The Linux Variant of TargetCompany Ransomware targets ESXi Environments

The TargetCompany ransomware was discovered in June 2021. Trend Micro tracks it under the name “Water Gatpanapun,” and it has a leak site known as “Mallox.” According to the reports, this year’s group activity is greatest in Taiwan, India, Thailand, and South Korea.
TargetCompany has been developing methods to get beyond security defenses used by organizations since it was discovered. One such method includes abusing totally undetectable (FUD) obfuscator packers and using a PowerShell script to get around the Antimalware Scan Interface (AMSI).
TargetCompany has a new variation that was just found by Trend Micro that is specifically designed to target Linux environments.
Technical Analysis
Since June 2021, TargetCompany has been in operation. When a file is encrypted, the filename ends in, .mallox,.exploit,.architek, or .brg.
TargetCompany wipes shadow copies from every drive and stops some processes that might be keeping important files, such as databases, open, just like other ransomware.
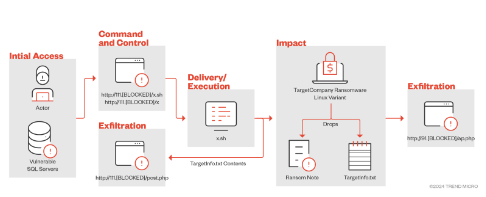
Virtualization environments are not being targeted by the threat actors behind TargetCompany in an effort to broaden the scope of their attacks and increase the amount of disruption and damage. By using the “uname” command, the ransomware operators have extended their capacity to determine whether a system is operating in a VMware ESXi environment.
The system is running VMware’s ESXi hypervisor if the system name matches “vmkernel.” Next, in order to encrypt files with particular extensions, the malware switches to “VM mode.”
The ransomware drops a text file called TargetInfo.txt containing victim data after it has been run. The content of the file TargetInfo.txt is subsequently forwarded to a C2 server, just like in the case of the ransomware that targets Windows systems.
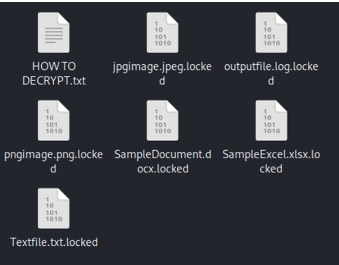
Following the encryption procedure, all folders holding encrypted files will contain a ransom note file with the name “HOW TO RECOVER!!.TXT.” The encrypted filenames are appended with the “.locked” extension by the malware.
Infection Chain
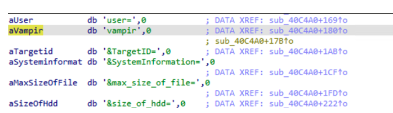
Data uploaded to Trend Micro’s C2 server allowed its researchers to associate the sample they examined with an affiliate known as “vampire.” Experts surmise that more comprehensive ransom demands and widespread targeting of IT systems are part of ongoing broader attacks. “Vampire” might have something to do with an affiliate that was mentioned in a Sekoia report.
