React2Shell Vulnerability Exposed: Breaking Down CVE-2025-55182’s Critical RCE Attack Chain

On December 3, 2025, the React development community faced one of its most severe security incidents: React2Shell (CVE-2025-55182). With a maximum CVSS score of 10.0, this vulnerability exposed React Server Components to remote code execution attacks through a critical deserialization flaw in the React Flight protocol. Within hours of disclosure, multiple threat actor groups, including Chinese state-sponsored operations, began actively exploiting vulnerable servers.
Technical Overview of CVE-2025-55182
The vulnerability stems from improper deserialization handling in React’s Flight protocol—the binary serialization mechanism that enables data transfer between server and client in React Server Components. The flaw exists across three npm packages: react-server-dom-webpack, react-server-dom-turbopack, and react-server-dom-parcel in React versions 19.0.0 through 19.2.0.
React Flight Protocol Architecture
React Flight operates as a line-based format for serializing component trees into compact, streamable chunks. Each chunk follows the format ID:TYPE?JSON, allowing progressive streaming of promises and server-side data. This protocol enables React Server Components to:
- Execute database queries on the server without exposing credentials
- Stream component trees incrementally as data becomes available
- Serialize non-JSON values like functions and blobs
- Maintain references between chunks using internal tokens
While these capabilities enhance performance, they also created the attack surface that React2Shell exploits.
Attack Vector Anatomy
The exploit leverages prototype chain walking through React’s requireModule function, which resolves module exports without implementing proper hasOwnProperty validation. Attackers craft malicious Flight payloads that inject fake Promise objects, hijack internal resolution mechanisms, and ultimately invoke the Function() constructor with attacker-controlled code.
Exploitation Mechanics
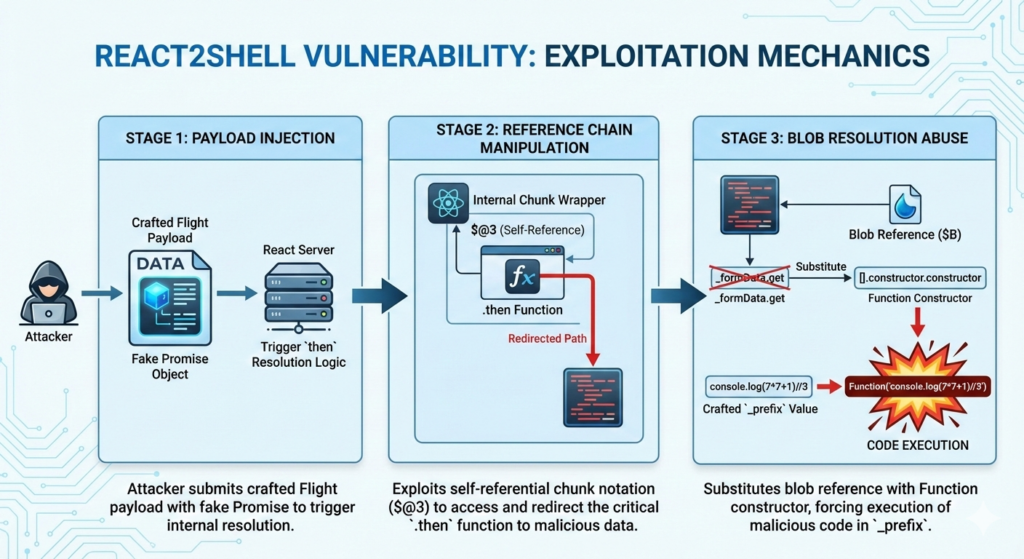
The proof of concept demonstrates a multi-stage attack chain:
Stage 1: Payload Injection The attacker submits a crafted Flight payload containing a fake Promise object shaped to trigger React’s internal then resolution logic. The payload structure includes status flags, response references, and value strings that mimic legitimate React chunks.
Stage 2: Reference Chain Manipulation By exploiting self-referential chunk notation ($@3), the attacker accesses React’s internal chunk wrapper objects. These wrappers contain the critical .then function used during promise resolution, which the exploit redirects to process malicious data.
Stage 3: Blob Resolution Abuse React Flight uses blob references (prefixed with $B) to handle non-serializable values. The exploit substitutes _formData.get with [].constructor.constructor—effectively creating a reference to the Function constructor. Combined with a crafted _prefix value containing executable code, this forces React to invoke:
Function(‘console.log(7*7+1)//3’)
The trailing comment prevents syntax errors from the appended blob ID, enabling clean code execution. This technique bypasses normal security boundaries by manipulating internal object properties during deserialization.
