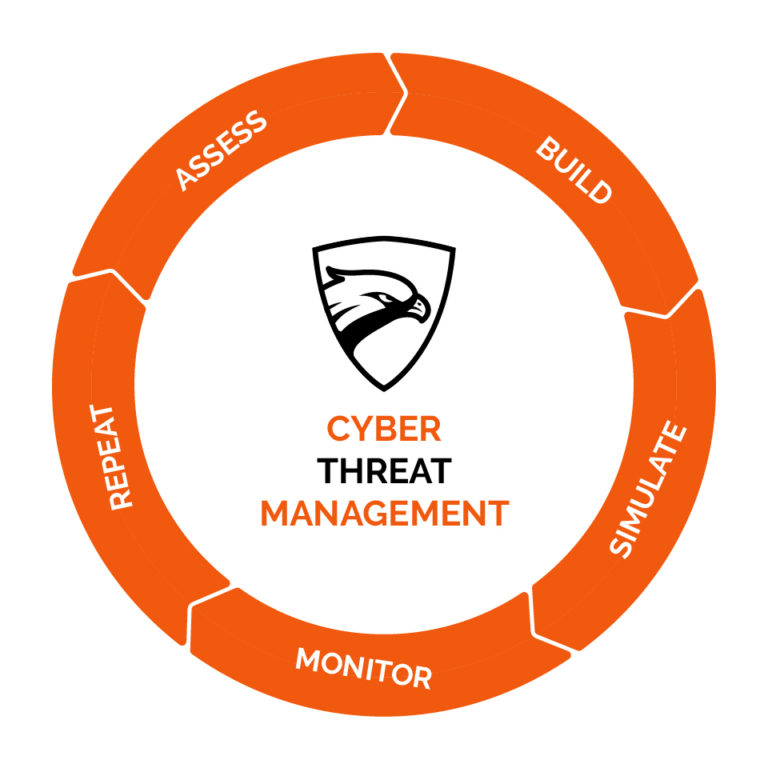
Cyber Threat Management with MITRE ATT&CK – Part 1

Let’s agree on this first, job of a SOC analyst is TOUGH, as tough as finding a needle in a haystack. Threat hunters are mostly presented with thousands of logs and telemetry data every second and are supposed to identify threat adversaries from this pool of information. This is one challenge which can fatigue both the human and machine intelligence.
There are many frameworks designed to help SOC analysts tackle this situation in different ways. Within our cyber threat research team at HAWKEYE, which consists of RED, BLUE and PURPLE team members, the effectiveness of all these frameworks are often debated. (At the end such debates bring us the best results). There is one framework which we unanimously agree up on and that’s MITRE ATT&CK vs. all the other Cyber-Attack Kill Chains.
So, What is MITRE ATT&CK?
MITRE ATT&CK is a comprehensive matrix of adversary tactics and techniques designed to help SOC analysts and threat hunters classify the threat adversaries and effectively detect the attacks in various stages. In short, it helps to make large pile of hay in to smaller piles based on type of needle you are searching for.
All the tactics and techniques are based on real world scenarios and accumulated over years (actual malware, viruses, trojans, exploits and so on). So, it covers most if not all of the known attack techniques.
Detection In-Depth
Attacks do not happen in just one step. A typical cyber-attack lifecycle passes through various stages from initial access through persistence to the actual impact.
MITRE ATT&CK classified attacks according to the stage and provides various techniques to detect attacks in each of these stages. Even if the attack has evaded the detection system in the first stage, it can still be identified and remediated in later stages as long as you know how to do that.
Each stage has a list of all known tactics and techniques used by adversaries and procedures to detect them. If the SOC is configured to detect attacks in all these stages, there is rare possibility that an attacker can pass through the attack life cycle without detection. Not all attacks pass through all these stages, so it’s imperative to have all the procedures followed and detection rules to be configured for each tactic.
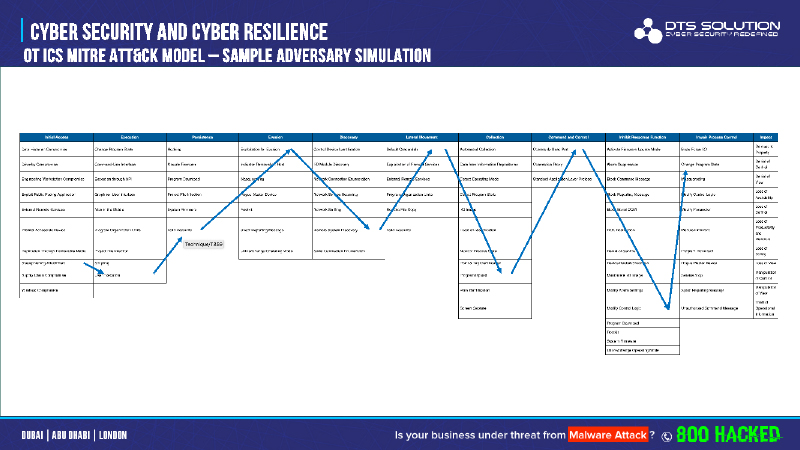
An example of a real-world cyber-attack scenario is shown below; where each technique being executed across the different stages / tactics of the cyber-attack lifecycle to eventually cause business loss or damage.
