Recent Uber Breach and Lessons Learnt
September 29, 2022

Uber acknowledged reports of a widespread cybersecurity compromise on September 15th. The security investigation found that the company’s system had been seriously compromised, with attackers going laterally to access the vital infrastructure of the business.

Background:
Uber acknowledged reports of a widespread cybersecurity compromise on September 15th. The security investigation found that the company’s system had been seriously compromised, with attackers going laterally to access the vital infrastructure of the business. A young hacker who claimed to have broken into Uber’s systems posted vulnerability reports and screenshots of the company’s crucial assets, including an email dashboard and the Slack server, bringing attention to the cybersecurity crisis. On the bug bounty website HackerOne, this private information was made available to the general public. The HackerOne vulnerability reports demonstrate that the attacker gained access to the system’s internal network, compromising the Google Workspace admin dashboard, VMware vSphere/ESXi virtual machines, and Amazon Web Services console.Attack Cycle:
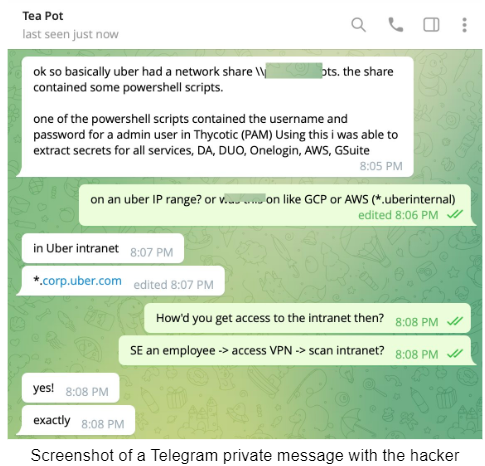
- Attackers gained access to a VPN and Uber’s internal network *.corp.uber.com using a social engineering effort against Uber employees.
- Once inside the network, the hacker discovered a few PowerShell scripts, one of which had the domain admin account’s login information for Thycotic, Uber’s Privileged Access Management (PAM) solution, hard coded.
- AWS, GCP, Google Drive, Slack workspace, SentinelOne, HackerOne admin console, Uber’s internal employee dashboards, and a few code repositories were among the services and internal tools the attacker used to access and control using admin access.
- The hacker then mocked Uber by informing them of the vulnerability via a message in their company’s Slack channel.


Breach Analysis:
According to news sources detailing the hack of Uber’s systems, the attacker tricked one of the staff members into disclosing their password, allowing the target to get initial access. Researchers believe that password-stealing software like RedLine which was installed on an employee’s PC may have taken the employee’s login information. Redline has also been used by Lapsus$ to acquire employee credentials in the past. According to Uber, the hacker might have purchased the stolen passwords from a dark web marketplace. Bypassing MFA: The attacker spammed the victim with the repeated MFA push/deny to overwhelm him and then later posed as the “IT” team over WhatsApp to get the victim to accept and visit his created Phishing page. The victim then visited the fake Uber login page and entered credentials. This technique is also known as MFA fatigue. Most people have a common misconception that MFA prevents social engineering. Although MFA can prevent social engineering it is vulnerable to Man in the middle attack. ( MiTM). MFA can also be bypassed Attacker can set up a fake Uber login page with tools like evilginx on his local machine and send it to the victim. Initial Access: After gaining access to the employee’s account, the attacker utilized that person’s preexisting VPN access to pivot to the intranet network. In comparison to external infrastructure, internal network infrastructure is frequently less configured, protected, and audited. Lateral Movement: Prior to the incident, logs obtained from information thieves were being sold on the underground market. Raccoon and Vidar were the infostealers used in these attacks on Uber employees. According to the evidence, the attacker used the acquired data to move laterally within Uber’s network. Hardcoded credentials in a PowerShell script were a major weakness that gave the attacker such extensive access. These login credentials granted administrator access to Thycotic, a PAM system. With admin access, you can grant yourself or retrieve secrets from all connected systems. The PAM system manages access to several systems. The attacker now appeared to have full access to all of Uber’s internal systems as a result. Impact: The attacker got access to Uber’s internal network environment including Gsuite Vcenter, Slack, AWS, and their EDR portal. The attacker was able to access the dashboard at HackerOne, where security researchers report bugs and vulnerabilities. However, any bug reports the attacker was able to access have been remediated according to Uber.Lessons Learnt:
- Implemented Zero-Trust Network Access (ZTNA) and Software-Defined Perimeter (SDP)
- Organizations should start using phishing-resistant MFA like hardware security keys, which require employees to physically plug in a USB device to their computers after entering their credentials – specifically for privileged users.
- Use advanced risk-based authentication and authorization approach with conditional access that looks at device fingerprint, device that is managed and connected to the domain, geo-ip, location, device X.509 certificate authnetication and so on.
- SSO is a double-edge sword – once credentials are compromised you have access to all integrated platforms. Use with case!
- Ensure VPN is built around SSL VPN with endpost host check and ensure the above aspects are enforced and baselines from monitoring perspective.
- Performing regular security awareness training and simulated phishing tests for employees that target compromising MFA and simulate context bypass to ensure risk-based and conditional access is working as expected.
- Ensure your secrets, master passwords, tokens and private keys are enclaved and high segmented into different vaults, with access governed through strict access policies where only specific workloads are accessible.
- Ensure Powershell and Automation Scripts do not contain hardcoded passwords
- Secure the management interfaces of all infrastructure and critical security controls by ensuring access is only permitted from authorized /32 IP addresses.
- Establish a naming convention of workloads and server hostnames that are difficult to understand. Dont name a jump server “JUMP-SRV” 🙂
- Last but not least, establish proper monitoring controls in place, use baselining techniques to determine admin activity and behavior of subjects and objects.