Using Windows Event Forwarding for Centralized Windows Monitoring – Part 1

Staying on top of cyber threats in your environment could be challenging even with a lot of protective measures in place. The threat landscape is constantly evolving and often the case is that your protective measures are playing catch up.
This is where your Security Operations Center comes in to bridge the gap between threat actors’ evolving tactics and techniques and your protective measures. However, the success of a SOC greatly depends on the level of visibility into the environment which it protects.
SOC analysts use SIEM (Security Information and Event Management) as the foundational tool to gain insight into the environment.
Consider the below scenario.
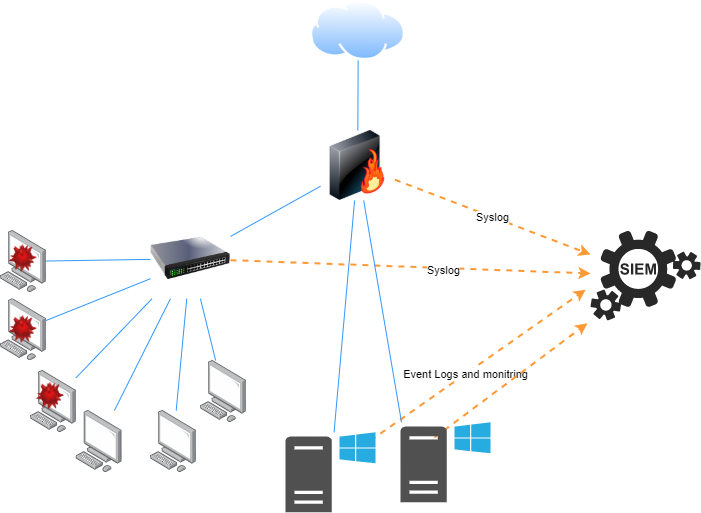
This is an example of a scenario where the SIEM has limited visibility into an environment. The firewall, switch and servers send logs to the SIEM, however, there is no visibility into the activities of the endpoints unless it is related to traffic going via the firewall. An infected host in the endpoint subnet could propagate throughout the subnet with the SIEM being none the wiser.
There are multiple ways to maximize visibility into the environment. One of the best ways to monitor windows hosts is using event logs. Windows event log is a detailed record of the system, security, and application activities maintained by the Windows operating system.
Sending Windows Event Logs to SIEM
There are multiple ways to send Windows event logs to the SIEM. Some SIEM implementations come with agents which can be installed on Windows machines to collect and send event logs (example: Wazuh). Some solutions are focused on collecting and sending event data to a centralized location (example: NXLog).
Challenges
- When the number of windows hosts in your environment are in the hundreds or thousands, it could be a daunting task to install and manage the agents on all the hosts.
- Micro-segmentation is key in preventing an attacker who has gained access to a system from pivoting to different networks and compromising a larger section of the infrastructure. It would be insecure to allow traffic from all user segments to the SIEM.
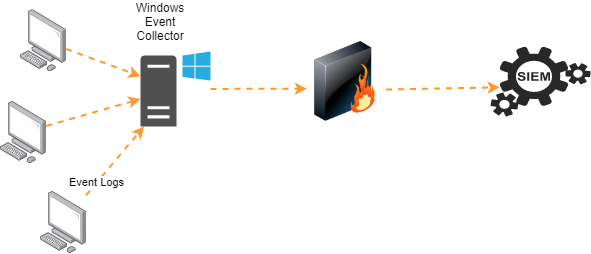
Windows Event Forwarding
Windows Event Forwarding (WEF) enables Windows endpoints to send event logs to a Windows Event Collector (WEC) server. The WEC servers would then send the collected event logs to the SIEM using the methods discussed earlier.