SOAR Features and Use Cases

Organizations are getting bigger and bigger and, because of that a lot of events, activities and data are being generated and triggered, and the scale of these events sometimes reaches to a peak, where analysts are not able to handle them anymore.
For the purpose of having control and visibility over the system events, logs and other valuable data that may indicate anything related to compromise or unwanted actions, companies are heavily integrating their infrastructures with solutions like Security Information and Event Management (SIEM), as well as creating Security Operations Center with skilled SOC Analysts to monitor and analyze all this as well as alert/notify and even prevent malicious activities. This all sounds great, but as Security Operations Center and SIEM Solution became popular, security researchers understood that very frequently SOC Analysts are forced to perform daily identification, remediation, containment, recovery actions that can be easily automated, and as this is not automated yet in most of the companies, SOC Analysts are wasting hours and hours to do tasks that are common and repetitive, additionally this may push away the analyst from real threats, because of being distracted with tasks that can be automated. As the problem of automation has raised, security researchers have created a solution called SOAR.
Introduction:
SOAR stands for Security Orchestration, Automation, and Response
SOAR has the capability and features of threat and vulnerability management, security incident response and security operations automation. SOAR allows companies to collect threat-related data from a range of sources and automate responses to low-level threats. Tasks which were performed by SOC Analysts such as analyzing IP address reputation, blocking suspicious IP address, isolating virtual machine from network, and many other tasks can be automated if the appropriate digital playbook is created and implemented.
In a short SOAR integrates all of the tools, systems and applications within an organization’s security toolset and then enables the SOC team to automate incident response workflows. SOAR’s main benefit to a SOC is that it automates and orchestrates time-consuming, manual tasks, including opening a ticket in a tracking system, such as Jira, without requiring any human intervention, which allows engineers and analysts to better use their specialized skills.
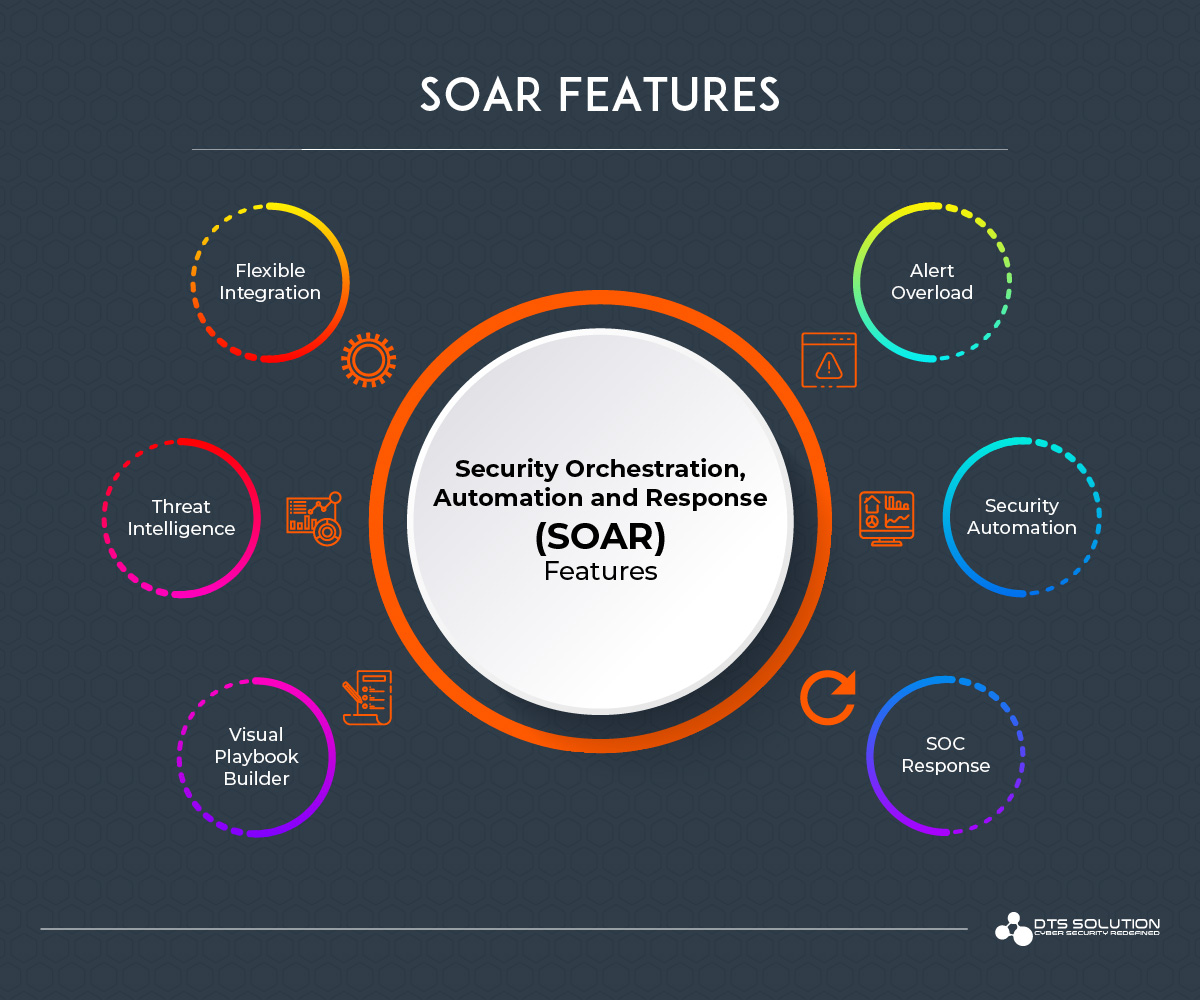
SOAR Features:
- Alert Overload: A SIEM may generate so many alerts that analysts can’t keep up. By automating the response to many alerts, SOAR helps to prevent SOC personnel from becoming overwhelmed and suffering alert fatigue.
- Lack of Talent: Good SOC Analysts are hard to find. And when you do hire them, you do not want to waste their time and skills on tedious, repetitive security tasks. SOAR automates those tasks so that engineers are free to focus on more complex issues and make the most of their expertise.
