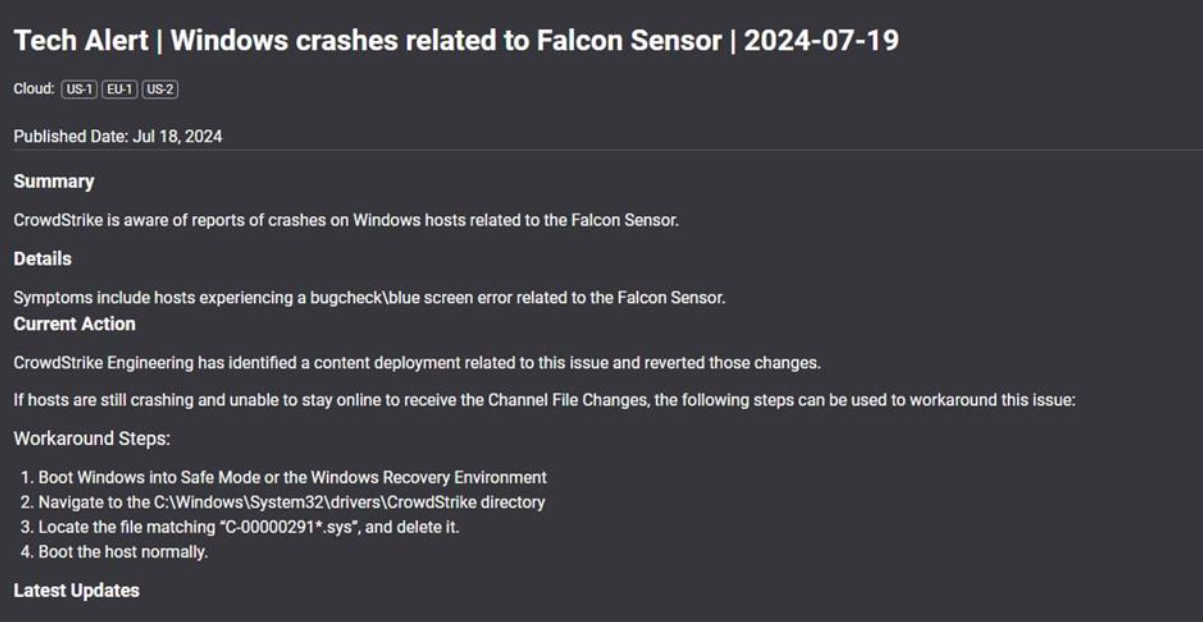
- Boot Windows into Safe Mode or the Windows Recovery Environment
- Navigate to the C:\Windows\System32\drivers\CrowdStrike directory
- Locate the file matching “C-00000291*.sys” and delete it
- Boot the host normally
Exploitation of the outage:
Sadly, the disruption brought about by CrowdStrike has made room for malicious threat actors. Cybercriminals have quickly taken advantage of the situation by posing as remedies to the BSOD issue and setting up phishing pages and fraud domains. For example, under the pretense of offering a patch, one rogue domain sent users to payment pages demanding cryptocurrencies like Bitcoin and Ethereum.
