Ransomware Incident Response Plan – Part 2
Ransomware was and still is one of the most dangerous attacks that can cause catastrophic consequences to the endpoint system if not responded properly. The following article is specially created for preparing incident response teams against this particular attack, but it is generally excellent guidance for everyone who would like to have clear and step-by-step approach on how to prepare, identify, contain, remediate and recover from the dangerous attacks of ransomware.
The following is part two of the overall incident response plan where we are going to discuss in our opinion the most important phases of the incident response plan, which are the containment and remediation phases. Before jumping into the phases and steps we would like to give brief recap about ransomware, to explain what it is and how does it work.
Ransomware is a type of malware from crypto virology that threatens to publish the victim’s data or perpetually block access to it unless a ransom is paid. While some simple ransomware may lock the system in a way which is not difficult for an expert to reverse, more advanced malware uses a technique called crypto viral extortion, in which it encrypts the victim’s files, making them inaccessible, and demands a ransom payment to decrypt them.
In a properly implemented crypto viral extortion attack, recovering the files without the decryption key is an intractable problem and difficult to trace digital currencies such as Ukash or Bitcoin and other cryptocurrency are used for the ransoms, making tracing and prosecuting the perpetrators difficult.
Containment Overview:
After the identification phase, if any malicious/suspicious activity was detected we can assume that there is a big chance that there is a presence of a malware on the endpoint, hence the endpoint must be quarantined and isolated from the network, to stop the spread to other endpoints and overall infrastructure.
As we are talking about the ransomware, we must be extremely careful in this case, because the process of system corruption and encryption will not take much time, hence the time is limited. Having an endpoint protection system that can look for the execution and kill the process is usually the best means of containment.
