Dark Web and Threat Intelligence (DARKINT)

Security researchers and Cybersecurity professionals have an immense interest in discovering threat intelligence on the deep web and darknet. This intelligence allows organizations to detect block and prevent threats of all kinds—But first, we need to know, what exactly is the deep web and the Dark Web?
The Deep Web, also called as the invisible web, includes websites and data sources that are not indexed and unknown by search engines of the surface web. It includes online pages that are restricted by passwords and encrypted networks to create a non-discoverable platform from public. The term deep web is often confused with darknet/Dark Web.
The Dark Web (also called the darknet), is a sub-division of Deep web which is inaccessible through search engines or browsers and requires exceptional authorization to access the sites. The Dark Web is used by people to seek anonymity for various purposes, both illicit and lawful in nature. It offers users total anonymity and are made intentionally hidden from the public. Because of its anonymous nature, we may find a great deal of dreadful activity, including illegal goods selling and buying, and other illicit activities.
Relevancy of Dark Web:
The size of the Dark Web is impossible to measure since majority of the information is hidden or masked from the public such as Cyber Crime, Cyber Espionage, fraud related activities, pirated contents, hacking and illicit forums etc. Since the search engines cannot index the sites, anonymous web pages are inaccessible for the public to show these sites in the search results. We require specific configuration or software to access the Dark Web sites. Moreover, the threat actors’ identities and locations are protected by encryption technology that routes threat actor’s data through many servers across the globe and makes it extremely difficult to identify the real person behind the threat.
Since more and more sites and information are always being added to Deep web, we are not able to compute the size of the Deep Web, and the Dark web also keeps on growing with the exponential growth of Deep web. Accessing Dark Web and finding the hidden websites is comparatively easy, but the challenging part is to specifically query the search for finding the relevant and worthwhile threat intelligence data, that will improve our organization’s security aspect.
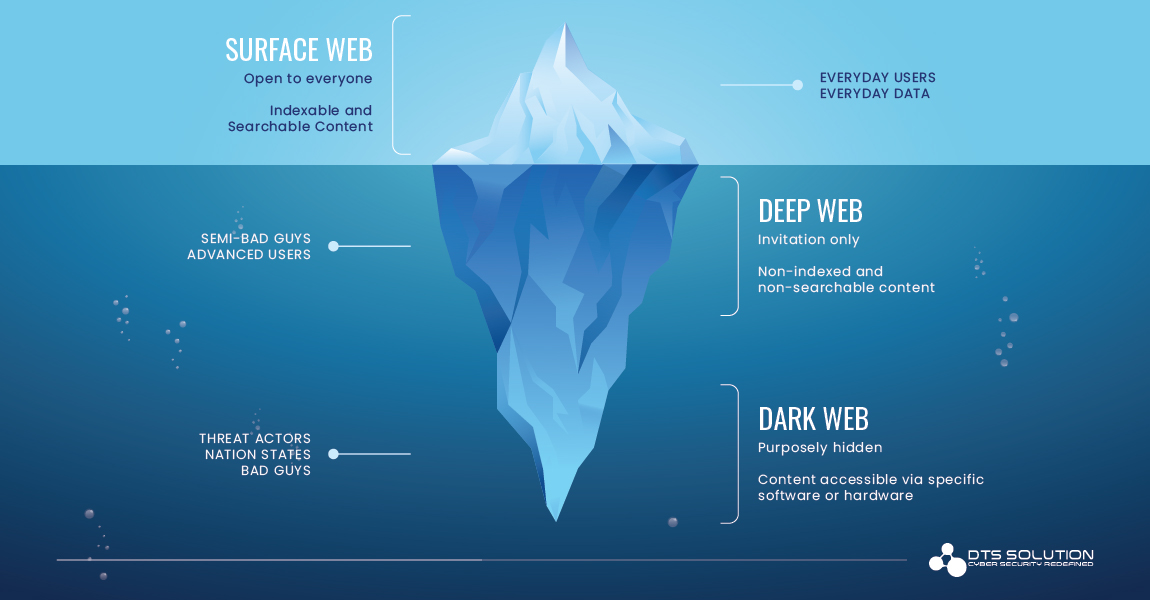
How the Dark Web Threat Intelligence (DARKINT) allows organizations to detect and prevent threats of all kinds?