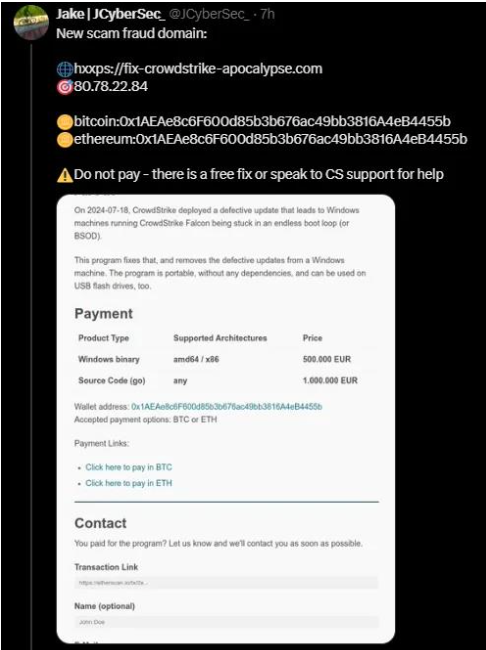
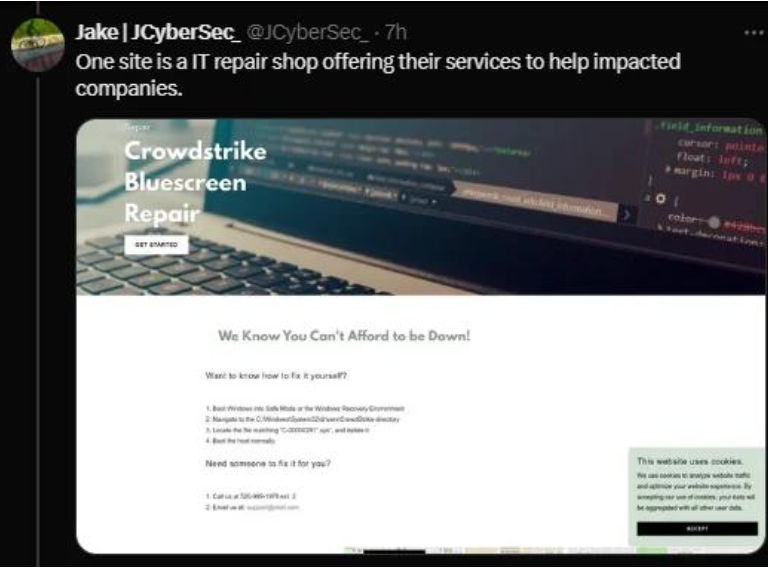
There is now another domain that claims to provide support services to organizations impacted by the problem. It is urged to proceed cautiously as these statements may be deceptive and present further security risks.
Recommendations:
This incident serves as a clear warning of the risks involved in updating systems and the significance of maintaining cybersecurity awareness. Organizations ought to:
- Make sure all communications are verified by confirming they originate from authorized sources. Following the update, there can be a rise in phishing attempts as attackers pretend to be CrowdStrike or other reliable organizations.
- Make use of reliable services to confirm the security of different websites and URLs, particularly those that promise to provide assistance or cures for current problems.
- Inform staff members about the dangers of phishing and the significance of confirming the legitimacy of requests for access or information.
IOCs
crowdstrike-helpdesk[.]com
crowdstrikebluescreen[.]com
crowdstrike-bsod[.]com
crowdstrikedown[.]site
crowdstrike0day[.]com
crowdstrikedoomsday[.]com
crowdstrikefix[.]com
crashstrike[.]com
crowdstriketoken[.]com
fix-crowdstrike-bsod[.]com
bsodsm8rLIxamzgjedu[.]com
crowdstrikebsodfix[.]blob[.]core[.]windows[.]net
crowdstrikecommuication[.]app
fix-crowdstrike-apocalypse[.]com
crowdstrikeoutage[.]info
clownstrike[.]co[.]uk
whatiscrowdstrike[.]com
clownstrike[.]co
microsoftcrowdstrike[.]com
crowdfalcon-immed-update[.]com
crowdstuck[.]org
failstrike[.]com
winsstrike[.]com
crowdpass[.]
supportfalconcrowdstrikel[.]com
crowdstrikehealthcare[.]com
crowdstrikeclaim[.]com
crowdstrikebug[.]com
crowdstrikeupdate[.]com
crowdstrikefail[.]com
crowdstrikeoopsie[.]com
crowdstrike[.]fail
crowdstrike[.]woccpa[.]com
crowdstrikereport[.]com
crowdstrikefix[.]zip
crowdstrike-cloudtrail-storage-bb-126d5e[.]s3[.]us-west-1[.]amazonaws[.]com
hoo[.]be/crowdstrike
crowdstrike[.]orora[.]group
supportportal.crowdstrike[.]com/s/login/?mkt_tok=MjgxLU9CUS0yNjYAAAGUa2XCfb6M3jra…
sinkhole-d845c7b471d9adc14942f95105d5ffcf.crowdstrikeupdate[.]com
crowdstrike[.]okta[.]com/app/coupa/exkqmsghe0qkvea070x7/sso/saml
crowdstrike-falcon[.]online
crowdstrikerecovery1[.]blob[.]core[.]windows[.]net
crowdstrikeoutage[.]com
sedo[.]com/search/details/?partnerid=324561&language=es&domain=crowdstrike[.]es&ori…
supportportal[.]crowdstrike[.]com
isitcrowdstrike[.]com
crowdstrike[.]black
crowdstrikefix[.]zip