Carefully document and report the performed activities, this will help to detect the virus/malware on other IT systems as well. Examine all endpoints that may be vulnerable or exposed to that particular attack, perform identification phase on the endpoint and in case of anomaly detection isolate the system.
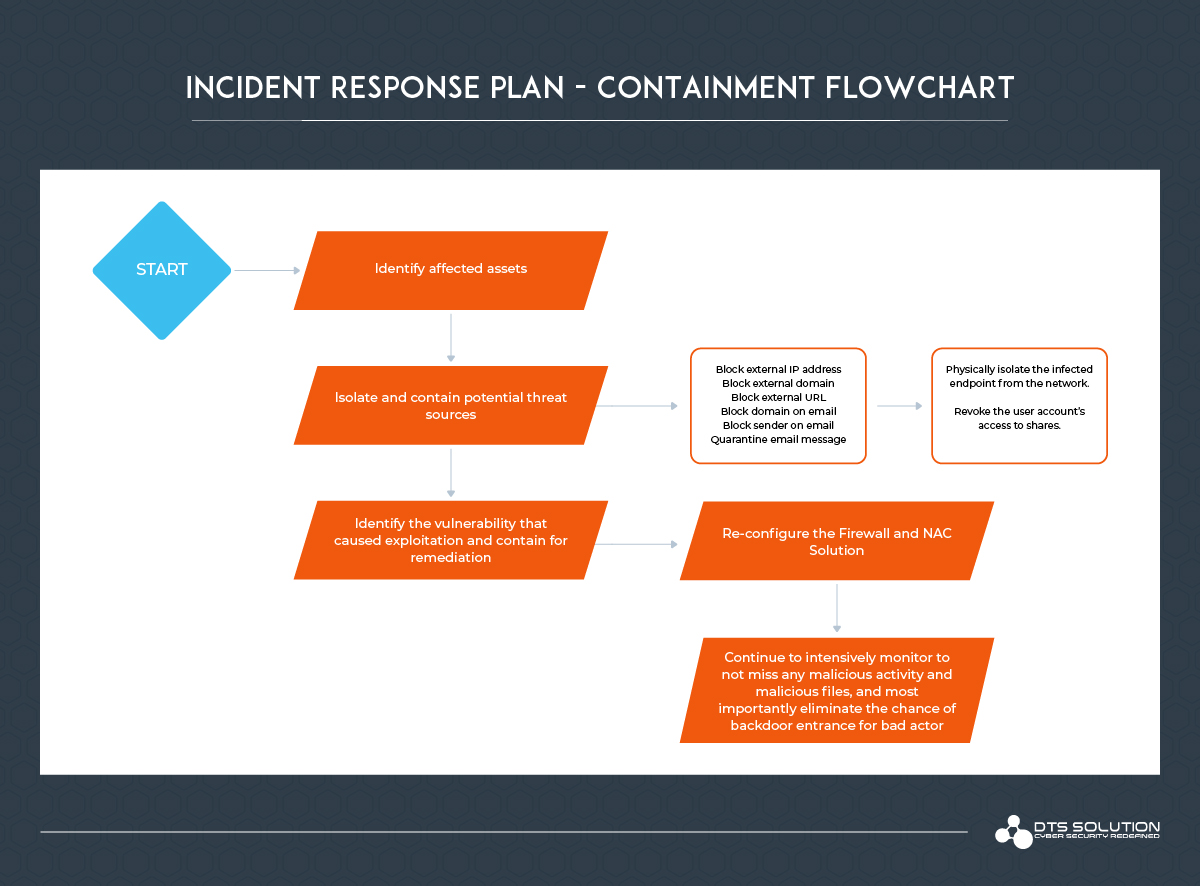
Containment Hands-On:
- Identify affected assets and perform containment, you must ensure that any communication with the affected device and potential threat source is isolated and contained, for that purposes the following is recommended:
- Block external IP address
- Block external domain
- Block external URL
- Block domain on email
- Block sender on email
- Quarantine email message
- As you have identified the user that potentially encrypted:
- You now have two steps to perform immediately:
- Physically isolate the infected computer from the network.
- Revoke the user account’s access to shares.
- You now have two steps to perform immediately:
- Isolate the system to prevent spread, if possible, disconnect from network.
- Completely disconnect the network cable from the infected host and eliminate any kind of connection to stop the spread.
- No need to turn of the host, as it will not prevent anything, instead ensure that file modifications are alerted and prevented by appropriate cyber solutions such as DLP and FIM.
- Re-configure the Firewall and NAC Solution as well as host-based firewall to block the connection with the internal network for temporary purposes, until full identification process is done, and malicious C&C is detected and disconnected as well as the malware that caused ransomware and backdoors most importantly.
- Identify the vulnerability that caused exploitation and contain for remediation.
- Continue to intensively monitor to not miss any malicious activity and malicious files, and most importantly eliminate the chance of backdoor entrance for bad actor.
- Perform documentation and inform stakeholders, users about the incident, and share the documentation to prevent the spread and isolate all other assets that may be infected.
