PhishForce: In-the-wild Phishing of Facebook Accounts Using a Vulnerability in Salesforce’s Email Services
August 28, 2023

We have been subjected to fraudulent emails from the early days of the internet, from intrusive spam to highly targeted and customized phishing efforts. Bad actors will always manage to keep one step ahead, coming up with new ways to bypass filtering laws and other regulations aimed to clean up our inboxes, despite substantial breakthroughs in email detection and blocking over the years.


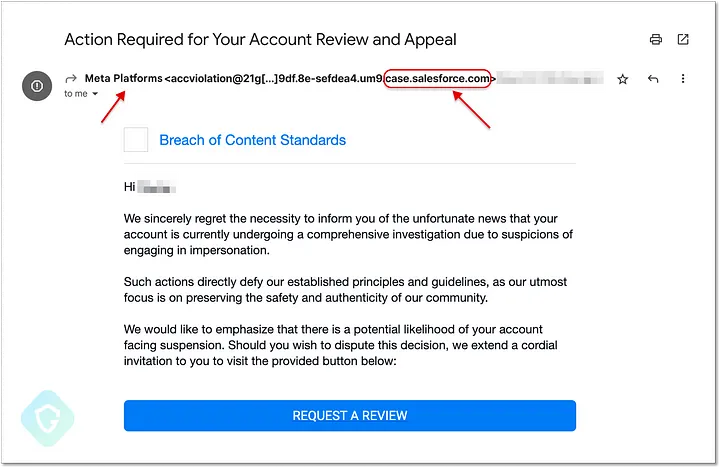 The message’s circled portion displays the “@salesforce.com” domain, yet it is identified as originating from “Meta Platforms.” That ought to serve as a red flag that this email is a phishing scam. Another error is the label on the large blue button, which reads “Request a Review.” It doesn’t: When a user clicks on this button, a phishing website designed to steal their Facebook account information is delivered in its place.
The phishing page is hosted by Facebook and appears to be some type of game, which is the second red flag. However, the page also contains stuff unrelated to gaming. The ingenious aspect of this comes into play here: Using Salesforce.com’s official email gateway services, the malicious email is sent from a salesforce.com email address and contains a genuine link to facebook.com. Essentially, this appearance of respectability is a cover for the malicious email.
The message’s circled portion displays the “@salesforce.com” domain, yet it is identified as originating from “Meta Platforms.” That ought to serve as a red flag that this email is a phishing scam. Another error is the label on the large blue button, which reads “Request a Review.” It doesn’t: When a user clicks on this button, a phishing website designed to steal their Facebook account information is delivered in its place.
The phishing page is hosted by Facebook and appears to be some type of game, which is the second red flag. However, the page also contains stuff unrelated to gaming. The ingenious aspect of this comes into play here: Using Salesforce.com’s official email gateway services, the malicious email is sent from a salesforce.com email address and contains a genuine link to facebook.com. Essentially, this appearance of respectability is a cover for the malicious email.


Background
A sophisticated email phishing operation that took use of genuine Salesforce email services and SMTP servers’ 0-day vulnerability has been discovered by Guardio’s Email Protection. The research team at Guardio Labs has discovered an actively exploited vulnerability that allows threat actors to create customized phishing emails using the Salesforce infrastructure and domain. It uses an obsolete tactic: sending malicious emails while concealing them behind typically trusted mail gateways so that the emails won’t be blocked by defense mechanisms.Phishforce Vulnerability
Customers of the Salesforce CRM are able to send emails under their own brands utilizing verified custom domains. This prevents users from impersonating other brands in emails they send using Salesforce without authorization. Guardio Labs, however, reports that the attackers discovered a way to take advantage of Salesforce’s “Email-to-Case” tool, which businesses employ to turn incoming client emails into usable cases for their support staff.
A common “Email-To-Case” Flow in Salesforce Eco-System (Guardio)
In order to take control of a Salesforce-generated email account, the attackers specifically set up a new “Email-to-Case” flow and then made a new inbound email address on the “salesforce.com” domain.
Generated Salesforce address (Guardio Labs)
After that, they configured the address as an “Organization-Wide Email Address,” which Salesforce’s Mass Mailer Gateway utilizes for outgoing emails, and lastly, they went through the verification procedure to validate ownership of the domain. Through this method, they were able to send emails to anybody using their Salesforce email address, getting through both Salesforce’s verification safeguards and any other email filters and anti-phishing measures in place. The phishing kit used in this attack includes ways to go around two-factor authentication in order to acquire Facebook account credentials. The message’s circled portion displays the “@salesforce.com” domain, yet it is identified as originating from “Meta Platforms.” That ought to serve as a red flag that this email is a phishing scam. Another error is the label on the large blue button, which reads “Request a Review.” It doesn’t: When a user clicks on this button, a phishing website designed to steal their Facebook account information is delivered in its place.
The phishing page is hosted by Facebook and appears to be some type of game, which is the second red flag. However, the page also contains stuff unrelated to gaming. The ingenious aspect of this comes into play here: Using Salesforce.com’s official email gateway services, the malicious email is sent from a salesforce.com email address and contains a genuine link to facebook.com. Essentially, this appearance of respectability is a cover for the malicious email.
The message’s circled portion displays the “@salesforce.com” domain, yet it is identified as originating from “Meta Platforms.” That ought to serve as a red flag that this email is a phishing scam. Another error is the label on the large blue button, which reads “Request a Review.” It doesn’t: When a user clicks on this button, a phishing website designed to steal their Facebook account information is delivered in its place.
The phishing page is hosted by Facebook and appears to be some type of game, which is the second red flag. However, the page also contains stuff unrelated to gaming. The ingenious aspect of this comes into play here: Using Salesforce.com’s official email gateway services, the malicious email is sent from a salesforce.com email address and contains a genuine link to facebook.com. Essentially, this appearance of respectability is a cover for the malicious email.
Attack Chain

Attack Chain – Guardio Labs
Recently we received a suspicious email from “[email protected]” regarding vendor registration abusing the same phishforce vulnerability. On first look, it is a bit difficult to classify it as a phishing email as it is received from a trusted sender bypassing anti-phishing mechanisms.
