CISA Warning: CVE-2024-38856 Apache OFBiz RCE Vulnerability under active exploitation

Background
A pre-authentication vulnerability in Apache OFBiz can result in remote code execution. With a CVSS score of 9.8, the vulnerability tracked as CVE-2024-38856 is rated as critical severity. SonicWall found the issue and notified Apache of it. If the vulnerability is successfully exploited, an attacker might be able to remotely run any code, which would compromise the system entirely.
Additionally, SonicWall uncovered CVE-2024-36104, an unauthenticated RCE employing path traversal, and CVE-2024-38856 is a patch bypass for it. The vulnerability was fixed by Apache in June.
By adding CVE-2024-38856 to its list of known exploited vulnerabilities and advising users to fix the vulnerability by September 17, 2024, CISA confirmed that the vulnerability is being exploited actively.
CVE-2024-38856:
A SonicWall security researcher noted in their blog that the authentication method is vulnerable. Path traversal attack vector tests were included in the patch that fixed CVE-2024–36104.
In theory, the ControlServlet and RequestHandler methods should receive the same endpoint, however they actually receive distinct endpoints. By delivering a raw URL, such as POST /webtools/control/forgotPassword/ProgramExport, without any path traversal vector, an attacker can take advantage of this vulnerability and avoid authentication.
By chaining the ProgramExport endpoint with other endpoints that don’t require authentication, an attacker may be able to access it without authorization. Among the URLs that may be used maliciously are:
- /webtools/control/forgotPassword/ProgramExport
- /webtools/control/main/ProgramExport
- /webtools/control/showDateTime/ProgramExport
- /webtools/control/view/ProgramExport
- /webtools/control/TestService/ProgramExport
Active exploitation:
Organizations must move quickly to address the CVE-2024-38856 issue since proof-of-concept (PoC) exploit scripts and scanners are readily available to the public.
Attackers can swiftly turn these flaws into weapons, which could result in large-scale malicious activity. Effective vulnerability management necessitates ongoing observation of CVEs and exploitation trends.
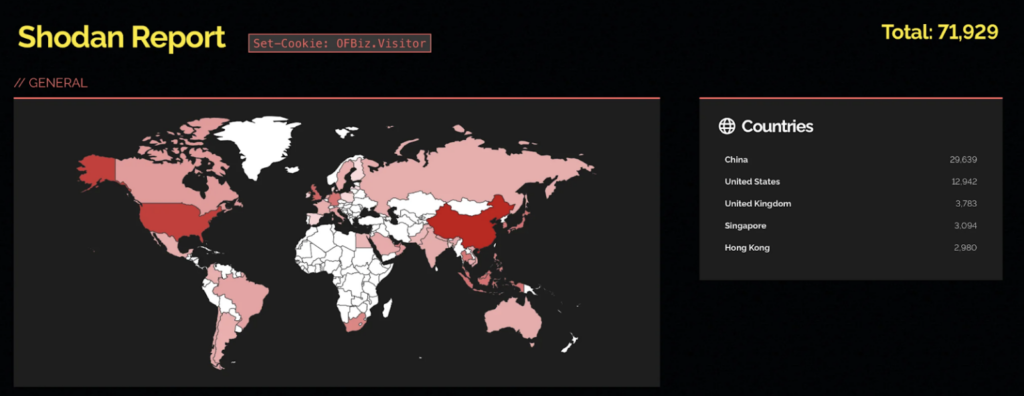
GitHub has an example of both a scanner and an exploit. Furthermore, the possible attack surface is indicated by the discovery of roughly 72,000 vulnerable Apache OFBiz instances by a Shodan search.
Recent Exploitation Trends and CISA’s Response
The Apache OFBiz CVE-2024-38856 vulnerability has been actively abused in the wild since it was first discovered. The vulnerability, which was first identified by SonicWall, enables threat actors to get around authentication procedures and compromise systems. The threat has been further intensified by the availability of Proof-of-Concept (PoC) exploit scripts on websites like GitHub, which makes it simpler for attackers to target unpatched systems.
On August 28, 2024, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) added CVE-2024-38856 to its list of known exploited vulnerabilities (KEVs) after realising how serious this problem was. This inclusion emphasises how serious the vulnerability is, especially considering that federal entities must implement updates by September 17, 2024, in order to reduce the likelihood of exploitation.
Considering the ongoing exploitation and possible incorporation into more extensive attack activities, like botnet operations like Mirai, enterprises must give top priority to patching and updating to Apache OFBiz version 18.12.15 in order to prevent any system breaches.
Affected versions:
Versions of Apache OFBiz prior to 18.12.15 are susceptible to the vulnerability.
Recommendations:
Upgrading to version 18.12.15 is highly recommended for organizations in order to reduce this serious security risk. The Apache OFBiz website’s Downloads page has the most recent upgrades and release details.
Visit the official research blog for further information and an investigation of the vulnerability’s fundamental cause.