The Basics of Threat Hunting

Forms of Threat Hunt
The truth is that threat hunt end goal plays an important role in the whole classification of the type of the hunt. Hunt events start with a concrete goal to discover specific actors—which classifies this type of hunt as a threat focused. Likewise, an environmental hunt engagement focused on learning a particular subset of the overall environment from a technical angle. Classifying the type of a threat hunt is as essential as the type of threat hunt changes the TTP and data sources required to conduct the hunt. A hunt might also start as an environmental hunt and might change into a threat-focused hunt as any malicious activity be discovered.
Both types of hunts are essential to an organization to keep a complete threat hunting program ecosystem. Threat focused hunts focus on known adversary behavior and can verify the presence of known actor TTP in the landscape. Environmental focused threat hunts may pick a specific protocol or known source and look for malicious behaviors not yet associated with an actor TTP.
Whilst the hunt search at data related to a specific attack TTP, no setting exists surrounding a known malicious actor. When hunting for complex attackers, a threat- focused hunt that contains known intelligence about a particular attacker might be tailed by an environmental hunt to look for possible development in the attacker TTP or unknown attacker TTP.
Components of a successful threat hunt
Threat Hunting Playbooks
In the basic way, a playbook provide an analyst with a checklist of tasks to follow and execute. In the context of a threat-focused hunt, a hunting playbook may center the threat hunting process on specific recognizable actions related to known attacker TTP. For environment hunts, a hunting playbook may have a larger possibility to reveal malicious activity inside a larger set of data. Threat hunting playbooks might follow a arrangement analogous to incident response playbooks.
Incident response method provides pre-established actions that facilitate responders to rapidly counteract attackers within the network (NIST, 2016). In this sense, threat hunt playbooks offers pre-established actions for adversary discovery. A playbook should not, however, restrain the ingenuity and analytical mind of the threat hunter. Whilst an analyst should complete all steps of a particular playbook to guarantee the integrity of the hunt, the analyst should also be encouraged to investigate outside the box beyond the playbook tasks grounds. If an analyst finds an unusual or effective methodology beyond the defined scope of the playbook, the analyst should be encouraged to revise or update the playbook with the new methodology.
Threat Intelligence
Threat intelligence delivers one source of context for scoping the attention of a threat hunt through the analysis of a particular attacker’s TTP.
Events assist as a central component and capture the use of a capability or skills by an adversary over a particular infrastructure against a victim. The four major components, adversary, capability, infrastructure, and victim allow analysts to develop a full picture of a particular intrusion.
“The Diamond Model for Intrusion Analysis,” an approach describe in-depth attacker intrusions that provide a model for classifying attacker behavior is the foundation for identifying attackers, their victims, the infrastructure targets, and capabilities. Ultimately, this provides threat intelligence with a way to take attacker tradecraft and form TTP for threat hunts. In addition to TTP, threat hunts use this model to identify relevant data sources for an investigation.
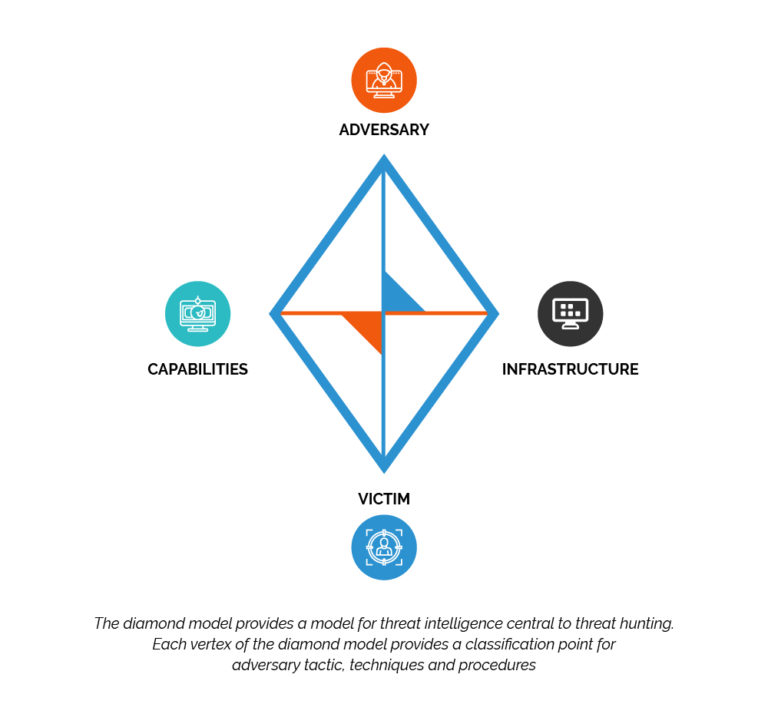
Figure 1. The Diamond Model for Intrusion Analysis
The adversary and victim center on the intent of the activity group execution attacks against a single victim or multiple victims. The adversary does not attribute the attack to a particular nation, group, or individual but instead looks at the intent of the attack. In the context of threat hunting, a threat hunt may decide to focus on attacks within a particular sector.
The infrastructure describes the set of systems an attacker uses to launch attacks against a given victim. Indicator-based defense approaches build indicators from sources such as internet protocol (IP) addresses and domain names. IP addresses and domain names both serve as indicator based descriptors for attack infrastructure. For attackers that exploit and use botnets, the attack infrastructure would consist of all types of machines within the botnet. The infrastructure vertex, however, should not exclusively comprise of indicators. Threat intelligence should also provide awareness into attacker behavior. For example, an attacker may use encoded DNS messages for C2. The infrastructure vertex may consist of the IP addresses connected with the DNS servers but can also contain some of the unique C2 behaviors related with the attacker’s infrastructure TTP.
