Leveraging DETT&CT Framework
November 3, 2023
Building detection is a difficult task, particularly with an increasing number of data sources. It might be challenging for detection engineers to keep track of numerous data sources and the necessary detection rules for them, or to avoid creating duplicate detection rules that cover the same techniques.



Background:
To identify gaps, give new detection rule development top priority, or integrate new data sources, a SOC must have a clear picture of its visibility and detection coverage in practice. This is where a tool like DeTTECT, in conjunction with ATT&CK, comes into play.ATT&CK:
MITRE ATT&CK is a knowledge base of adversary TTPs used by adversaries against enterprise networks that are based on actual observations. While ATT&CK covers some of the tools and software used by attackers, the framework mainly emphasizes how adversaries interact with systems to achieve their goals. ATT&CK consists of a group of tactics that are made up of a number of techniques and sub-techniques. The tactical purpose of an adversary for a certain action serves as the “why” of an ATT&CK approach. To obtain initial access, maintain persistence, move laterally, exfiltrate data, and other tactical goals. These tactics and techniques are represented in a matrix containing, at the time of writing, 14 tactics and 188 techniques.
Fig. MITRE ATT&CK matrix
DETT&CT:
DeTTECT is a free software program found on GitHub at https://github.com/rabobank-cdc/DeTTECT. Its goal is to assist SOC teams in comparing the quality of their data logging sources to the MITRE ATT&CK matrices in order for them to quickly determine whether they have the necessary logging coverage to be able to detect adversaries, depending on the tactics they may be employing. DeTTECT’s ability to accomplish this in an intelligible manner due to its strong visual component is what makes it so valuable. This can help you comprehend how to strengthen your organization’s logging for the several threats you might encounter. For instance, you might be logging traffic through your web proxy but not through your email gateway. By not importing those logs into Azure Sentinel, you can lose out on a very useful intelligence source for your threat detection. You can map the data you already have in your organization to the ATT&CK entities. You may manage the data sources, visibility, and detection for your blue team with the help of the framework DeTT&CT provides. Additionally, it will give you the tools you need to manage threat intelligence that you receive from your own intelligence team or a different source. Then, compare this to the detection or visibility coverage you now have. Functionalities: DeTT&CT provides a framework that can assist you in managing your blue teams’ data, visibility, and detection coverage by mapping the information you have on the entities accessible in ATT&CK. The DeTT&CT framework is made up of various components, including:- a Python tool (DeTT&CT CLI)
- YAML administration files
- the DeTT&CT Editor (to create and edit the YAML administration files)
- scoring tables for detections, data sources, and visibility
- Data sources administration
- Technique administration (visibility and detection coverage)
- Groups administration

Fig. Data source quality scoring table
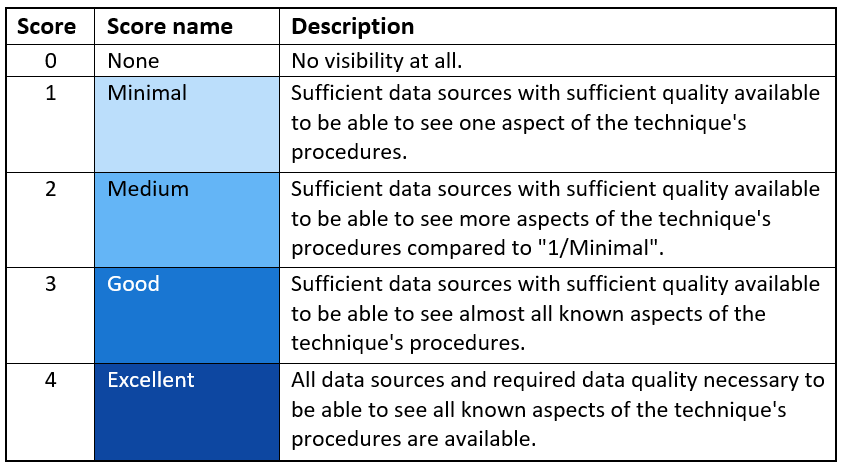
Visibility: DeTT&CT uses visibility to determine whether you have access to enough reliable data sources to be able to gather proof of actions related to ATT&CK procedures. To respond to incidents, carry out hunting investigations, and develop detections, visibility is essential. You can rate the visibility coverage according to the ATT&CK approach in DeTT&CT.
Fig. Visibility scoring table
Detection: Your visibility can be utilized to develop novel detections for ATT&CK procedures, but only if you have access to the appropriate data sources with sufficient data quality. Detections frequently result in alerts, therefore your blue team investigates them.
Fig. Detection scoring table
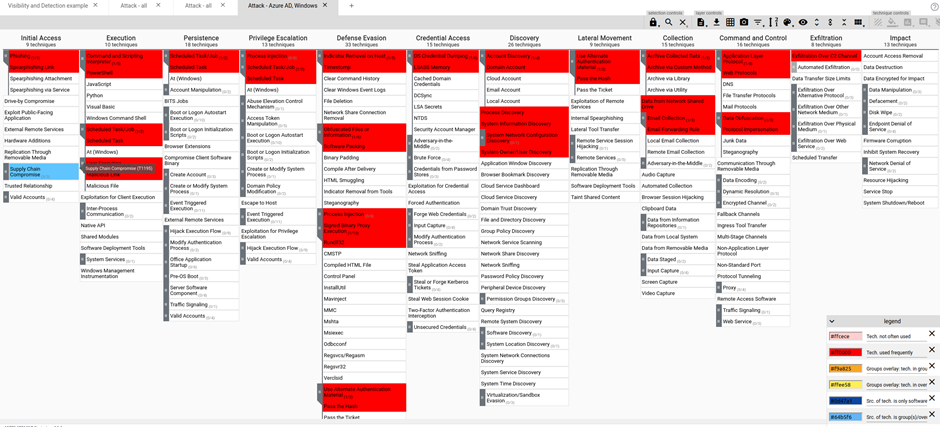
Gap analysis: To identify any gaps in your detection, you might also compare your detection layer to your threat analysis layer or to a layer created for a particular red team activity. The red team will specify a range of tactics that imitate a recognized threat to an organization when executing adversary simulation. They typically create an ATT&CK matrix layer to illustrate this scope.
Fig. ATT&CK Red team layer