Polyfill Supply Chain Attack

Popular JavaScript library and service Polyfill.io allows outdated browsers that do not support browser APIs or newer JavaScript capabilities to support them. Usually, websites employ Polyfill by incorporating an HTML tag with JavaScript code. This gives the Polyfill JavaScript full control over that page, enabling it to do anything it wants, such as discreetly recording user input or replacing any content.
A script from the polyfill.io domain and service, which was acquired earlier this year by a Chinese firm called “Funnull,” has been altered to inject malicious code on websites in a supply chain attack, the Sansec.io research team recently warned. At the moment, more than 100,000 sites could be affected.
Polyfill CDN
A Content Delivery Network (CDN) is a distributed worldwide server system that serves users with web content according to their location. When it comes to JavaScript polyfill libraries, content delivery networks (CDNs) are essential since they effectively host and serve these libraries worldwide. Developers can reduce latency and improve load times by using content delivery networks (CDNs) to guarantee that their polyfills are delivered to users promptly and consistently. Developers were also able to avoid bundling JavaScript libraries by using a CDN.
A popular content delivery network (CDN) that dynamically provided polyfills depending on the HTTP headers of incoming requests was cdn.polyfill.io in the case of the malicious polyfill takeover. This ensured maximum compatibility by delivering the proper polyfill based on the user’s browser and version.
There are serious security issues associated with using polyfills hosted on a CDN. This is mainly because there is a chance that arbitrary JavaScript code execution could occur within the application context. For a specific web application, this risk is frequently identified as a Cross-site Scripting (XSS) vulnerability.
The integrity and security of the external server are what the application depends on when it fetches a polyfill library from a CDN as in the actual CDN source. As demonstrated by the most recent attack against cdn.polyfill.io, the compromised code can be injected and run in the user’s browser if the hosted library or the CDN is affected. Such malicious code is capable of carrying out a number of malicious activities, including phishing site redirection, data theft, and malware infection. This kind of XSS vulnerability has the worst possible effects on browser security.
Impact
The original creator of the Fastly-hosted polyfill.io website, Andrew Betts, estimated in 2017 that up to 700 million requests a month were made to update outdated browsers with modern web standards and that a staggering 91 million browsers were requesting to import the library every day.
Currently, Polyfill is embedded on over 100,000 websites using the “cdn.polyfill.io” name. The potential daily traffic of thousands of visitors to each of these sites underscores the significant risks involved and the wide-ranging consequences of this supply chain attack.
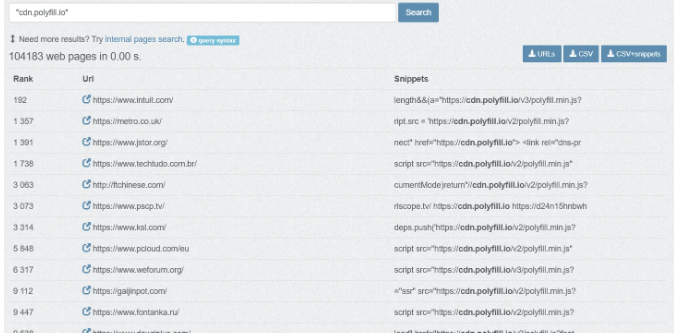
In a report by Germán Fernández, the Atlassian community website has also been identified as importing the JavaScript polyfill library from the malicious polyfill.io domain.
Silent Push Labs also discovered that the malicious polyfill.io source was present on government websites, and they reported this information to CISA.
Code from the ‘cdn.polyfill[.]io’ service is still embedded in a number of npm packages intended to provide the polyfill functionality.
How the Exploit Works
| Plugin Name | Affected Versions | Fixed Version |
| Social Warfare | 4.4.6.4 to 4.4.7.1 | 4.4.7.3 |
| Blaze Widget | 2.2.5 to 2.5.2 | 2.5.4 |
| Wrapper Link Element | 1.0.2 to 1.0.3 | 1.0.5 |
| Contact Form 7 Multi-Step Addon | 1.0.4 to 1.0.5 | 1.0.7 |
| Simply Show Hooks | 1.2.1 to 1.2.2 | No available fixes |
- Choices
- PluginAuth
Detection
The below rule can detect if any website is currently impacted by the Polyfill attack:
rules:
– id: polyfill-compromise
patterns:
– focus-metavariable: $…URL
– pattern-either:
– pattern: |
‘$…URL’
– pattern: |
“$…URL”
– metavariable-regex:
regex: https?://(cdn\.polyfill\.io)
metavariable: $…URL
message: Found compromised polyfill.io load which is currently serving malware
to some targets. Replace with Fastly or Cloudflare-hosted version.
languages:
– generic
severity: ERROR
fix: |
https://polyfill-fastly.io/v3/polyfill.min.js
metadata:
category: security
cwe:
– “CWE 506: Embedded Malicious Code”
confidence: HIGH
likelihood: HIGH
impact: HIGH
owasp:
– A8:2021 Software and Data Integrity Failures
references:
– https://sansec.io/research/polyfill-supply-chain-attack
– https://cdnjs.cloudflare.com/polyfill
– https://community.fastly.com/t/new-options-for-polyfill-io-users/2540
subcategory:
– vuln
Recommendations
Following are some best practices you should consider to help protect from the polyfill supply chain attack:
- Use only CDNs from reliable suppliers. For instance, Cloudflare is renowned for its dependability and strong security protocols.
- As a drop-in substitute, Cloudflare suggests using the polyfill clone they introduced at https://cdnjs.cloudflare.com/polyfill.
- Audit and keep an eye on any third-party dependencies and scripts on a regular basis.
- Subresource Integrity (SRI) tools can be used to guarantee that content provided by content delivery networks (CDNs) has not been altered. They can also be used to pin content to an intended version or hash that has been audited and found to be free of malicious or other undesirable behavior.
- To limit the sources from which scripts can be loaded, implement a robust CSP. By doing this, harmful scripts may not run. Because polyfills are frequently part of the application loading critical route, they execute with the same permissions as other JavaScript on the page, which makes them a target for attackers looking to take advantage of this trust. Because of this risk, it’s crucial to use reliable and secure CDNs, put strong security measures in place like Content Security Policy (CSP), and routinely audit third-party dependencies to protect against vulnerabilities of this kind.
- Determine if polyfills are still required for the project. Many of the functionality that polyfills offer are now natively supported in current browsers. It is strongly advised that you vendor your dependencies using your own project assets rather than depending on CDNs or other third-party sources.
IOCs
hxxps://kuurza[.]com/redirect?from=bitget
hxxps://www.googie-anaiytics[.]com/html/checkcachehw.js
hxxps://www.googie-anaiytics[.]com/ga.js