Cicada – A new ransomware targeting VMware ESXi systems

Background
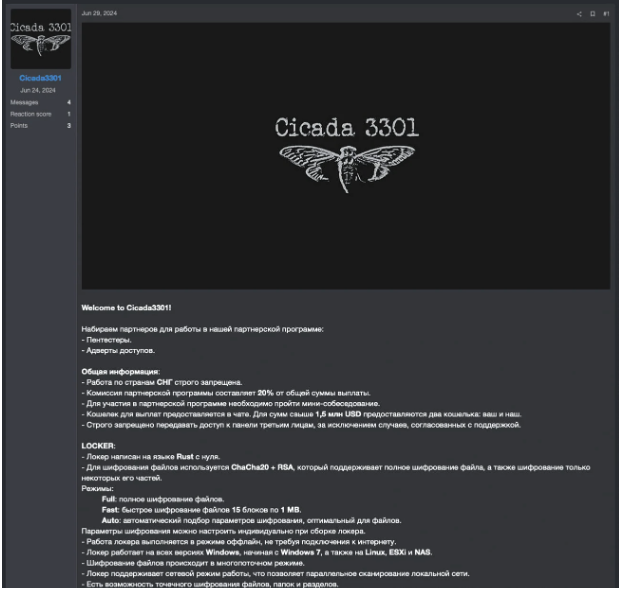
A recent ransomware-as-a-service (RaaS) campaign has swiftly targeted organizations across the globe by pretending to be the authentic Cicada 3301 organization. It has already listed 19 victims on its extortion page.
The new criminal operation bears the same name and logo as the enigmatic Cicada 3301 online and offline game, which ran from 2012 to 2014 and featured complex cryptographic riddles.
There is no link between the two, though, and the legitimate initiative has denounced any affiliation with the threat actors in a statement, while also denouncing the conduct of the ransomware operation.
Technical Details
Written in Rust, the Cicada3301 ransomware attacks Linux/ESXi and Windows hosts. Researchers from Truesec have analyzed a variation that is the same malware for Windows but targets VMware ESXi servers. The experts noted that only a small number of ransomware groups—including the now-defunct BlackCat/ALPHV group—have employed Rust-based ransomware, despite the fact that many of them are currently targeting ESXi systems. Significant similarities have been found between the ALPHV ransomware and Cicada3301’s ransomware, according to analysis.
The Cicada3301 ransomware has several interesting similarities to the ALPHV ransomware.
- Both are written in Rust
- Both use ChaCha20 for encryption
- Both use almost identical commands to shutdown VM and remove snapshots[1]
- Both use –ui command parameters to provide a graphic output on encryption
- Both use the same convention for naming files, but changing “RECOVER-“ransomware extension”-FILES.txt” to “RECOVER-“ransomware extension”-DATA.txt”[2]
- How the key parameter is used to decrypt the ransomware note
The Cicada3301 group launched their initial attack by using credentials that were either stolen or obtained through brute force to get in to ScreenConnect. There may be ties between the two, as evidenced by the ransomware group’s IP address being connected to the Brutus botnet. This timing aligns with the group that appears to have left the BlackCat/ALPHV ransomware, which suggests that Cicada3301 may be an ALPHV rebranding, a partnership with ALPHV’s developers, or an independent organization employing altered ALPHV code.
Rust-based ransomware Cicada3301 is compatible with Linux/VMware ESXi and Windows encryptors. The researchers analyzed the VMWare ESXi Linux encryptor for the ransomware activity as part of Truesec’s investigation.
The encryptor must be launched with a special key entered as a command line argument, just like BlackCat and other ransomware families like RansomHub. An encrypted JSON blob containing the configuration the encryptor will use to encrypt a device can be decrypted with this key.
According to Truesec, the encryptor uses the key to decrypt the ransom note as a means of validating its authenticity before carrying out the next encryption steps.
Several configurable parameters are supported by the Cicada3301 ransomware, allowing users to modify the malware’s behavior while it is being executed. These parameters, which are controlled by the clap::args library, consist of options such as:
- sleep: Delays execution of the ransomware by a specified number of seconds.
- ui: Displays real-time progress and statistics of the encryption process, such as the number of files encrypted.
- no_vm_ss: Encrypts files on ESXi hosts without shutting down running virtual machines, using the esxicli terminal and deleting snapshots.
Its primary function (linux_enc) encrypts files using the ChaCha20 stream cipher and then encrypts the symmetric key that was used throughout the process using an RSA key. The ‘OsRng’ function is used to generate the encryption keys at random.
Targeting certain file extensions that correspond to documents and media files, Cicada3301 measures the size of each file to decide where to encrypt the complete contents (<100MB) and where to apply intermittent encryption (>100MB).
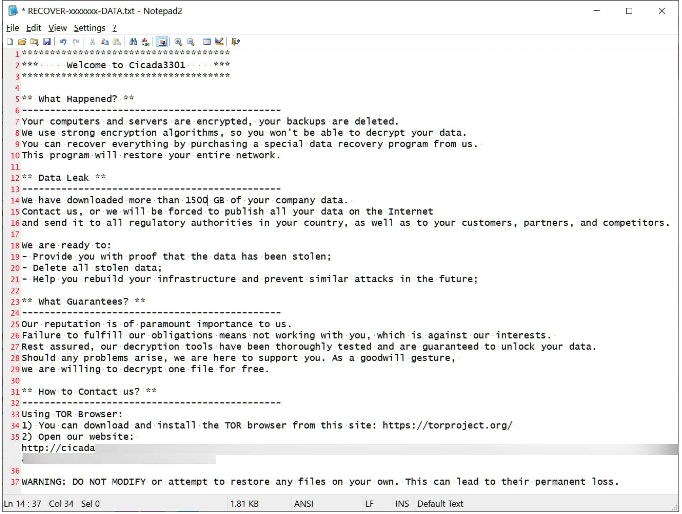
When encrypting a file, the encryptor will generate ransom notes with the name ‘RECOVER-[extension]-DATA.txt,’ as demonstrated below, and append a random seven-character extension to the file name. Notably, ransom notes with the name “RECOVER-[extension]-FILES.txt” and arbitrary seven-character extensions were also employed by BlackCat/ALPHV encryptors.
