The ClawdBot Vulnerability: How a Hyped AI Agent Became a Security Liability

Clawdbot, an open-source AI agent gateway that went viral in late January 2026, has emerged as a critical case study in autonomous system security. Security researchers discovered severe misconfigurations affecting hundreds of publicly exposed Clawdbot control servers, granting unauthorized access to sensitive credentials, conversation histories, and complete system control.
ClawdBot entered the market positioned as an autonomous AI agent capable of managing tasks ranging from workflow automation to crypto operations. Its appeal was clear. It promised speed, autonomy, and reduced human involvement. What followed instead was a series of disclosures that exposed deep architectural weaknesses with real-world impact.
The vulnerability stems from authentication bypass conditions created when Clawdbot operates behind misconfigured reverse proxies, transforming localhost trust assumptions into internet-wide exposure.
Clawdbot's Dual-Component Architecture: Gateway and Control Interface
Clawdbot functions as an agent gateway bridging large language models with messaging platforms and local system capabilities. The architecture comprises two critical components:
Clawdbot Gateway handles message routing, LLM inference calls, credential management, and tool execution as a persistent service behind reverse proxies like Nginx or Caddy.
Clawdbot Control provides the web-based administrative interface for configuring integrations, approving devices, and managing API keys, effectively centralizing all agent capabilities behind a single control plane.
Unlike standard web applications, Clawdbot requires extensive system permissions. The agent must read private messages across multiple platforms, store authentication tokens, execute shell commands, maintain persistent state, and autonomously initiate actions without explicit prompts. This architecture concentrates high-value capabilities within a single attack surface where exposure enables identity compromise, command execution, and perception manipulation beyond simple data theft.
Authentication Bypass via Misconfigured Reverse Proxy Localhost Trust
The vulnerability manifests through a specific misconfiguration in Clawdbot’s authentication mechanism. While implementing cryptographic device authentication via challenge-response protocols, it includes default behavior that auto-approves connections from localhost (127.0.0.1).
When Clawdbot deploys behind a reverse proxy on the same server. a standard production pattern, all external traffic forwarded to the gateway appears to originate from the loopback interface. The critical failure occurs when gateway.trustedProxies configuration remains empty. Without explicit proxy configuration, the gateway ignores X-Forwarded-For headers and uses only socket addresses:
- External request reaches reverse proxy
- Proxy forwards to Clawdbot on localhost
- Clawdbot identifies connection as 127.0.0.1
- Auto-approval bypasses authentication
- Attacker gains full control plane access
This represents fundamental misconfiguration rather than zero-day exploitation.
Over 1,000 Exposed Instances: Credentials, Conversations, and Root Access Compromised
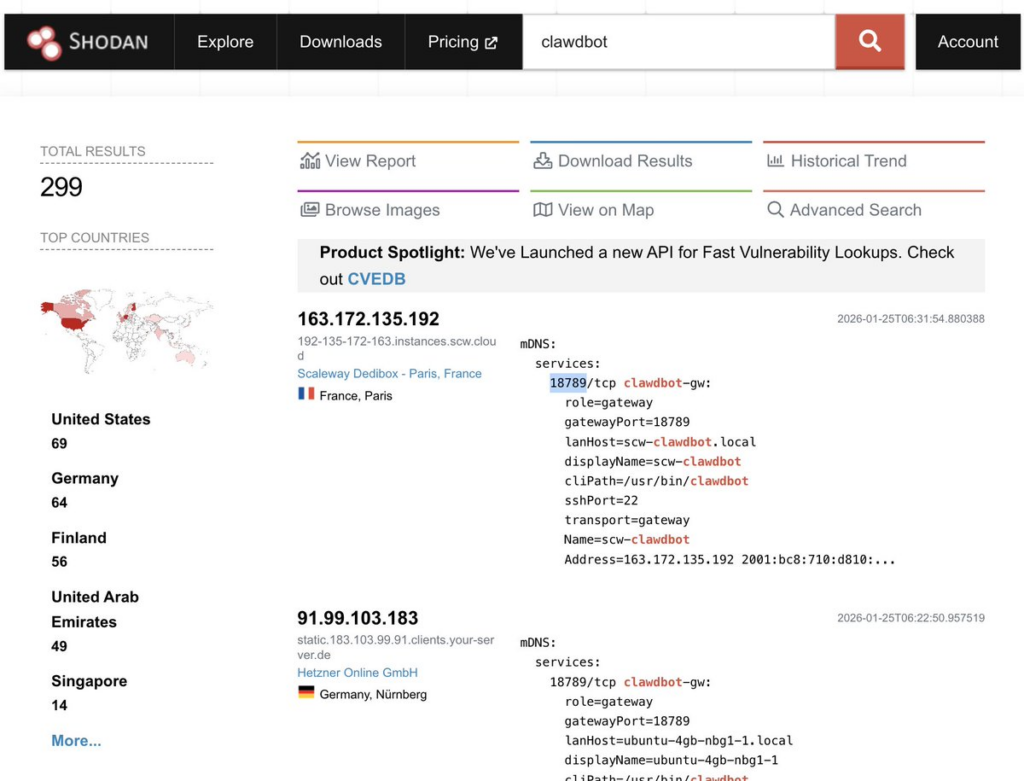
Security researcher Jamieson O’Reilly documented exposure scale through internet-wide scanning. Using Shodan, he identified Clawdbot control servers via distinctive HTTP fingerprints including unique HTML strings and static assets, revealing over 1,000 exposed gateways.
