DNS Tunneling and Countermeasures in an Enterprise

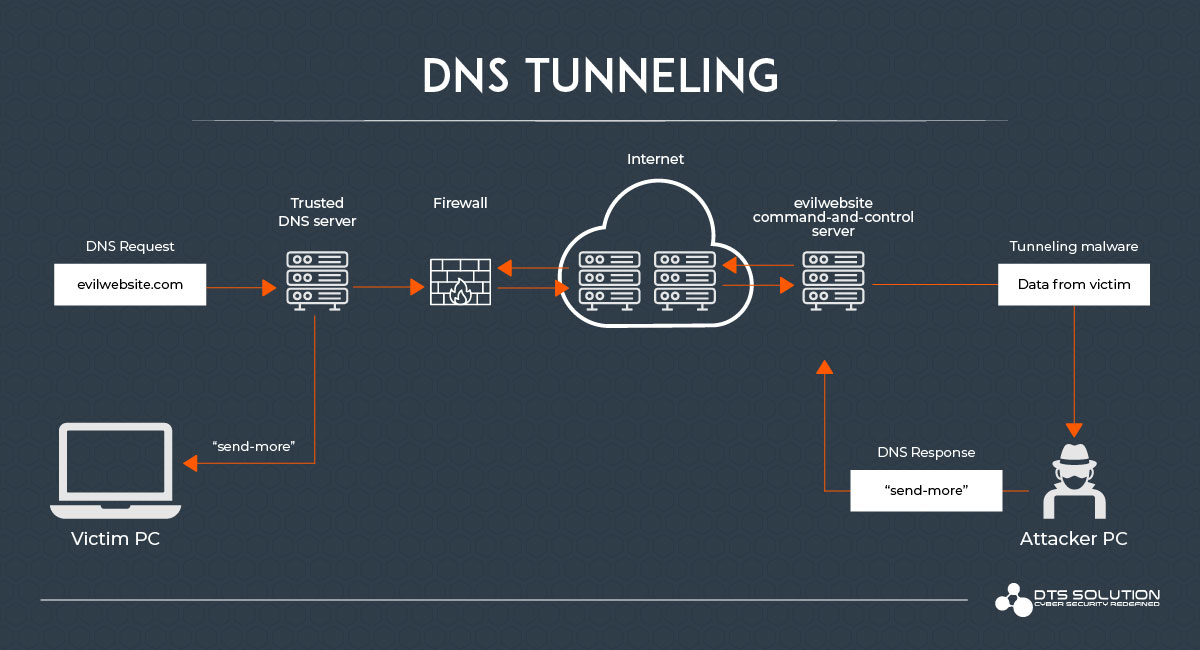
DNS tunneling is one of the significant threats that an organization faces when it comes to attacker tactics and techniques used to exfiltrate data out of the organization.
This attack manipulates the domain name protocol to breach security gateways, exfiltrating sensitive information out of the organization in an undetected manner that would ordinarily be blocked by NGFW and Secure Web Gateway / Proxies.
DNS tunneling also refers to the use of DNS protocol, to perform an attack or data breach. In the tunneling process, malicious DNS requests are used to send covert commands to the C&C server. Once the footprint is established sensitive data can be exfiltrated over DNS tunneling.
DNS protocol was merely designed to search for IP addresses from domain names and can pose a security challenge when it is misconfigured or misused. Over the number of years, we have seen a raft of security vulnerabilities and attacks targeting DNS infrastructure.
DNS tunneling allows cybercriminals to install malware or transfer stolen data into DNS queries, establishing a covert communication route that penetrates most firewalls if not configured properly.
Many known APT groups have used trojans and malware that install DNS tunneling libraries and executables to exfiltrate sensitive data. These DNS tunneling techniques come in various formats with an extended list of toolkits being available for attackers to leverage.
How is DNS tunneling a threat to enterprises
Most enterprises focus on web or email traffic which constantly undergoes attacks. Since DNS has no part in data transfer it often leads to enterprises ignoring its vulnerability to data exfiltration and malicious communications. DNS is therefore prone to misuse.
DNS is commonly used in every enterprise because users need to find their resources and applications, making DNS traffic a trusted protocol, which is a misconception.
DNS-based C2C malware was one of the six most dangerous new attacks discovered in 2012. DNS tunneling attacks were made easy due to the availability of DNS tunneling toolkits making it possible for amateurs to breach an enterprise’s network and infrastructure security solutions and steal data. NGFW and Web Proxy controls were also not very mature in handling DNS tunneling and misuse of DNS (in)security issues.
