Detecting ADCS Privilege Escalation: How Misconfigured Certificates Expose Active Directory

Active Directory Certificate Services (AD CS) is Microsoft’s system for managing digital certificates in enterprise networks. It provides encryption, digital signing, and secure authentication, all integrated directly with Active Directory.
While AD CS strengthens security, misconfigurations in certificate authorities and templates often open the door to abuse. Weak settings can allow attackers to request certificates for accounts they should not control, impersonate privileged users, and maintain long-term access without detection.
This combination of usefulness and risk makes AD CS both a critical security tool and a frequent target for attackers seeking persistence and privilege escalation inside corporate networks.
The Core Problem
ADCS misconfigurations allow attackers to request certificates for privileged accounts, effectively bypassing traditional password-based security controls. Once an authentication certificate is issued, it can be used to authenticate as the subject identity until revocation or expiration – making password resets ineffective against such attacks.
The problem stems from certificate templates that combine dangerous settings: authentication-based Extended Key Usages (EKUs) with insufficient enrollment restrictions. When these templates allow subject name modification or lack proper approval workflows, they become pathways for privilege escalation.
Primary Attack Vectors
ESC1: Subject Alternative Name Manipulation
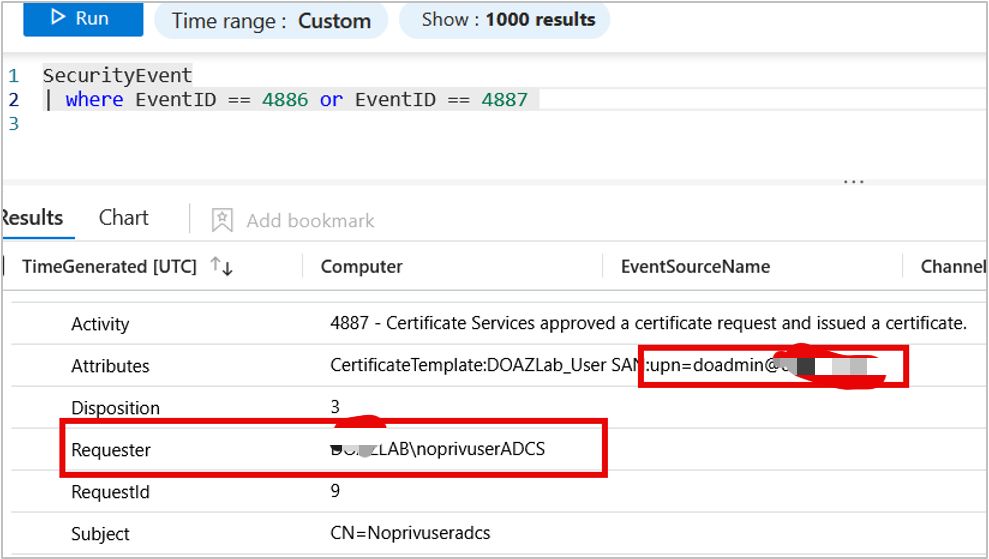
ESC1 attacks exploit certificate templates with the CT_FLAG_ENROLLEE_SUPPLIES_SUBJECT flag enabled. This configuration allows certificate requestors to specify their own Subject Alternative Name (SAN), essentially impersonating any domain user, including administrators.
The attack requires:
- A certificate template with client authentication EKU
- The “Supply in request” setting enabled
- Enrollment permissions for low-privileged users
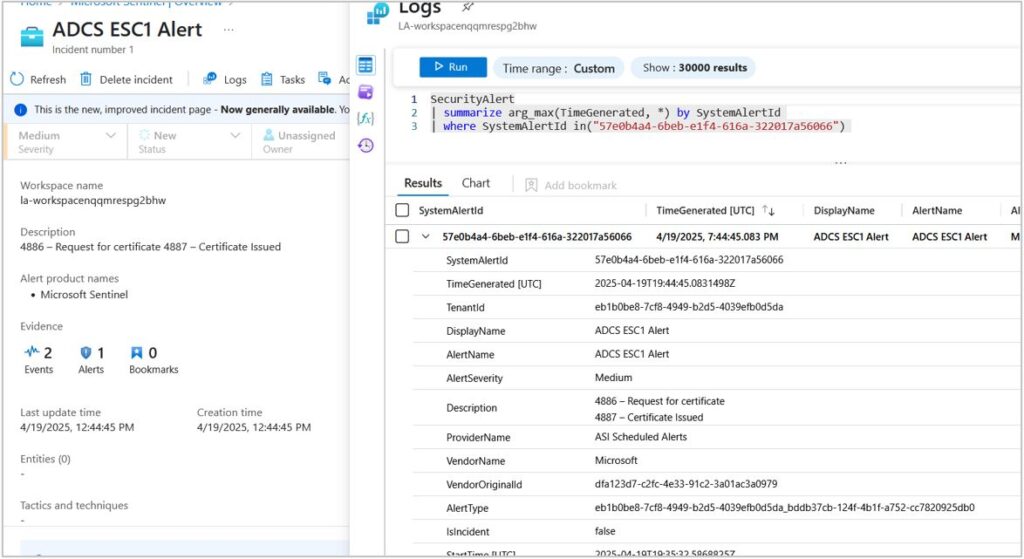
Detection focuses on monitoring Event IDs 4886 (certificate request) and 4887 (certificate issued), specifically looking for mismatches between the requestor and certificate subject.
