CVE-2024-4985: GitHub Enterprise Server Authentication Bypass Vulnerability

GitHub Enterprise Server is a self-hosted platform that facilitates software development, scaling, and delivery for enterprises. For businesses needing greater control and scalability for their code repositories, GitHub Enterprise Server provides security, dependability, cloud computing, and third-party support.
GitHub Enterprise Server operates within your infrastructure and adheres to access and security measures defined by you, including firewalls, network policies, IAM, monitoring, and VPNs. It is particularly well-suited for enterprise use cases subject to regulatory compliance, mitigating potential challenges associated with public cloud-based development platforms.
The GitHub Enterprise Server (GHES) has a critical vulnerability with the highest severity rating. The flaw, being tracked as CVE-2024-4985, can let an attacker gain unauthorized access to the server.
CVE-2024-4985
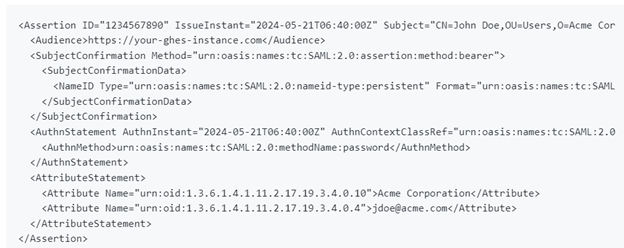
The servers that use the optional encrypted assertions feature with SAML single sign-on (SSO) authentication are affected by the vulnerability.
The vendor notifies that by default, the encrypted assertions are not enabled. Servers that employ SAML SSO authentication without encrypted assertions or those that do not use SAML single sign-on (SSO) are not affected by the vulnerability.
An attacker might configure a SAML response to grant access to a user who has administrator rights or to obtain access itself.
By encrypting the messages the SAML identity provider (IdP) sends during authentication, encrypted assertions enable site managers to increase the security of a GHES instance with SAML SSO.
Impact
Instances of GitHub Enterprise Server with encrypted assertions set for SAML SSO are specifically impacted by CVE-2024-4985.
Since this option is not standard, the only installations that are at risk are those that have enabled this functionality. This issue does not affect you if encrypted SAML assertions are not used in your GHES deployment.
For individuals who are impacted, this vulnerability could have a significant effect.
Exploitation poses serious dangers to the organization’s security and integrity since it can result in the loss of private source code, breaches of private information, and severe interruptions to development processes.
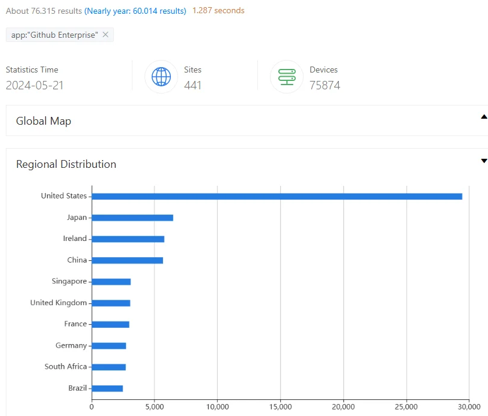
ZoomEye search yielded approximately 76,000 potentially vulnerable GHES instances, mostly in Ireland, Japan, and the United States, indicating a large potential attack surface.
Affected Versions
| GHES version | Fixed in |
| 3.12.3 and earlier | 3.12.4 |
| 3.11.9 and earlier | 3.11.10 |
| 3.10.11 and earlier | 3.10.12 |
| 3.9.14 and earlier | 3.9.15 |
| 3.8 and earlier | No fix available |
Recommendation
GitHub has quickly made patches available to fix CVE-2024-4985. Important modifications have been made to the GitHub Enterprise Server versions listed below:
- 3.9.15
- 3.10.12
- 3.11.10
- 3.12.4
It is highly recommended that administrators implement these patches right away in order to protect their systems from this vulnerability.
Updating your software is an essential part of keeping your company’s security posture strong. CVE-2024-4985 affects all versions of GitHub Enterprise Server prior to 3.13.0, and has been fixed in versions 3.9.15, 3.10.12, 3.11.10 and 3.12.4.