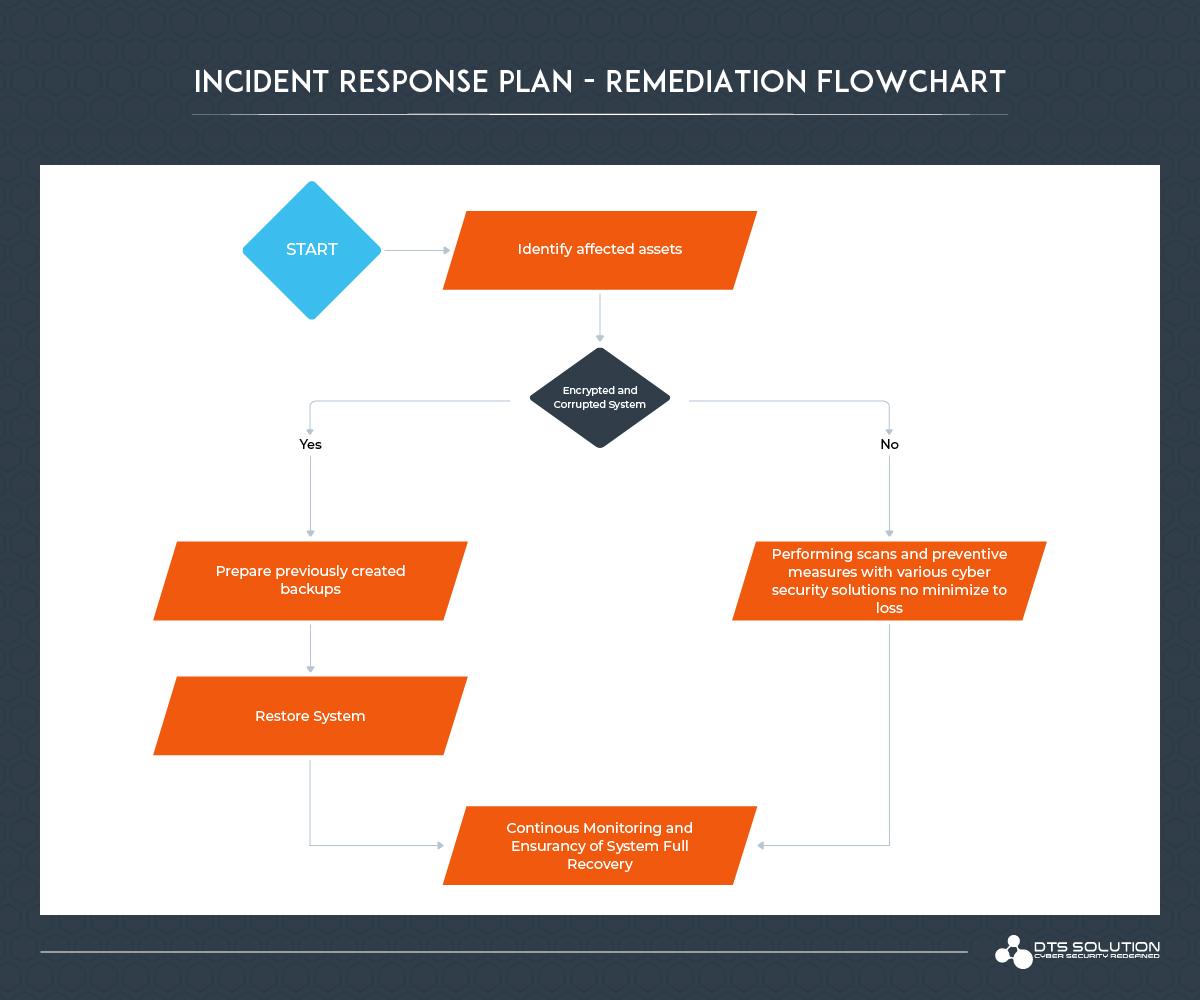
Remediation Overview:
To eradicate the ransomware from IT environment, the ransomware must be identified by the anti-virus various malware removal tools, or manually through registries and by identifying abnormal file extensions, if the threat is advanced manual intervention may be needed to quarantine these files and clean from the system.
If the malicious file is not detected by signature-based detection, the file can be given to the sandbox for more effective detection as all ransomwares are malwares as well, but all of these can be done in case the ransomware was detected on the earliest phase. Usually, the recommend practice is to replace compromised machines rather than clean them.
The main reason for replacement is that it is difficult to know if residual files of the ransomware are still on the system and able to re-infect devices. If you choose to clean rather than replace, continue to monitor for signatures and other IOCs to prevent the attack from re-emerging.
Remediation Hands-On:
- Identify affected asset and start remediation
- If the system is encrypted and corrupted already then
- Restore the system from previously prepared and created backup and restore the system to ideal state.
- If the system is not yet corrupted and encrypted, then:
- Immediately perform the scans and identification steps by isolating and checking the system until the identified and remediated.
- Still, it is highly recommended to restore to the last available ideal backup, because if the remediation step is not completed accurately and completely, there is a high chance that there will be malicious files left on the system that may cause backdoor for an attacker.
- Continue Log Monitoring and Validation of recovered system and ensure that system is fully remediated.
- It is crucial that incident response team report incident to all employees, stakeholders and others who may be affected or may be under the risk of being affected.
- Finally, if the incident had occurred because of a malicious email then delete the email message.