Active Exploitation Campaigns
Multiple coordinated campaigns have weaponized CVE-2025-55182 within 72 hours of disclosure. Google Threat Intelligence identified at least five Chinese state-sponsored groups deploying specialized payloads:
- UNC6600: Deploys MINOCAT tunneling utility for network pivoting
- UNC6586: Distributes SNOWLIGHT downloader with encrypted C2 channels
- UNC6588: Installs COMPOOD backdoor for persistent access
- UNC6603: Delivers updated HISONIC backdoor using Cloudflare Pages and GitLab for covert C2
- UNC6595: Deploys Linux-compiled ANGRYREBEL (Noodle RAT) for cross-platform operations
Threat hunting telemetry shows attackers establishing reverse shells to known Cobalt Strike infrastructure, then deploying remote monitoring tools like MeshAgent to maintain persistence. Subsequent activities include modifying SSH authorized_keys files, enabling root login, and harvesting cloud credentials from Azure IMDS endpoints, AWS metadata services, and GCP instance data.
Malware Deployment Patterns
Post-exploitation activities reveal sophisticated operational tradecraft. Threat actors deploy credential harvesting tools including TruffleHog and Gitleaks to extract secrets from repositories. Custom scripts target multiple secret types:
- Environment configuration files (.env, .env.local, .env.production)
- SSH private keys (~/.ssh/id_rsa, /root/.ssh/*)
- Cloud provider credentials (~/.aws/credentials, ~/.docker/config.json)
- Git authentication tokens (~/.git-credentials)
- System shadow files (/etc/shadow, /etc/passwd)
Microsoft Defender teams observed attempts to harvest OpenAI API keys, Databricks tokens, and Kubernetes service account credentials. Attackers used Azure CLI and Azure Developer CLI to obtain authentication tokens for lateral cloud infrastructure movement.
KSwapDoor and ZnDoor: Advanced Linux Backdoors
Palo Alto Networks Unit 42 identified KSwapDoor, a professionally engineered remote access tool delivered via React2Shell exploitation. This malware creates internal mesh networks allowing compromised servers to communicate peer-to-peer, evading security monitoring. Malware protection systems must account for KSwapDoor’s unique characteristics:
- Military-grade encryption for C2 communications
- Sleeper mode activation via covert network signals
- Kernel swap daemon impersonation for host persistence
- Interactive shell capabilities with file operation support
- Lateral movement scanning for network reconnaissance
NTT Security documented ZnDoor distribution to Japanese organizations, with attack chains executing bash commands to fetch payloads from 45.76.155[.]14. ZnDoor provides SOCKS5 proxy functionality, port forwarding, and comprehensive file system manipulation, indicating long-term infrastructure compromise objectives.
Companion Vulnerabilities
Beyond CVE-2025-55182, two additional security issues compound the React Server Components attack surface:
CVE-2025-66478 (Next.js) This duplicate vulnerability in Next.js App Router enables identical exploitation paths through similar deserialization flaws. Next.js versions 15.x and 16.x, along with canary releases from 14.3.0-canary.77 onward, inherited the underlying React Flight protocol weakness.
Denial of Service Vector Recursive then chaining triggers stack overflow conditions, causing server crashes through memory exhaustion. This provides an alternative disruption method for threat actors unable to achieve RCE.
Secret Exposure Path Manipulation of React’s internal structures can leak server-side environment variables and private configuration data, even without achieving full code execution.
Impact Assessment and Exposure
The Shadowserver Foundation tracks over 111,000 vulnerable IP addresses globally, with concentrated exposures in:
- United States: 77,800 instances
- Germany: 7,500 instances
- France: 4,000 instances
- India: 2,300 instances
GreyNoise Intelligence identifies 547 malicious IP addresses actively scanning for vulnerable endpoints across 24-hour monitoring windows. These scanning operations originate primarily from infrastructure in the United States, India, United Kingdom, Singapore, and the Netherlands.
Any production application using React Server Components faces exploitation risk, including:
- Next.js applications with App Router enabled
- Redwood framework deployments
- Waku implementations
- Custom RSC configurations using affected packages
Even applications not explicitly implementing Server Functions remain vulnerable if RSC support exists in the build chain.
Emergency Patching Requirements
CVE-2025-55182 represents a critical inflection point for React Server Components security. With maximum severity, active exploitation by sophisticated threat actors, and over 100,000 potentially vulnerable internet-facing applications, immediate action is imperative.
The vulnerability demonstrates how modern application architectures create new execution surfaces that traditional security tooling was not built to observe.
Patching closes the immediate door. Detection closes the gap attackers rely on after they get inside.
Security teams that treat application runtimes as monitored, controlled execution environments will contain this class of attack faster than those who rely on static assumptions.
Conclusion
CVE-2025-55182 represents a critical inflection point for React Server Components security. With maximum severity, active exploitation by sophisticated threat actors, and over 100,000 potentially vulnerable internet-facing applications, immediate action is imperative.
The vulnerability demonstrates how modern application architectures create new execution surfaces that traditional security tooling was not built to observe.
Patching closes the immediate door. Detection closes the gap attackers rely on after they get inside.
Security teams that treat application runtimes as monitored, controlled execution environments will contain this class of attack faster than those who rely on static assumptions.