ESC2/ESC3: Certificate Request Agent Abuse
ESC2 vulnerabilities involve templates with “Any Purpose” EKU or no EKU restrictions, while ESC3 exploits Certificate Request Agent permissions. ESC3 requires a two-stage attack: first obtaining an enrollment agent certificate, then using it to request certificates on behalf of other users.
These attacks demonstrate how certificate templates with overly permissive EKU settings can be chained together for privilege escalation. The Certificate Request Agent EKU (1.3.6.1.4.1.311.20.2.1) grants powerful permissions that should be restricted to administrative accounts only.
ESC4: Template Access Control Weaknesses
ESC4 targets write permissions on certificate template objects in Active Directory. Attackers with GenericWrite or similar permissions can modify template properties to introduce vulnerabilities, request certificates using the modified template, then restore the original configuration.
This attack highlights the importance of auditing Active Directory permissions on PKI objects, not just the templates themselves.
ESC8: NTLM Relay to Web Enrollment
ESC8 leverages NTLM relay attacks against ADCS web enrollment endpoints. Attackers relay authentication to HTTP-based certificate services, obtaining certificates for the relayed accounts. This attack vector has proven particularly effective when combined with techniques like PetitPotam for forcing authentication.
The vulnerability exists because many ADCS deployments enable HTTP endpoints without proper authentication hardening, allowing NTLM relay attacks to succeed.
Advanced Certificate Mapping Attacks
ESC9 and ESC10: Weak Certificate Mappings
Modern attacks like ESC9 and ESC10 exploit weak certificate mapping configurations introduced after Microsoft’s attempts to patch CVE-2022-26923 (Certifried). These attacks manipulate user principal names (UPN) or DNS hostnames on accounts with GenericWrite privileges, then request certificates that the domain controller maps incorrectly.
Key registry settings affect these attacks:
- StrongCertificateBindingEnforcement (KDC service)
- CertificateMappingMethods (Schannel provider)
When these settings allow weak mappings, attackers can impersonate high-privilege accounts by temporarily modifying target account attributes.
Detection and Monitoring Strategies
Effective ADCS security requires comprehensive logging and monitoring. Organizations must enable Certificate Services auditing through the CA properties interface, as auditing is disabled by default.
Critical events to monitor include:
- Event ID 4886/4887: Certificate request and issuance
- Event ID 4899/4900: Template modifications
- Event ID 39/41: Certificate request errors (post-KB5014754)
SIEM correlation should focus on identifying requestor/subject mismatches, unusual certificate authentication patterns, and modifications to high-privilege certificate templates.
Advanced monitoring involves querying the CA database using tools like certutil.exe or PowerShell modules like PSPKI, as Windows event logs don’t capture all certificate attributes that could indicate malicious activity.
Defensive Hardening Measures
Template Security Configuration
Remove or restrict dangerous template configurations:
- Disable “Supply in request” for subject names
- Implement manager approval requirements
- Restrict enrollment permissions to specific security groups
- Review Enhanced Key Usage settings for authentication capabilities
Certificate templates should follow the principle of least privilege, with enrollment restricted to accounts that genuinely require certificate-based authentication.
CA-Level Controls
Harden Certificate Authority settings by:
- Disabling the EDITF_ATTRIBUTESUBJECTALTNAME2 flag
- Implementing strong certificate mapping policies
- Restricting enrollment agent permissions
- Enabling HTTPS-only access for web enrollment
The EDITF_ATTRIBUTESUBJECTALTNAME2 setting is particularly dangerous as it allows Subject Alternative Name specification in any certificate, effectively turning every template into a potential ESC1 vulnerability.
Registry Hardening
Configure certificate mapping registry keys for security:
- Set StrongCertificateBindingEnforcement to 2 (full enforcement)
- Configure CertificateMappingMethods to disable UPN mapping (0x4 flag)
- Implement proper Subject Alternative Name validation
These settings prevent weak certificate mapping attacks by forcing strong cryptographic binding between certificates and user accounts.
Incident Response Considerations
ADCS compromises require specialized response procedures beyond traditional password resets. Certificate validity periods extend beyond password changes, meaning stolen or malicious certificates remain functional even after account remediation.
Response steps should include:
- Certificate revocation for affected accounts
- Review of CA database for suspicious issuances
- Template configuration audits
- Private key security assessment
Organizations using Hawk-Eye’s security services benefit from specialized ADCS threat hunting capabilities that identify certificate-based persistence mechanisms often missed by traditional security tools.
Conclusion
ADCS vulnerabilities represent a critical threat to enterprise security, providing attackers with powerful persistence and escalation capabilities. The complexity of certificate services configuration creates numerous opportunities for misconfiguration, making regular security assessments essential.
Organizations must treat Certificate Authorities as Tier 0 assets, implementing comprehensive monitoring, hardening configurations, and maintaining ongoing security reviews. As attackers increasingly target certificate-based authentication mechanisms, Hawk-Eye’s advanced threat detection capabilities become crucial for identifying and mitigating these sophisticated attacks before they compromise critical systems.
The shift toward certificate-based authentication makes ADCS security a fundamental component of enterprise defense strategies. Organizations that neglect PKI security do so at their own peril, as certificate vulnerabilities provide attackers with some of the most powerful and persistent access methods available in modern Windows environments.