- SOC Response: SOAR serves as a central station for the SecOps team to monitor and respond to alerts, as well as to communicate and collaborate on a response. To minimize the risk of breaches and limit the vast damage and disruption they can cause, rapid response is vital. SOAR helps organization to reduce mean time to detect (MTTD) and mean time to respond (MTTR) by enabling security alerts to be qualified and remediated in minutes, rather than days, weeks and months.
- Visual Playbook Builder: Create smart automated workflows with ease of product integrations, convert your playbooks into digital playbooks with ease and automate the tasks.
- Delivering better quality intelligence: Tackling the latest sophisticated cyber security threats requires an in-depth understanding of attackers’ tactics, techniques, and procedures (TTPs) and an ability to identify indicators of compromise (IOCs). By aggregating and validating data from a wide range of sources, including threat intelligence platforms, exchanges, and security technologies such as firewalls, intrusion detection systems, SIEM and UEBA technologies, SOAR helps SOCs to become more intelligence-driven. The effect of this is that security personnel are able to contextualize incidents, make better informed decisions and accelerate incident detection and response.
- Flexible Integration: The ability of SOAR Solution to integrate within your environment is wonderful, as the vendors of SOAR products have done a great job to make the process of connecting various security tools or assets to SOAR product easy and manageable.
SOAR Use-Cases:
SOAR use cases can vary depending on several factors, such as the internal environment of organizations, the industries they cater to, the security processes and workflows in place, the problems their security team is trying to solve for, and the regulatory compliance that needs to be ensured.
Following are some of the real-world SOAR use cases:
- Denial-of-Service (DoS) Alert Mitigation – From detection to blocking of the malicious indicators, automation helps in effectively breaking the chain of Denial-of-Service (DoS) attacks by standardizing the response process. In this SOAR use case, automation can perform tasks such as ingestion of threat alerts, triaging and analysis, and response actions to DoS alerts.
- Ransomware Alert Response – Ransomware attacks can be contained in their early stages with the help of SOAR-driven response processes. Ransomware alert response has gained prominence as one of the important SOAR use cases where in a ransomware alert is received from a SIEM tool, following which an incident is automatically created and investigated. The SOAR platform can then gather the host and user information and coordinate it with previous investigations, connecting the dots between different threat aspects. On completing the initial triage, a SOAR platform can initiate containment actions to determine the aftermath and extent of the ransomware attack, followed by response and remediation.
