ScreenConnect Authentication Bypass (CVE-2024-1709 & CVE-2024-1708)
Background
Since the advisory’s publication, these vulnerabilities have been shown to be highly exploitable and have been actively used in real-world situations. Furthermore, there is now widespread access to proof of concept exploit code, which raises the potential risk of these vulnerabilities.
Given how simple it is for attackers to take advantage of these vulnerabilities in the wild, the severity is highlighted by this. About 3,800 ConnectWise ScreenConnect instances were found to be susceptible, according to a tweet published by Shadowserver on February 20, 2024. This highlights the broad risk that these vulnerabilities offer.
CVE-2024-1709 – Authentication Bypass
A crucial error in ConnectWise ScreenConnect versions 23.9.7 and earlier’s authentication procedure led to the discovery of the initial vulnerability, known as CVE-2024-1709. Upon reviewing a text file, this vulnerability was discovered. The analysis showed that the authentication system was not sufficiently protected against all possible access points, including the important setup wizard (setup wizard.aspx).
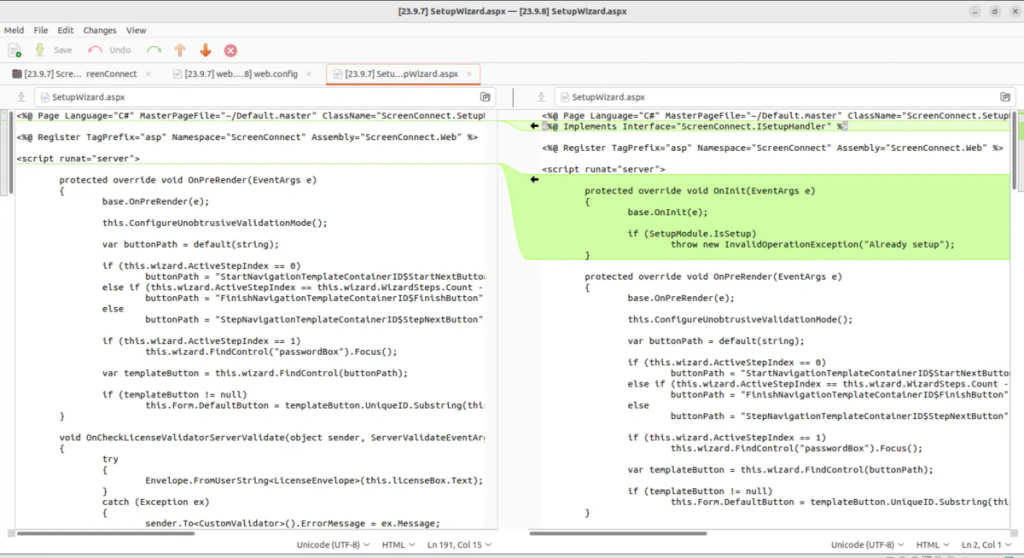
An important enhancement was added to a text file named SetupWizard.aspx in the most recent version of ConnectWise ScreenConnect. This file manages the setup wizard, which is used to install a system license and set up the first administrative user. There used to be a possible problem where the setup wizard could be accessed even after the first setup had finished.
Code difference of SetupWizard.aspx (Source: horizon3.ai )
CVE-2024-1708 – Path Traversal
The second vulnerability, identified in the ConnectWise ScreenConnect advisory as CVE-2024-1708, is associated with a ZipSlip attack vector. Because of improper handling of ZIP files, this vulnerability enables attackers to alter the contents of these files in order to run malicious code.
Attackers may be able to remotely execute code on a system thanks to this serious vulnerability. Nevertheless, it’s crucial to remember that access to a certain ScreenConnect function known as “Extensions” and administrative credentials are necessary in order to abuse it. It can, however, have chaining effects when used conjugatively with CVE-2024-1709. The majority of.aspx and.ashx files located in C:\Program Files (x86)\ScreenConnect\App_Extensions\root are probably malicious.
Recommendation
We strongly advise all customers using on-premise versions of ConnectWise ScreenConnect to update as soon as possible in order to guard against the anticipated widespread exploitation of these vulnerabilities, given their severity and ease of exploiting.
| Product | Affected Versions | Fixed Version | Latest Version |
|---|---|---|---|
| ConnectWise ScreenConnect | 23.9.7 and prior | 23.9.8 | 23.9.10.8817 |
Detection
sigma/rules-emerging-threats/2024/Exploits/CVE-2024-1709 at master · SigmaHQ/sigma (github.com)
sigma/rules-emerging-threats/2024/Exploits/CVE-2024-1708 at master · SigmaHQ/sigma (github.com)
IOCs
ConnectWise reported that the following IP addresses were used by threat actors:
155.133.5.15
155.133.5.14
118.69.65.60