Tactics:
Tactics are the different stages in the attack lifecycle. MITRE ATT&CK shares five types of tactics used by adversaries.
PRE-ATT&CK Tactics:
List of all tactics which are used by attackers to identify the target and information gathering. Example are target selection, technical information gathering, technical weakness Identification, etc.
Enterprise Tactics:
This are the tactics for the actual attack from initial access to the network till the impact and covers Windows OS, Linux and MAC OS systems.
Mobile Tactics:
Similar to Enterprise Tactics, this is the list of tactics specific to mobile devices to compromise and network.
Cloud Tactics:
Similar to Enterprise Tactics, this is the list of attack tactics specific to cloud service provider environments (AWS, Azure, Office365, Azure AD, GCP and other forms of IaaS, PaaS and SaaS).
ICS (Industrial Control Systems) Tactics:
Similar to Enterprise Tactics, this is the list of attack tactics specific to critical infrastructure (power plants, water desalination, oil and gas, aviation, airports, manufacturing etc.) or what is known as Industrial Control Systems (ICS). These set of attach tactics are aimed specifically to cause disruption to an industrial process and in turn cause major impact to society.
Tactics of MITRE ATT&CK Matrix:
Tactic | Description |
| Initial Access | This stage is the most lethal one for attackers where they obtain access to the network. All attack technics must pass though this stage. It can be a phishing email, orphaned USB Drive found in the backyard, Accidental disclosure of Information on Internet or Social media, etc. I would say, Security team must invest most of their resources to prevent attacks from passing the Initial access stage. Solutions like a well configured Perimeter Firewall, User Security Awareness and Email security systems are examples. |
| Execution | Execution consists of techniques that result in adversary-controlled code running on a local or remote system. Techniques that run malicious code are often paired with techniques from all other tactics to achieve broader goals, like exploring a network or stealing data. For example, an adversary might use a remote access tool to run a PowerShell script that does Remote System Discovery. |
| Persistence | Persistence consists of techniques that adversaries use to keep access to systems across restarts, changed credentials, and other interruptions that could cut off their access. Techniques used for persistence include any access, action, or configuration changes that let them maintain their foothold on systems, such as replacing or hijacking legitimate code or adding startup code. |
| Privilege Escalation | Privilege Escalation consists of techniques that adversaries use to gain higher-level permissions on a system or network. Adversaries can often enter and explore a network with unprivileged access but require elevated permissions to follow through on their objectives. Common approaches are to take advantage of system weaknesses, misconfigurations, and vulnerabilities. Examples of elevated access include:
These techniques often overlap with Persistence techniques, as OS features that let an adversary persist can execute in an elevated. |
| Defense Evasion | Defense Evasion consists of techniques that adversaries use to avoid detection throughout their compromise. Techniques used for defense evasion include uninstalling/disabling security software or obfuscating/encrypting data and scripts. Adversaries also leverage and abuse trusted processes to hide and masquerade their malware. Other tactics’ techniques are cross-listed here when those techniques include the added benefit of subverting defenses. |
| Credential Access | Credential Access consists of techniques for stealing credentials like account names and passwords. Techniques used to get credentials include keylogging or credential dumping. Using legitimate credentials can give adversaries access to systems, make them harder to detect, and provide the opportunity to create more accounts to help achieve their goals. |
| Discovery | Discovery consists of techniques an adversary may use to gain knowledge about the system and internal network. These techniques help adversaries observe the environment and orient themselves before deciding how to act. They also allow adversaries to explore what they can control and what’s around their entry point in order to discover how it could benefit their current objective. Native operating system tools are often used toward this post-compromise information-gathering objective. |
| Lateral Movement | Lateral Movement consists of techniques that adversaries use to enter and control remote systems on a network. Following through on their primary objective often requires exploring the network to find their target and subsequently gaining access to it. Reaching their objective often involves pivoting through multiple systems and accounts to gain. Adversaries might install their own remote access tools to accomplish Lateral Movement or use legitimate credentials with native network and operating system tools, which may be stealthier. |
| Collection | Collection consists of techniques adversaries may use to gather information and the sources information is collected from that are relevant to following through on the adversary’s objectives. Frequently, the next goal after collecting data is to steal (exfiltrate) the data. Common target sources include various drive types, browsers, audio, video, and email. Common collection methods include capturing screenshots and keyboard input. |
| Command and Control | Command and Control consists of techniques that adversaries may use to communicate with systems under their control within a victim network. Adversaries commonly attempt to mimic normal, expected traffic to avoid detection. There are many ways an adversary can establish command and control with various levels of stealth depending on the victim’s network structure and defenses. |
| Exfiltration | Exfiltration consists of techniques that adversaries may use to steal data from your network. Once they’ve collected data, adversaries often package it to avoid detection while removing it. This can include compression and encryption. Techniques for getting data out of a target network typically include transferring it over their command and control channel or an alternate channel and may also include putting size limits on the transmission. |
| Impact | Impact consists of techniques that adversaries use to disrupt availability or compromise integrity by manipulating business and operational processes. Techniques used for impact can include destroying or tampering with data. In some cases, business processes can look fine, but may have been altered to benefit the adversaries’ goals. These techniques might be used by adversaries to follow through on their end goal or to provide cover for a confidentiality breach. |
Techniques:
Techniques are the actual methodology used by adversaries to compromise the network in each stage / tactic. Each tactic can have tens of techniques. Attackers can use the most suitable one of them.