- Web Defacement Response – Security teams can utilize SOAR platforms to automatically detect and respond to web defacement attacks. Upon receiving an alert about website defacement from a third-party website monitoring service provider, an incident can be automatically created in a SOAR platform
Using SIEM and SOAR as Combined Force:
Both SIEM and SOAR solutions are complementary and together they can highly increase the potential of Security Operations Center, by improving the lives of the entire security team, from the analyst to the CISO, as it increases the efficiency of the SOC and the ability to mitigate incident from the organization. While the collection of data is incredibly meaningful, SIEM solutions tend to produce more alerts than SecOps teams can expect to respond to while still remaining effective. SOAR enables the security team to handle the alert load quickly and efficiently, leaving time for important, skills-based tasks which results in a higher-performing SOC.
How Is Automation Being Used In SOAR:
Automation supports numerous key activities that map into the overall security life cycle as defined by the phases in the NIST Cyber Security Framework (CSF). In an organization where Security Orchestration, Automation and Response is not implemented, the responsibility of mitigating and responding to low or mid-level incidents lays on the shoulders of IT Administrators and overall IT Team, in best scenarios companies dedicate time and budget to create and train incident response teams that will respond to an incident if it occurs.
In order to properly respond to an incident there is a need of a clear step-by-step guidance that will indicate and show how can an incident be treated and how incident response team can mitigate it. In professional field we call this step-by-step approach as incident response plan or playbook, which is created by security professionals and provided to incident response teams. The playbooks are based on use-cases which are very diverse, for example if the company is interested into how to mitigate the environment from a ransomware attack, then steps are created within playbook to process with. An incident response plan should be set up to address a suspected data breach in a series of phases. Within each phase, there are specific areas of need that should be considered.
The incident response phases are:
- Preparation – This is the firs phase in incident response plan, and this phase is responsible for providing information on how to prepare for the particular use-case, what kind of solutions to deploy implement, what kind of hardening, configuring and other activities to perform to be ready for the incident.
- Identification – This is the process where you determine whether you have been breached. A breach, or incident, could originate from many different areas. It provides the necessary sources and methods to perform analysis which will help to identify the incident.
- Containment – When a breach is first discovered, your initial instinct may be to securely delete everything so you can just get rid of it. However, that will likely hurt you in the long run since you will be destroying valuable evidence that you need to determine where the breach started and devise a plan to prevent it from happening again. Instead, contain the breach so it doesn’t spread and cause further damage to your business. If you can, disconnect affected devices from the Internet. Have short-term and long-term containment strategies ready. It’s also good to have a redundant system back-up to help restore business operations. That way, any compromised data isn’t lost forever.
- Eradication – Once you’ve contained the issue, you need to find and eliminate the root cause of the breach. This means all malware should be securely removed, systems should again be hardened and patched, and updates should be applied. Whether you do this yourself, or hire a third party to do it, you need to be thorough. If any trace of malware or security issues remain in your systems, you may still be losing valuable data, and your liability could increase.
- Recovery – This is the process of restoring and returning affected systems and devices back into your business environment. During this time, it’s important to get your systems and business operations up and running again without the fear of another breach.
- Aftermath – Once the investigation is complete, hold an after-action meeting with all Incident Response Team members and discuss what you’ve learned from the data breach. This is where you will analyze and document everything about the breach. Determine what worked well in your response plan, and where there were some holes. Lessons learned from both mock and real events will help strengthen your systems against the future attacks.
As was said already incident response team walks through each phase and performs actions accordingly and here is the catch – With the help of SOAR solution the following can be automated which will extremely help the SOC analysts to concentrate on more important and valuable tasks. Playbooks that are created can be converted to Digital Playbooks.
Digital Playbooks allow you to automate your security processes across external systems while respecting the business process required for your organization to function. Playbook templates can be customized to follow an organization’s current procedures while leveraging the automation capabilities of SOAR. By using Digital Playbooks and integrating them with security tools, the incident response plan can be automated and performed rapidly.
Things to Keep on Mind:
It is crucial to mention that SOAR solution is not a replacement for skilled professionals that are experts in security operations. SOAR is intended to ease the task of the analyst, but not replace it, because any kind of security operations solution would be meaningless without appropriate expert who would configure, analyze, and monitor the activities. For example, SOAR solution is not efficient at all if the skilled analyst has not configured it and has not deployed set of tasks, playbooks that will trigger in case of alert or condition. SOAR is a solution for mitigating security threats through automation which is programmed to collect data about security threats from various sources and respond quickly to the low-level security events without human assistance.