DCSync Attacks Explained
October 30, 2023

Once an attacker gets access to a Windows endpoint, they can access credentials saved in clear text or as a hash. It is possible to retrieve credentials from a compromised Windows endpoint using a number of practical methods.
Background:
For instance, attackers might use the SAM database, Cached Domain Credentials, LSASS Memory, or Replicating Directory permissions to retrieve credentials. They can go laterally and get more access by using their acquired credentials. Attackers can retrieve credentials via the DCSync attack against Active Directory (AD) accounts that have the “Replicating Directory Changes” permission. For the entire AD domain of the company, these accounts with granted permissions might be extremely dangerous. They allow hackers to execute other attacks, like Golden Ticket and Pass the Ticket (PTT), to access any resource on the AD domain without restriction.AD Replication:
To handle AD objects in the environment, most organizations require numerous Domain Controllers. The Directory Replication Service in Active Directory, which Microsoft designed to maintain these numerous Domain Controllers in sync with one another, can be leveraged by attackers to obtain the users’ password hashes in Active Directory. To discover objects within AD, domain accounts need the “Replicate Directory Changes” access. A domain change query is also possible with the replication permission. With the “Replicate Directory Changes” permission, an attacker can take control of common, non-privileged user accounts and utilize malicious replication to steal passwords. Using a DCSync attack, the domain security principals who have been granted both of the following rights at the domain level can successfully retrieve password hash information. Any Domain User with the following permissions enabled may ask for the replication of AD objects, including the user NTLM hashes, and may eventually request the DC to dump the NTDS.dit file: CN: DS-Replication-Get-Changes (GUID: 1131f6ad-9c07–11d1-f79f-00c04fc2dcd2) CN: DS-Replication-Get-Changes-All (GUID: 1131f6ad-9c07–11d1-f79f-00c04fc2dcd2) CN: DS-Replication-Get-Changes-In-Filtered-Set (GUID: 89e95b76–444d-4c62–991a-0facbeda640c)DCSync Attack:
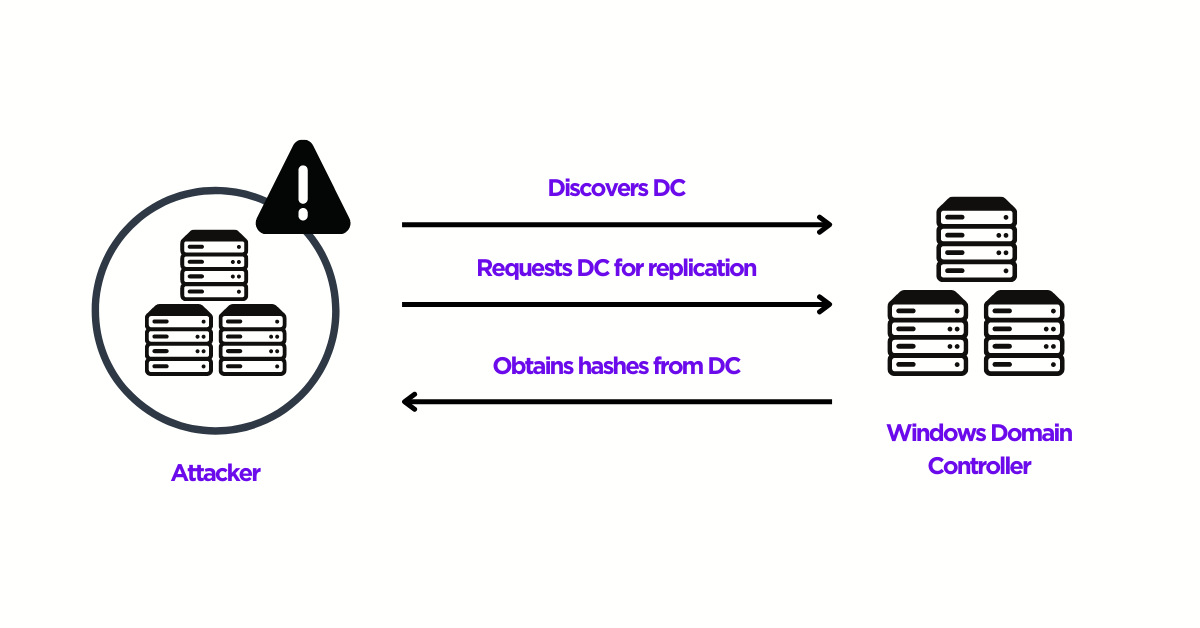
Active Directory environments are supported by domain controllers, which are the servers that host the Active Directory Domain Services databases and regulate user authentication requests to other services inside the domain. Attackers who take control of a domain controller put the security of the entire Active Directory forest at risk. They would be able to do additional post-exploitation attacks, access, and compromise other Active Directory user accounts, and manipulate Active Directory databases. The DCSync attack, which was developed and released in 2015, significantly reduces the complexity of gaining access to an Active Directory domain controller by eliminating the need to compromise one. Instead, DCSync enables an attacker to completely compromise a whole forest using a single domain administrator credential (or even a domain user with enough capabilities). That attacker can impersonate a domain controller thanks to DCSync. The primary Domain Controller is asked to replicate user credentials to the attacker via the Directory Replication Service (DRS) Remote Protocol using the GetNCChanges request. The high-level procedure of a DCSync attack, which enables attackers to gain total control of an organization’s AD infrastructure, is described here.- Make use of a user account that is common or non-privileged and has the “Replicate Directory Changes” authority.
- Discover a DC under the given domain name.
- Use the Microsoft Directory Replication Service Remote (MS-DRSR) protocol to request the DC to replicate sensitive data, such as password hashes.
- Obtain the NTLM hashes of accounts like Administrators and KRBTGT that may be beneficial.
- To move laterally, make a Golden Ticket and use Pass the Ticket (PTT) attacks.

Working of DCSync attack (Source: SentinelOne)
DCSync attacks are simple to launch with the aid of tools like Mimikatz and Empire. For instance, attackers can impersonate a domain controller and send the request using built-in capabilities like Mimikatz and other tools. As a result, the attacker is spared from having to delete a Windows NTDS.DIT database file, a “red flag” operation that would most likely result in alerts from a network monitoring system like an IPS or SIEM.Detection:
- Monitor domain controller logs for replication requests and other unscheduled activity possibly associated with DCSync (DS0026).
- Monitor and analyze traffic patterns and packet inspection associated with protocol(s) that do not follow the expected protocol standards and traffic flows (e.g. extraneous packets that do not belong to established flows, gratuitous or anomalous traffic patterns, anomalous syntax, or structure). Consider correlation with process monitoring and command line to detect anomalous process execution and command line arguments associated with traffic patterns (DS0029).
Event IDs to Monitor:
- Security Event ID 4662 (Audit Policy for an object must be enabled) – An operation was performed on an object.
- Security Event ID 5136 (Audit Policy for an object must be enabled) – A directory service object was modified.
- Security Event ID 4670 (Audit Policy for an object must be enabled) – Permissions on an object were changed.
Mitigation:
- Manage the access control list for “Replicating Directory Changes” and other permissions associated with domain controller replication (M1015).
- Ensure that local administrator accounts have complex, unique passwords across all systems on the network (M1027).
- Do not put user or admin domain accounts in the local administrator groups across systems unless they are tightly controlled, as this is often equivalent to having a local administrator account with the same password on all systems. Follow best practices for the design and administration of an enterprise network to limit privileged account use across administrative tiers (M1026).