How to Detect Typosquatting using DNSTwist
Typosquatting is a social engineering attack in which a threat actor registers domains with purposefully misspelled versions of well-known companies’ or websites’ domains and puts malicious content on them or tempts users to enter sensitive data.
Typosquatting:
Internet users who enter a URL improperly into their browser or click on a URL in a phishing email are the target of this kind of attack. Hackers will attempt to emulate the appearance of the original website in order to maximize the likelihood of a successful cyber-attack.
Typosquatting affects more than just well-known companies and websites. Any brand might be chosen, and occasionally it is even simpler to carry out this attack against less renowned firms because the more convincing domain names will be accessible for registration. Typosquatting is not just a problem for users; it also harms the reputation of the brands and organizations it targets.
Typosquatting techniques:
The following are some sophisticated typosquatting methods:
- Homograph Attacks:
This is dependent on visual resemblance. For instance, an uppercase I in sans-serif font resembles a “l.” Another illustration is the Latin letter “y,” which is actually the Cyrillic letter U. This kind of attack is uncommon, though. - Soundsquatting:
Users may select the erroneous term when two words have the same pronunciation but different spellings. For instance, “ate” could be misinterpreted as “eight”. - Bitsquatting:
This depends on bit-level errors being made by the computer hardware. For instance, “microsoft.com” could be mistyped as “mic2osoft.com” by omitting a single bit.
Detecting Typosquatting using DNSTwist:
Using an inputted domain, Marcin Ulikowski’s Dnstwist Python script makes it possible to identify phishing, typo squatters, and attack domains. Using a domain name provided, it creates a huge list of permutations and then checks to see if any of them are already in use. The tool can be downloaded from the GitHub repository and can be installed on Linux/Windows/Mac.
https://github.com/elceef/dnstwist
Here are the commands for quick installation either through pip/apt/brew/docker:
`pip install dnstwist[full]`
`sudo apt install dnstwist`
`brew install dnstwist`
`docker run -it elceef/dnstwist`
When running the script, a number of options are available in Dnstwist. These are the options:
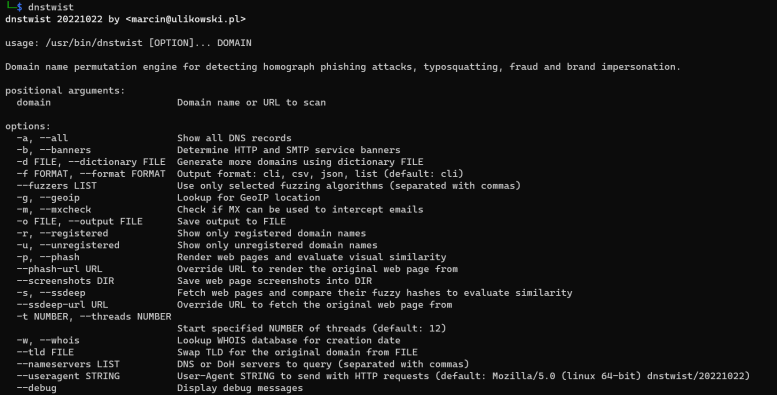
Fig 1. DNSTwist Options
You can just enter a domain for simple usage to acquire a list of probable attack domains. While somewhat helpful, utilizing different command line parameters will help you narrow down your search and get exactly what you’re looking for.

Fig 2. Simple Usage
For longer input domains, thousands of domain variants are typically generated. In certain circumstances, it might be practical to just show registered users. The -r parameter in dnstwist instructs the application to only output domain names that are actually registered.

Fig 3. Filtering out registered domains
On phishing domains, attackers occasionally set up email “honey pots” and wait for misspelled emails to arrive. In this case, attackers would set up their server to catch all emails sent to that domain, regardless of who the message was intended for. Another dnstwist feature enables quick testing of any mail server (identified by a DNS MX record) to determine which one can be exploited with such malicious intent. The SPYING-MX string will be used to flag suspicious servers.
The -g flag can be used to view a site’s geo-location based on its IP address. By using the command ./dnstwist.py -rg example.com, for instance, the list displayed in the preceding section will now include the site’s location.
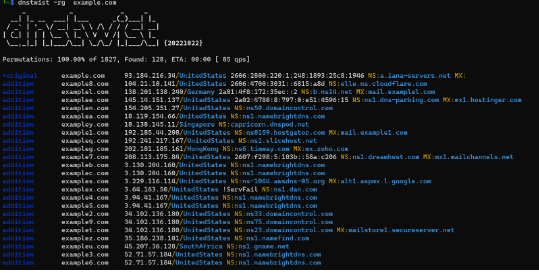
Fig 4. Finding geolocation of the domains
Ssdeep, a tool in Dnstwist that connects to the inputted domain and generates a fuzzy hash of the website, is quite helpful. It then calculates the percentage of similarity between your site and the attackers by comparing that hash to the hashes of the found registered domains. If the percentage is high, it means that the websites in the produced domain and the inputted domain are almost identical and may be exploited in phishing scams. The unique feature of detecting similar HTML source code can be enabled with –ssdeep argument.
Mitigation for Typosquatting:
- If you already have a domain, one defensive strategy is to register common variants and typos of it.
- Use multi-factor authentication to protect your domain name on domain registrars
- Don’t forget to set notifications and alerts when its time for renewing your domain
- Implement brand monitoring techniques to ensure brand impersonation using typosquatting is quickly identified and taken-down
- Using the output of DNSTwist use those permuations to block such domains on your web, proxy and mail gateways.
- Use SSL certificates at all times to enable site ownership verification for users.
- You have the option to take legal action against typosquatters if you have a trademark.
- Enhance your site’s SEO so that it ranks higher in search results than sites with typos.