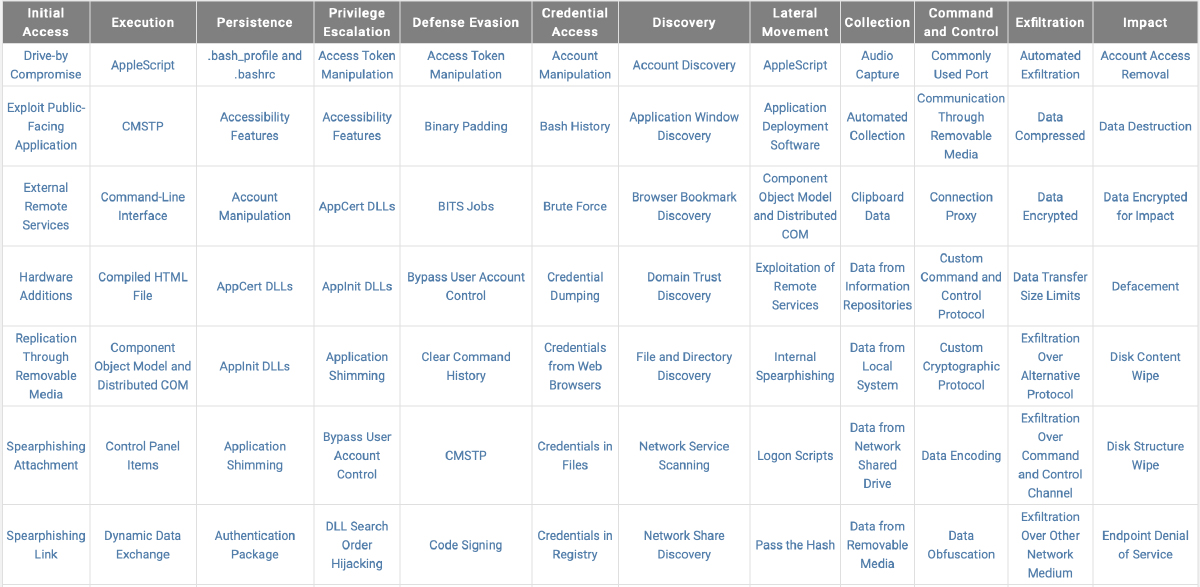
This is exactly where the BLUE and SOC team should spend most of their time on. Each technique should be carefully reviewed, and detection capabilities must be configured for them across the different tools. Security tooling plays a part such as endpoint security, EDR / MDR, NGFW and IPS, NDR, DLP, email security, WAF, MFA, PAM and so on but equally it is important to collect logs from endpoints, servers, domain controllers, hypervisors, applications and databases to be able to build proper detection capabilities.
Leaving even one of them unconfigured would be like sending an invitation to the attacker.
How can SOC analysts make use of MITRE ATT&CK Matrix?
Looking from a SOC analyst’s perspective; each tactic and technique can be a considered useful in building monitoring “use cases”. A SOC analyst should:
- Understand cyber-attacks pertaining to their environment, assets, systems and applications and how they could materialize
- Configure each critical and dependent log source to send relevant security events and audit logs and telemetry data to the SIEM or big data security analytics platform
- Identity how each technique across the different tactics can be identified and detected with these logs.
- Develop and build use cases and rules to detect these techniques being executed; correlate events based of MITRE techniques and generate events
- Configure alerting for triggering these correlation rules and events
- Simulate each technique and ensure the effectiveness of the configured rules and use cases. Threat adversary simulation to be performed here.
- Define response procedure / incident response playbooks for each threat events.