CVE-2024-40766: Critical SonicWall Firewall Vulnerability

Background
SonicWall has released a patch to address a severe vulnerability discovered in certain SonicOS-based firewall devices.
The vulnerability, CVE-2024-40766 with a CVSS score of 9.3, is described as an improper access control vulnerability that could allow threat actors to gain unauthorized access to resources and crash the affected device. SonicWall did not disclose if it knew the vulnerability was being actively exploited.
SonicWall advises impacted users to install the necessary updates as soon as feasible. Users who are unable to deploy updates quickly should restrict device management access to local, trustworthy sources.
As of right now, no documented Proof of Concept (PoC) attacks have been discovered for this vulnerability, and we have not seen any exploitation of it in the wild. Threat actors have often targeted SonicWall firewalls, which are commonly found in corporate environments, according to CISA’s Known Exploited Vulnerabilities Catalog. Threat actors are likely to target it in the near future given its history and the possible access this new vulnerability may grant.
Affected Versions
Affected versions:
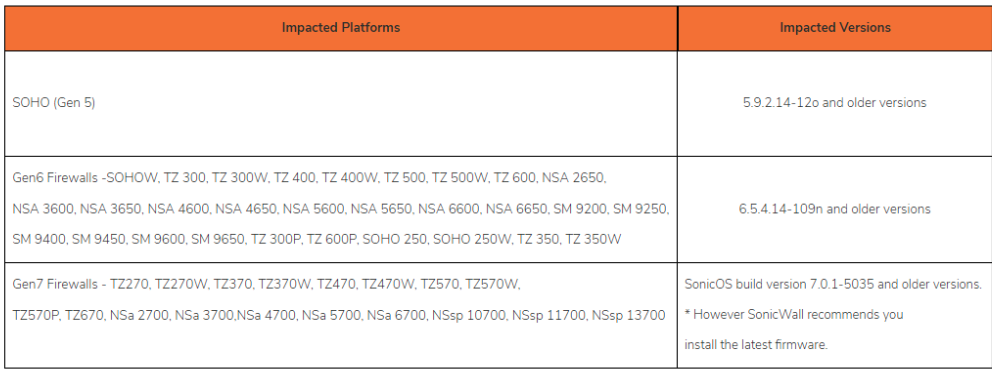
SonicWall Firewall Gen 5 and Gen 6 devices, as well as Gen 7 devices running SonicOS 7.0.1-5035 and previous versions, are impacted by this vulnerability.
Particular models that are affected include:
- Gen 5: SOHO gadgets with 5.9.2.14-12o or earlier.
- Gen 6: 6.5.4.14-109n and previous versions of the TZ, NSA, and SM models.
- Gen 7: TZ and NSA models using SonicOS builds 7.0.1-5035 and older.
Recommendations
Customers are strongly encouraged to update to the most recent fixed version.
| Product | Affected Platform | Fixed Version |
| SonicWall Firewall | SOHO (Gen 5) | 5.9.2.14-13o |
| Gen6 Firewalls -SOHOW, TZ 300, TZ 300W, TZ 400, TZ 400W, TZ 500, TZ 500W, TZ 600, NSA 2650, NSA 3600, NSA 3650, NSA 4600, NSA 4650, NSA 5600, NSA 5650, NSA 6600, NSA 6650, SM 9200, SM 9250, SM 9400, SM 9450, SM 9600, SM 9650, TZ 300P, TZ 600P, SOHO 250, SOHO 250W, TZ 350, TZ 350W |
| |
| Gen7 Firewalls – TZ270, TZ270W, TZ370, TZ370W, TZ470, TZ470W, TZ570, TZ570W, TZ570P, TZ670, NSa 2700, NSa 3700, NSa 4700, NSa 5700, NSa 6700, NSsp 10700, NSsp 11700, NSsp 1370 | While this vulnerability has not been reproduced in SonicOS firmware versions higher than 7.0.1-5035, SonicWall still recommends installing the latest firmware. |
SonicWall advises customers who are unable to patch right away to disable internet access to WAN management or limit firewall management access to reliable sources. Their guide contains comprehensive instructions for limiting access to the SonicOS admin panel.
Affected Versions
https://psirt.global.sonicwall.com/vuln-detail/SNWLID-2024-0015
https://www.sonicwall.com/support/knowledge-base/how-can-i-restrict-admin-access-to-the-device/170503259079248