DNS tunneling attacks may give attackers a backdoor channel through which to exfiltrate stolen data. DNS provides a hidden method of communication that enables attackers to avoid firewall detection.
The DNS tunnel may be utilized as a complete control channel for an already compromised host inside an organization. This enables cybercriminals to download malicious code, steal data from organizations, and get total remote access to systems, among other things.
How can you detect DNS tunneling?
Malware that uses DNS tunneling methods to carry command and control connections and channels can be detected and identified. There are two categories of detection techniques.
- Payload Analysis
- Traffic Analysis
Payload Analysis:
Size and request-response
This technique includes identifying suspicious traffic by using a ratio of source and destination bytes. Tunneling attackers tend to put maximum data into requests and responses leading to long labels, up to 63 characters, or long names up to 255 characters. It is recommended to look into hostnames longer than 52 characters.
Entropy of hostnames
Original DNS names have authentic meanings to them while encoded names have higher entropy.
Statistical analysis
Analysis of the percentage of the longest meaningful substring’s length is a character-based technique. It is recommended to look into anything containing over 27 unique characters. Character frequency analysis and repeated consonants or numbers can also signal to DNS tunneling.
Unusual record types
Records that are not used by the targeted typical client are also a detection technique.
Traffic Analysis:
The volume of DNS traffic per IP address
Look for DNS traffic created by one client’s IP address. Tunneled data is restricted to 512 bytes per request hence the attacker need to create a large number of requests.
DNS traffic saturation per domain
A less reliable technique includes tracking the unusual number of requests back to the domain name. Since tunneling can be configured to multiple domain names, this technique isn’t reliable.
Unusual hostnames per domain
DNS tunneling utilities use unusual hostnames for their requests which might all lead to a domain name indicating tunneling.
The geographic location of the DNS server
Receiving unusual DNS traffic from geographical locations that are unknown should be monitored. Organizations will have predefined whitelisted authoritative DNS servers.
Security Controls
NGFW, Secure Web Gateway, SASE, and DNS Firewalls are all cybersecurity solutions that have DNS tunneling detection capabilities through signature detection and DNS deep packet inspection capabilities.
DNS Tunneling Utilities
Attackers may use any of the following DNS tunneling utilities and is a great way to identify any potential use within your environment using Windows Events or System Logs.
- DeNise
- dns2tcp
- meterpreter
- DNScat
- Heyoka
- Iodine
- NSTX
- OzymanDNS
- psudp
- squeeza
- tcp-over-dns
- Psiphon
- TUNS
- Malware using DNS
How can you prevent DNS tunneling?
Beyond the cybersecurity controls that would be expected within an organization, there are very specific methods to prevent DNS tunneling attacks. Here are a few of our favorite ones.
- Using a DNS malicious domain verification against all DNS requests would be a good start
- Since DNS tunneling relies on sending encoded malicious DNS requests, blocking the suspicious DNS methods can prevent the attack. Such DNS traffic can be monitored by NGFW like Palo alto and Fortinet which monitor the DNS traffic and block malicious activity. Fortinet Threat Intelligence Service FortiGuard is used for signature-based detection of DNS tunneling attacks
- Whitelist your DNS authoritative server on your perimeter firewalls, all other use of DNS protocol should be blocked to non-whitelisted IP addresses
- DNS firewall should be employed which can validate all DNS queries before forwarding unresolved queries to authoritative DNS servers once screening checks are passed
- Analysis of the DNS requests that may seem unusual. Tracking such patterns and blocking them would prevent DNS tunneling.
- Log and monitor DNS queries and response data. There is a need for continuous monitoring. DNS logs can be monitored by SIEM and CSOC.
- DNSSEC, access restrictions, and other architecture upgrades can help protect recursive servers against unauthorized access and modification.
- Enable a real-time DNS solution that identifies suspicious DNS server requests and patterns and performs sink-holing
- Behavioral analytics to identify and block DNS tunnels which can efficiently block DNS tunnels after processing only a few queries. It works by detecting and blocking DNS tunnels using comprehensive behavioral analytics by analyzing the DNS queries pattern.
- Enterprise tools also provide DNS proxy functions. This proxy can be used to protect DNS traffic. The service monitors all traffic that passes through this proxy firewall. These logs are analyzed and forwarded to the DNS tunneling detection engine
- To tackle DNS tunneling for remote users DNS proxy functionality also exists in SASE platforms.
- Deploying machine learning techniques on DNS traffic to detect anomalies in patterns as explained earlier.