Having Dark Web as a source for threat intelligence is essential in preventing cybercrimes.
Dark web provides insight to security professionals into the enemy’s mind, allowing them to forecast threats and strengthen their defenses. It’s pretty sure that security investigators will use the Dark Web to obtain highly valuable threat intelligence data. The Data is mostly associated with the potential targets for both organizations and individuals; breached data dumps, including breached personal or company information; forums for the users to anonymously discuss illegal topics, such as how to conduct cyberattacks; how to organize illegal activities etc.
Data collected from Dark Web, are processed, indexed and analyzed and could be disseminated to answer multiple intelligence questions like who, what, where, when, how etc. which helps to identify information that may pose potential harm.
There are many analytic engine tools which helps in collecting vital information from the deepest layers of the internet by automatically and anonymously combs through the entire Dark Web on specific keywords, which helps to identify information and that may pose potential harm. This frequent checking on the Dark Web helps to understand if people are talking about them and what they are saying, and finally making the gathered crucial data from Dark web sources available to the Security Analysts on different sectors.
Knowing what types of exploits are being performed on one’s organization allows the security investigators to prepare for security incident response plan before something happens. For example, a company can search the Dark Web to check if any of their internal IP addresses, credentials, organization sensitive information have been posted. If a data breach/theft happens, it is better to be aware of it and can proactively take actions before it goes to public.
If your organization is breached and sensitive information is stolen, there is a higher chance that it will show up on the Dark Web before you know an attack has taken place.
The Value of Dark Web Sources for Threat Intelligence
Threat Intelligence from Dark Web may be used by organizations for:
- Data validation and data verification can be done in early stages to reduce risks associated with the data
- Identify any data breaches, data leaks, compromised credentials and trade secrets
- Being pro-active against different cyber threats and crimes
- Detection of TTP’s (Techniques Tactics Procedures) used by Attackers
- Detection of exploits, vulnerabilities and other IOC’s (Indicator of Compromise)
- Knowledge about different malwares and tools that Threat Actors use, with their working knowledge, and methods of implementing the attack in typical cases
- Figure out the motivation behind attacks
Potential Barriers and Limitations with Dark Web Intelligence
The extraction of the reliable information from hundreds of thousands of other Dark Web conversations within the Dark Web is a challenge. As a result, it is possible to collect irrelevant/false-positive information rather than receiving benefits. This may lead to loss of resources and time.
Another challenge is that, since the Darknet sites could be present at any part of the world, there may exist illicit forums, dark marketplaces and cyber espionage details in different languages, sometimes even in native languages. This makes it really difficult for the security analysts to understand real threats, targets and their intentions.
Next is due to the anonymous nature of the Dark web, the Dark Web provides only less protection to the external users. Hence, it is easy to infect the machine by clicking any links or collecting/downloading information, since many of the websites are accessible via a Tor Browser which conceals the attacker details and these sites might contain malware or embedded viruses. Therefore, it is recommended to re-image the machine after the Dark Web search.
Finally, a proven discovery tool is essential to efficiently aggregate data across a range of deep web and dark net providers to any threat intelligence strategy. Data sources on the deep and Dark Web are extensive and regularly changing, since having the tools to expose Dark Web dangers and defend against them is a crucial asset for any organizations including healthcare organizations, cyber sectors, government agencies etc.
There is no doubt that threat intelligence gathered from the Dark Web is a clue for the security researchers to know about the motivations, methods and tactics of threat actors, which cannot be obtained through conventional monitoring. For example, say a threat actor turned out to be an insider who was working for the company and stole the sensitive details or the information about their critical assets. By researching across references from the Dark Web for any potential sale of the information, we can prevent or can take actions before the information is sold.
To make the best use of Dark Web intelligence, the security analysts need to be alerted when relevant information emerges and be able to quickly determine whether the extracted information requires further investigation or escalation. Using the intelligence to assess risk in this way will ultimately add an extra layer of assurance in security, mitigating against future fraudulent charges and hence it drives for more efficient decision making.