Compromised instances exposed multiple data categories:
Configuration Dumps: Anthropic API keys, Telegram bot tokens, Slack OAuth secrets, signing keys, device-pairing metadata.
Conversation Archives: Months of private messages across Signal, Telegram, Slack, Discord, WhatsApp with attachments and media files.
Credential Repositories: API keys for integrated services, OAuth tokens, session identifiers in network-accessible locations.
Execution Access: Unauthenticated command execution on host systems, with several instances running root privileges without separation.
A particularly severe case involved Signal integration where pairing credentials resided in globally readable temporary files, enabling complete account takeover by bypassing end-to-end encryption through endpoint compromise.
Six-Phase Attack Chain: From Shodan Discovery to System Compromise
The exploitation requires minimal sophistication:
Discovery: Shodan searches for “Clawdbot Control” return hundreds of results within seconds.
Access: Misconfigured gateways load admin interfaces without authentication, completing WebSocket handshakes for full control.
Credential Extraction: Configuration files contain plaintext credentials for Anthropic Claude API, Telegram, Slack, Discord, WhatsApp Business.
Data Exfiltration: Complete conversation histories with private messages, files, voice content, behavioral patterns.
Identity Takeover: Control plane access enables impersonating operators, injecting malicious commands, modifying AI responses, exfiltrating data through legitimate-appearing integrations.
System Compromise: Command execution capabilities permit shell access, backdoor installation, network pivoting, agent modification.
Active Exploitation: Cryptocurrency Theft Campaigns
Blockchain security firm SlowMist identified active campaigns targeting cryptocurrency users through exposed Clawdbot instances. Attackers employ prompt injection via email and messaging to exfiltrate wallet private keys, seed phrases, exchange API credentials while monitoring transaction patterns through conversation histories. These campaigns align with broader targeting patterns against AI infrastructure observed in recent weeks.
The agent’s autonomous behavior amplifies attack surfaces, operating continuously enables injected commands to execute without user interaction, creating persistent AI-driven backdoors.
Why AI Agents Break Traditional Security Models
Clawdbot exposes fundamental tensions in autonomous agent design:
Least Privilege Violation: Broad access requirements across messaging, credentials, command execution conflict with restriction principles.
Sandboxing Breakdown: Cross-platform operation violates isolation assumptions.
Credential Concentration: Centralized stores create single points of failure exposing multiple service tokens.
Perception Layer Attacks: Beyond confidentiality, integrity, availability—agents enable cognitive manipulation through selective filtering or response modification without triggering traditional detection.
These represent inherent architectural trade-offs rather than patchable bugs.
Remediation and Hardening
Organizations must implement immediate controls:
Configuration: Set gateway.auth.password, configure gateway.trustedProxies explicitly, implement IP whitelisting, employ network segmentation.
Access Control: Require MFA for control plane access, implement RBAC, use separate credentials per platform, rotate keys regularly.
Credential Management: Deploy dedicated secrets management systems (supporting major secrets vaults and authentication platforms), encrypt stores at rest, implement least-privilege scopes.
Network Security: Properly configure reverse proxies, enforce TLS, implement rate limiting, block direct internet access.
Monitoring: Comprehensive detection requires identifying unauthorized access, unusual API patterns, unexpected commands, anomalous messaging. Organizations should implement continuous monitoring across all agent touchpoints to detect compromise indicators including API abuse patterns and credential theft attempts.
Detection Methodology
Security teams should implement:
Scanning: Use Shodan/Censys to inventory exposed instances via HTML fingerprints.
Log Analysis: Review proxy logs for suspicious source IPs, geographic anomalies, timing patterns.
API Monitoring: Track usage across platforms for unexpected addresses, time patterns, rate anomalies.
Behavioral Analysis: Monitor message timing, content patterns, recipient lists for deviations.
System Indicators: Track processes, filesystem modifications, network connections for compromise signs.
Broader Security Implications
The incident represents a critical inflection point. Autonomous agents violate traditional security assumptions:
- Operate continuously across domains without explicit interaction
- Consolidate diverse capabilities requiring concentrated credentials
- Enable perception manipulation creating cognitive-layer attacks
- Provide immediate high-value access without establishing persistence
Organizations must recognize AI agents as privileged infrastructure comparable to identity providers or secrets management requiring corresponding controls, monitoring, governance. The alternative: widespread compromise as adoption accelerates without security maturity.
Conclusion
Clawdbot’s vulnerabilities reflect collision between powerful capabilities and security models designed for different paradigms. The lesson: treat autonomous agents as critical infrastructure requiring security-by-default configurations, proper authentication, comprehensive monitoring, secrets integration, regular audits, incident planning.
Organizations should approach deployment with rigor matching identity systems or privileged access platforms. For comprehensive monitoring across emerging attack vectors, managed security operations capabilities designed for modern attack surfaces provide essential visibility into autonomous system threats.
The age of autonomous computing has arrived. Security frameworks must evolve before major breaches make urgency undeniable.