The capability develops from known attacker intrusion tools and techniques. Obtaining this knowledge regularly comes from threat intelligence. Threat hunts make use of this intelligence to center on data collection to sources with the potential to discover attacker tools and techniques.
Kill Chain ATT&CK model
One mode to analyze the phases of attack involves the analysis of attacker actions throughout the cyber kill chain. Cyber Kill Chain is a framework that delivers one means to model attacker action across the range of common attack steps. An alternative to the Kill Chain is MITRE’s ATT&CK model. Both models pursue to outline and classify the overall actions that adversary does during an attack. By classifying actions, the analysts can identify attack behaviors that may fit into a particular phase of each model. The same analysis can be used to evaluate the a threat hunt by guaranteeing that the hunt focuses on the full range of attacker action.
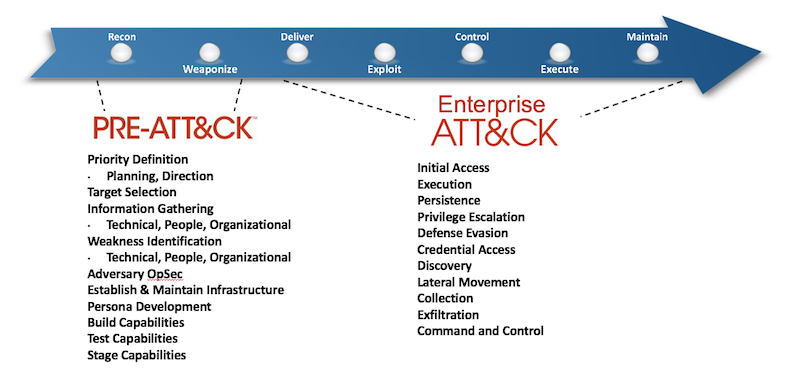
Figure 2. The Cyber Kill Chain and MITRE ATT&CK
Hunt Cycle Model in the Field
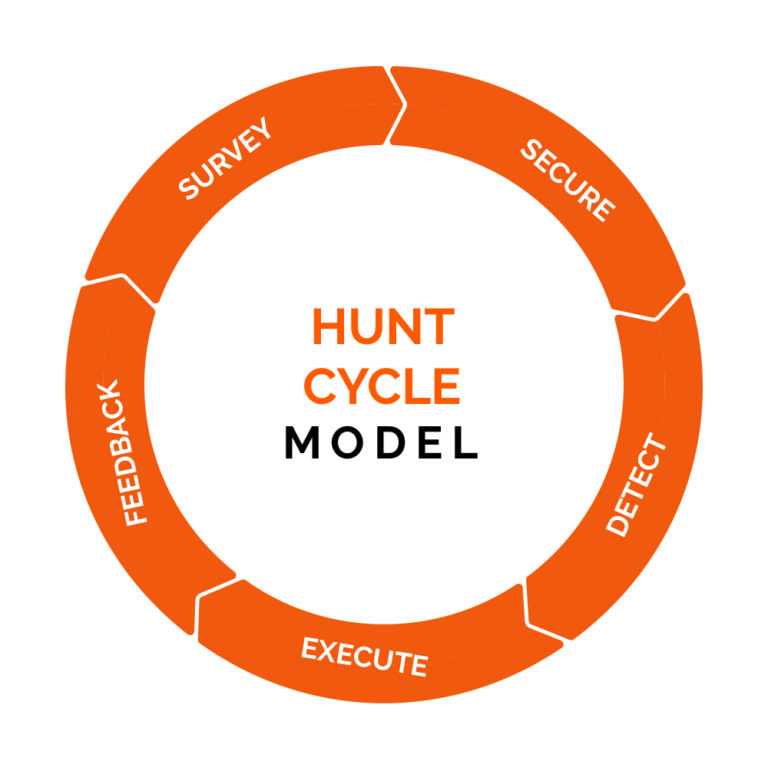
Survey
In this phase the main goal is to discover assets in the environment, determine which assets an adversary is most likely to target, and deploy sensors to assets to monitor them and collect data on any malicious activity.
Secure
Lock down the monitored assets to ensure threats already in the environment are prevented from moving laterally and gaining further access. The secure phase also prevents execution of new malware and other exploit.
Detect
Use the hunt sensors’ automated detection and data collection capabilities to find evidence of successful and failed attacks, and identify adversaries by analyzing the collected data.
Execute
Stop the attack by disrupting the adversary’s access and preventing it from being regained, repair damage to compromised assets, and inform the appropriate personnel of the actions taken by the hunters and the weaknesses that still need to be addressed.
Feedback
Strength and shortcoming analysis should occur for each phase in the threat hunt model in the form of a feedback. A finding for the feedback out of the threat hunt might identify the need for an internal development team to develop additional IEC 60870-5-104 analysis tools. If no internal development team exists, a tool might be purchased to fill the gaps. The feedback stage might also identify deficiencies in hypotheses or data sources identified in the hunt phases.
Organizations that use a threat hunting model process increase the ability to measure the entire coverage of a hunt. By associating the evidence the hunt investigated within available data sources related with known attacker TTP, it is likely to compute the total coverage of the hunt.
Every phase in the model plays a fundamental step essential for the complete threat hunt process. Moreover, the model shapes a framework for the various stakeholders involved in a hunt to provide and add to the successful results.
In conclusion, a threat hunting model delivers a complete and dedicated methodology for discovery adversary TTP inside the organization’s environment. By exercising the threat hunting model, the general outcomes of the hunt better track the purpose and reserve analytic integrity.