New Malware Masquerades as Palo Alto VPN Targeting Middle East Organizations

Background
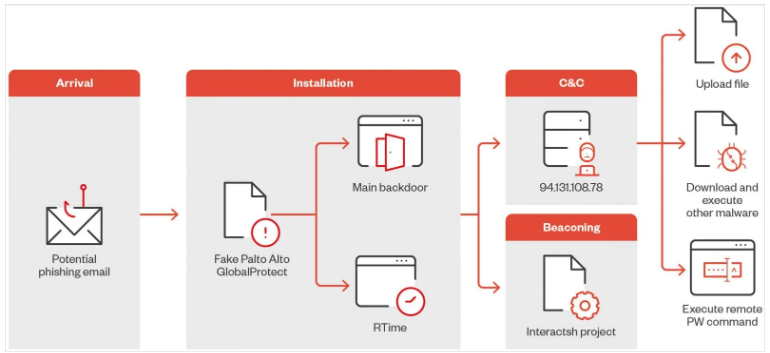
Threat actors target Middle Eastern enterprises using malware masquerading as the genuine Palo Alto GlobalProtect Tool, which can steal data and execute remote PowerShell instructions to further breach internal networks.
Palo Alto GlobalProtect is a legitimate security solution provided by Palo Alto Networks that enables safe VPN connection with multi-factor authentication. Organizations widely use the solution to ensure that remote employees, contractors, and partners have secure access to private network resources.
Utilizing Palo Alto GlobalProtect as bait reveals that attackers target high-value business entities utilizing enterprise software rather than random users.
Key features:
- Using dynamic C&C infrastructure: the malware redirects to a freshly registered URL, “sharjahconnect” (most likely referring to the UAE emirate Sharjah), which is intended to resemble a legitimate VPN interface for a UAE-based organization. This strategy is intended to allow the malware’s destructive actions to mix in with normal regional network traffic, improving its evasion capabilities.
- Domain masquerading: By impersonating a well-known area service, attackers leverage trust ties, boosting the possibility of successful C&C contacts.
- Geopolitical targeting: The domain’s regional specificity and the origin of the submission point to a targeted effort against Middle Eastern entities, possibly for geopolitical or economic espionage.
- Using newly registered domains: Using new domains for C&C activity enables attackers to avoid blacklists and complicates attribution.
Technical details:
It checks for indicators of running in a sandbox before executing its main code. Then it sends profile information about the compromised system to the command and control (C2) server.
As an additional evasion layer, the malware encrypts the strings and data packets that will be exfiltrated to the C2.
The C2 IP detected by Trend Micro used a newly registered URL containing the “sharjahconnect” string, making it appear to be a legal VPN connection portal for Sharjah-based offices in the United Arab Emirates.
Given the campaign’s targeting scope, this choice allows the threat actors to blend in with normal operations while reducing red flags that could raise the victim’s suspicion.
Using the Interactsh open-source tool, beacons are sent out at regular intervals to communicate the malware status with threat actors during the post-infection phase.
The commands received from the command and control server are:
| Command | Details |
| time to reset | Commands the malware to sleep for a specific amount of time. |
| pw | Execute a PowerShell script and return the result to the server hxxp[:]//94.131.108.78[:]7118/B/hi/, after which the threat actor is notified via DNS request if “step6” is successful. |
| pr | Processes a command string and performs different actions based on the command type:
wtime: Reads or writes a wait time to a file. create-process: Starts a process and returns its output. dnld: Downloads a file from a URL to a local path. upl: Uploads a file to a remote server. Encryption is used for secure communication with the remote server. If the command is unrecognized, it returns an “invalid program command” message. The result is sent to the C&C server hxxp[:]//94.131.108.78[:]7118/B/hi/. |
| invalid command type | In case an error occurs in any part of the execution, the malware uses the command function to send the result via the string “invalid command type”. |
Recommendations:
- Regular training sessions on the many forms of social engineering attacks, updates on new techniques and trends in social engineering, and educating employees to detect common red flags can all assist in keeping users from falling prey to social engineering lures.
- Giving employees access to only the data and systems they need for their jobs reduces the likelihood of attackers acquiring access to critical information, even during a successful breach.
- Organizations should use robust email and web security solutions to filter and block harmful and suspicious communications.
- To deal with social engineering attacks, companies must have a well-defined incident response plan in place. This includes taking prompt action to minimize and neutralize the threat.
IOCs
File-based
- Trojan.Gen.MBT
- WS.Malware.1
Machine Learning-based
- Heur.AdvML.A!300
- Heur.AdvML.A!400
- Heur.AdvML.A!500
- Heur.AdvML.B
- Heur.AdvML.B!200
79B38C4BE5AC888E38EC5F21AC3710F3D0936A72
72CDD3856A3FFD530DB50E0F48E71F089858E44F
hxxp://94.131[.]108.78:7118/B/hi/
94.131.108.78
portal[.]sharjahconnect.online
tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
step1-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
step2-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
step3-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
step4-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
step5-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
step6-{dsktoProcessId}.tdyfbwxngpmixjiqtjjote3k9qwc31dsx.oast.fun
References
New Malware Masquerades as Palo Alto VPN Targeting Middle East Users (thehackernews.com)
Threat Actors Target the Middle East Using Fake Palo Alto GlobalProtect Tool | Trend Micro (US)
Middle East targeted by malware using fake Palo Alto VPN (broadcom.com)
New backdoor malware impersonating Palo Alto’s GlobalProtect (fieldeffect.com)