IOC (Indicators of Compromise):
Below are the Indicators of Compromise (IOCs) related to Cicada3301 ransomware:
| Type | Value |
| SHA256 | 7b3022437b637c44f42741a92c7f7ed251845fd02dda642c0a47fde179bd984e |
| SHA256 | 8b6ad87e408e38fc1db868da6e643f616dac59fbae08382c4a7dd4ea119ea057 |
| SHA256 | d5e38ac1187c607e701f506c4015bde94be6c485d566d004d810d7565c188743 |
| SHA256 | 26460aa2df29f766cb5712ebca44cb3365ebfdb5cae0b2ec36ef1e3568911d6a |
| SHA256 | cdec58a57381bb8c1e374efb0bf1897d89d1e096d2b704820893859d9f08d086 |
| SHA256 | ea9d994de91389280b334f2af991baa49ca613a6bf898d7bb25f88cc66488f5c |
| SHA256 | 3f5b623222c755d59052fab9e096c9d2b9a47d06b3a5de62fb9a66750af4efc4 |
| SHA256 | 27873e3d4ec3a0e7d66bee8bda4d65cc8fcefbdca2c8d5c049372a63ff0bc2ed |
| SHA256 | cf3ae16b01f7eb129e0e7387ac7feb61ecfce5db0d7494b3962c02c681f504d4 |
| SHA256 | 578ea26729b43fd976365a6700c80950e0b71a39e67bfff715423d60ae6bfab9 |
| SHA256 | 03ab1588acaabdb509e9db7cfe1e60522bc8baa13bbd35160b4bde7d1b6402ef |
| SHA256 | 4a08eb0eb1f4ebb54bceabbebcb7da48238f0278ae5421326ee65ec7951e4239 |
| SHA256 | 01b610e8ffcb8fd85f2d682b8a364cad2033c8104014df83988bc3ddfac8e6ec |
| SHA256 | 056c0628be2435f2b2031b3287726eac38c94d1e7f7aa986969baa09468043b1 |
| SHA256 | 062ce400f522f90909ed5c4783c5e9c60b63c09272e2ddde3d13e748a528fa88 |
| SHA256 | 0b452f7051a74a1d4a544c0004b121635c15f80122dc6be54db660ceb2264d6f |
| SHA256 | 0ec48b297dd1b0d6c3ddd15ab63f405191d7a849049feedfa7e44096c6f9d42a |
| SHA256 | 20fc3cf1afcad9e6f19e9abebfc9daf374909801d874c3d276b913f12d6230ec |
| SHA256 | 2317d3e14ab214f06ae38a729524646971e21b398eda15cc9deb8b00b231abc3 |
| SHA256 | 2417da3adebd446b9fcb8b896adb14ea495a4d923e3655e5033f78d8e648fcc8 |
| SHA256 | 37f56127226ce96af501c8d805e76156ca6b87da1ba1bb5d227100912f6c52d9 |
| SHA1 | 54a8fe5c70ed0007fdd346a9a75977fd9f8ad24a |
| SHA1 | c08a863c2e5288d4ce2a9d46a725518f12711a7 |
| IP Address | 91[.]92[.]249[.]203 |
| IP Address | 178[.]73[.]210[.]238 |
| IP Address | 188[.]119[.]112[.]225 |
| IP Address | 213[.]252[.]246[.]245 |
| IP Address | 45[.]14[.]224[.]93 |
| IP Address | 45[.]67[.]230[.]134 |
| IP Address | 81[.]7[.]7[.]159 |
| IP Address | 95[.]179[.]143[.]32 |
| IP Address | 88[.]198[.]101[.]58 |
| IP Address | 168[.]100[.]8[.]38 |
Detecting Cicada3301 Ransomware:
The following Yara rule can help detect the ransomware:
| rule Cicada3301_Ransomware {
meta: description = “Detects Cicada3301 ransomware based on specific strings within the PE executable” author = “Michael Gorelik, Morphisec” in_the_wild = true strings: $a1 = “RECOVER–DATA.txt” $a2 = “for /F \”tokens=2 delims=:\” %i in (‘sc query state^= all ^| findstr /I ‘) do sc stop %i” $a3 = “taskkill /IM * /F” $a4 = “net stop /y” $a5 = “—–BEGIN PUBLIC KEY—–“ condition: uint16(0) == 0x5A4D and 3 of ($a*) } |
Detection
The Yara signature mentioned below can help in detecting and hunting Cicada3301 ransomware:
rule elf_cicada3301{
meta:
author = “Nicklas Keijser”
description = “Detect ESXi ransomware by the group Cicada3301”
date = “2024-08-31”
strings:
$x1 = “no_vm_ss” nocase wide ascii
$x2 = “linux_enc” nocase wide ascii
$x3 = “nohup” nocase wide ascii
$x4 = “snapshot.removeall” nocase wide ascii
$x5 = {65 78 70 61 6E 64 20 33 32 2D 62 79 74 65 20 6B} //Use of ChaCha20 constant expand 32-byte k
condition:
uint16(0) == 0x457F
and filesize < 10000KB
and (all of ($x*))
}