Detection
rule win_targetcompany_ransomware {
strings:
$sequence_0 = { ff15???????? 85c0 7475 fe85a7fdffff 80bda7fdffff0c }
// n = 5, score = 500
// ff15???????? |
// 85c0 | test eax, eax
// 7475 | je 0x77
// fe85a7fdffff | inc byte ptr [ebp – 0x259]
// 80bda7fdffff0c | cmp byte ptr [ebp – 0x259], 0xc
$sequence_1 = { 53 ff15???????? ff75e8 ff15???????? ff75e0 ff15???????? 3975f0 }
// n = 7, score = 500
// 53 | push ebx
// ff15???????? |
// ff75e8 | push dword ptr [ebp – 0x18]
// ff15???????? |
// ff75e0 | push dword ptr [ebp – 0x20]
// ff15???????? |
// 3975f0 | cmp dword ptr [ebp – 0x10], esi
$sequence_2 = { eb43 b900100000 3bc1 733a 53 51 }
// n = 6, score = 500
// eb43 | jmp 0x45
// b900100000 | mov ecx, 0x1000
// 3bc1 | cmp eax, ecx
// 733a | jae 0x3c
// 53 | push ebx
// 51 | push ecx
$sequence_3 = { 83c424 33cd 33c0 5f e8???????? c9 c3 }
// n = 7, score = 500
// 83c424 | add esp, 0x24
// 33cd | xor ecx, ebp
// 33c0 | xor eax, eax
// 5f | pop edi
// e8???????? |
// c9 | leave
// c3 | ret
$sequence_4 = { 813d????????a9aaaa0a 722b 68???????? 8d4dd4 }
// n = 4, score = 500
// 813d????????a9aaaa0a |
// 722b | jb 0x2d
// 68???????? |
// 8d4dd4 | lea ecx, [ebp – 0x2c]
$sequence_5 = { e8???????? 57 6a0c 5a 8bce 8d45e0 e8???????? }
// n = 7, score = 500
// e8???????? |
// 57 | push edi
// 6a0c | push 0xc
// 5a | pop edx
// 8bce | mov ecx, esi
// 8d45e0 | lea eax, [ebp – 0x20]
// e8???????? |
$sequence_6 = { 83ec40 53 56 33f6 57 8d5dc4 }
// n = 6, score = 500
// 83ec40 | sub esp, 0x40
// 53 | push ebx
// 56 | push esi
// 33f6 | xor esi, esi
// 57 | push edi
// 8d5dc4 | lea ebx, [ebp – 0x3c]
$sequence_7 = { 50 8d45b0 50 e8???????? 8d45b0 50 8d85c0feffff }
// n = 7, score = 500
// 50 | push eax
// 8d45b0 | lea eax, [ebp – 0x50]
// 50 | push eax
// e8???????? |
// 8d45b0 | lea eax, [ebp – 0x50]
// 50 | push eax
// 8d85c0feffff | lea eax, [ebp – 0x140]
$sequence_8 = { bf???????? 8d75e8 e8???????? 8b1d???????? 8d75f0 }
// n = 5, score = 500
// bf???????? |
// 8d75e8 | lea esi, [ebp – 0x18]
// e8???????? |
// 8b1d???????? |
// 8d75f0 | lea esi, [ebp – 0x10]
$sequence_9 = { 8945ec e8???????? 53 6a01 8d758c e8???????? 53 }
// n = 7, score = 500
// 8945ec | mov dword ptr [ebp – 0x14], eax
// e8???????? |
// 53 | push ebx
// 6a01 | push 1
// 8d758c | lea esi, [ebp – 0x74]
// e8???????? |
// 53 | push ebx
condition:
7 of them and filesize < 328704
}
Recommendations
- Multifactor authentication (MFA) should be enabled to stop attackers from moving laterally within a network.
- When backing up essential files, follow the 3-2-1 rule: make three backup copies in two distinct file formats, and store one of the copies somewhere else.
- Patching and updating systems on a regular basis is crucial to maintaining patch management techniques that can prevent hostile actors from taking advantage of any software vulnerabilities. Operating systems and apps should also be kept up to date.
MITRE ATT&CK
| Tactic | Technique | ID |
| Defense Evasion | File Deletion | T1070.004 |
| Discovery | System Information Discovery | T1082 |
| Execution | Command and Scripting Interpreter: Unix Shell | T1059.004 |
| Command and Control | Ingress Tool Transfer | T1105 |
| Exfiltration | Exfiltration over Alternative Protocol | T1408 |
| Exfiltration over C2 Channel | T1041 | |
| Impact | Data Encrypted for Impact | T1486 |
IOCs
dffa99b9fe6e7d3e19afba38c9f7ec739581f656
2b82b463dab61cd3d7765492d7b4a529b4618e57
9779aa8eb4c6f9eb809ebf4646867b0ed38c97e1
3642996044cd85381b19f28a9ab6763e2bab653c
4cdee339e038f5fc32dde8432dc3630afd4df8a2
0f6bea3ff11bb56c2daf4c5f5c5b2f1afd3d5098
hxxp://111.10.231[.]151:8168/general/vmeet/upload/temp/x.sh
hxxp://111.10.231[.]151:8168/general/vmeet/upload/temp/x
hxxp://111.10.231[.]151:8168/general/vmeet/upload/temp/post.php