HawkEye AI
Human-Centered ML and AI
Precision-Based Cyber Threat Detection and Response
HawkEye is dedicated to transforming cybersecurity by delivering real-time, AI-powered threat detection and response.
Our mission is to drastically reduce response times, improve threat prediction accuracy, and minimize false positives, enabling organizations to stay ahead of cyber risks with greater precision and efficiency.
HawkEye AI - Goals
Reduce MTTR (Mean Time to Respond)
Increase Unknown Threat Detection Rate
Achieve Reduction in False Positives
Enhance Prediction Accuracy
Leverage AI to improve SOC Analyst Efficiency
Where We Apply AI
- Attack Evolution: Continuously adapting to new attack vectors and strategies across hybrid environments.
- Privileged Activities: Monitoring and analyzing actions taken by privileged users to identify potential risks.
- Cyber Threat Intelligence: Integrating AI to better anticipate and mitigate emerging threats.
- User Behavior and Abuse: Detecting anomalies in user behavior to prevent insider threats.
- Network Traffic: Profiling network traffic in real-time to identify suspicious patterns, outliers and potential breaches.
Human-Centered HawkEye AI
Pattern Matching
HawkEye AI, we utilize pattern-matching AI/ML algorithms to strengthen threat detection by identifying deviations from established behavioral norms.
This includes detecting anomalies such as domain generation algorithm (DGA) patterns in DNS traffic, which are commonly associated with malware communication.
Our system also identifies unusual login activities that could indicate brute-force attacks, as well as lateral movement within the network through abnormal traffic patterns or protocol usage.
Continuously learning from new threat data, our platform adapts to evolving attack techniques and improves its detection capabilities. This proactive approach allows us to identify advanced threats like zero-day attacks and insider threats with high accuracy, while reducing the number of false positives.
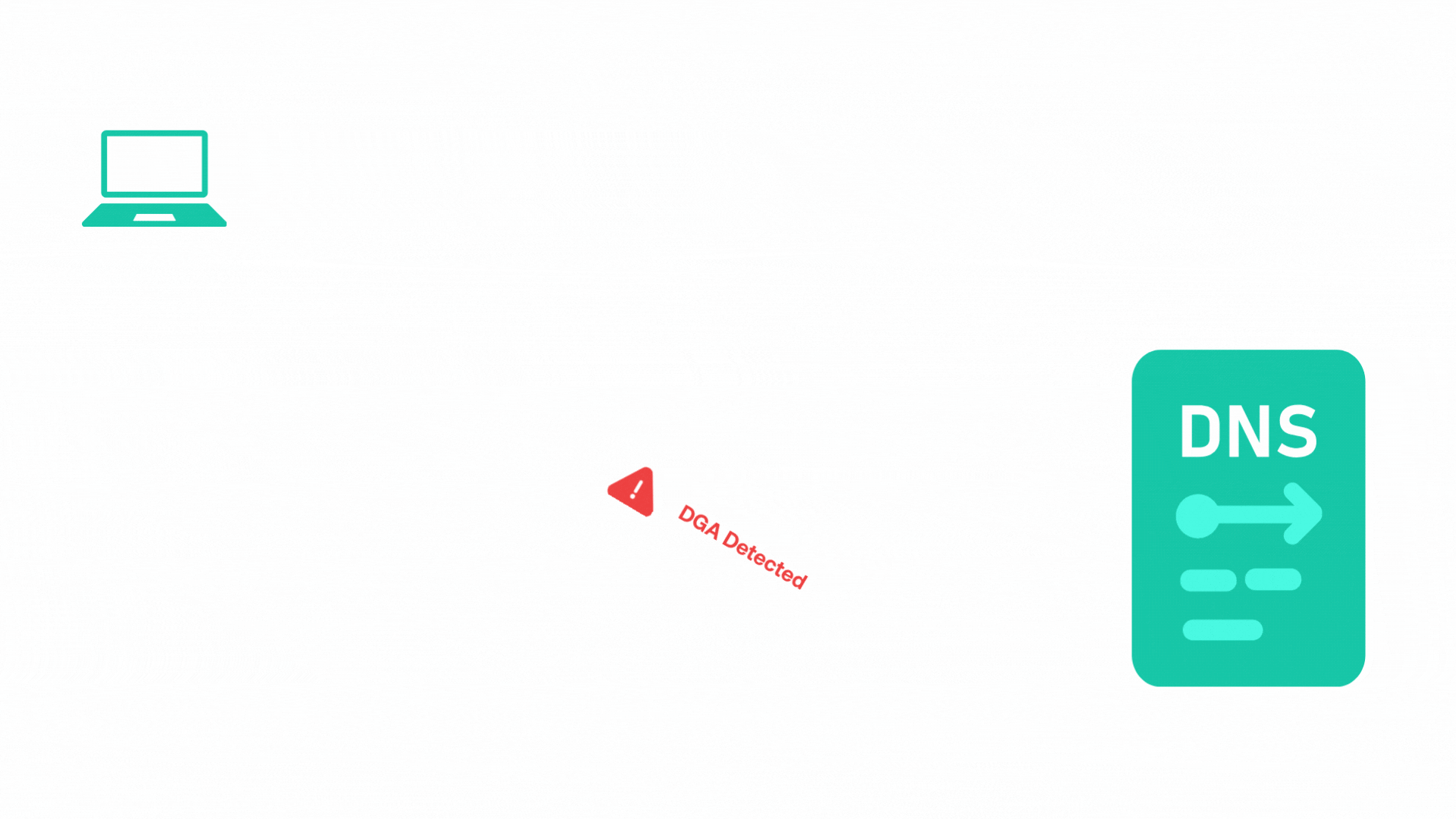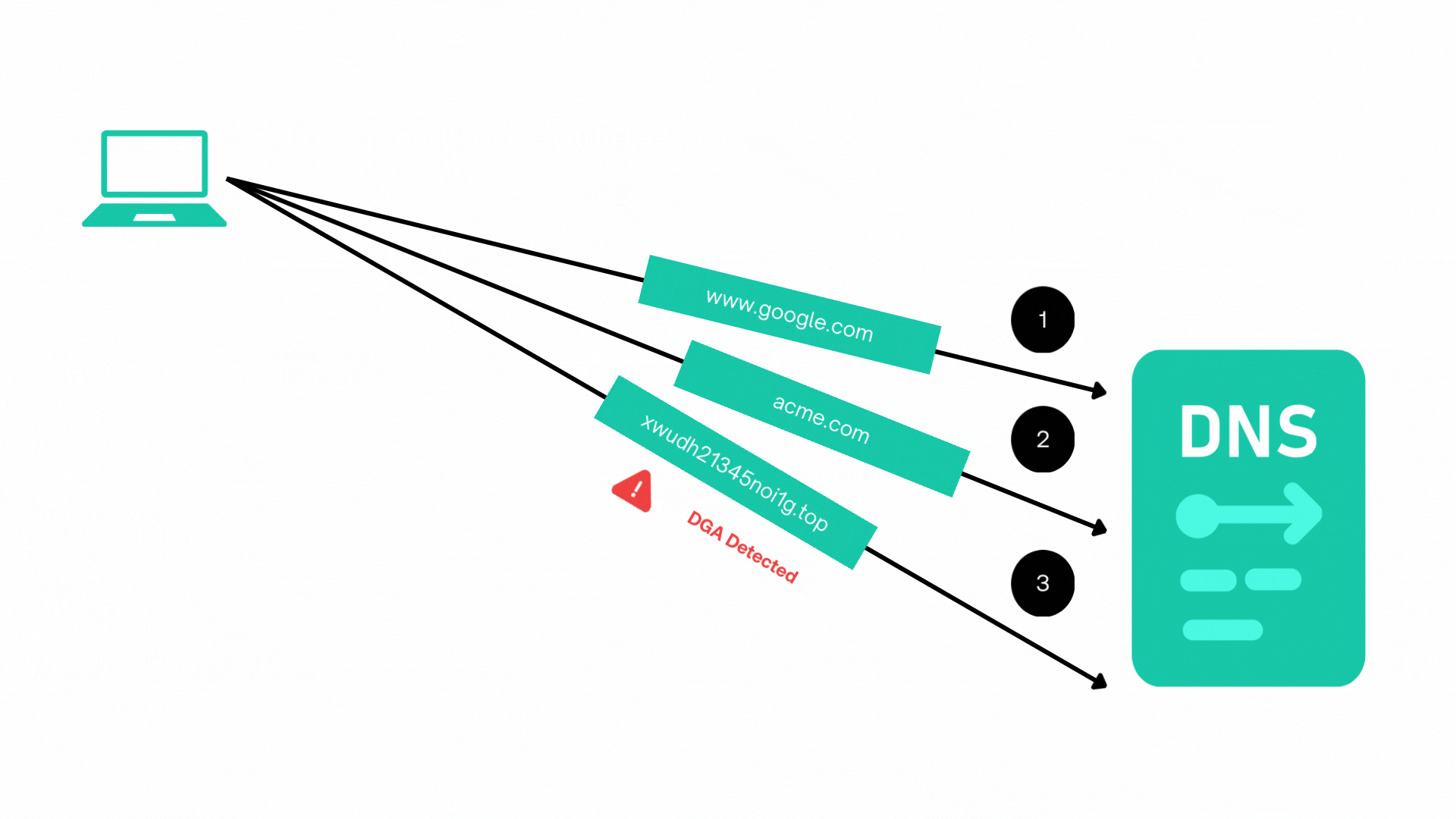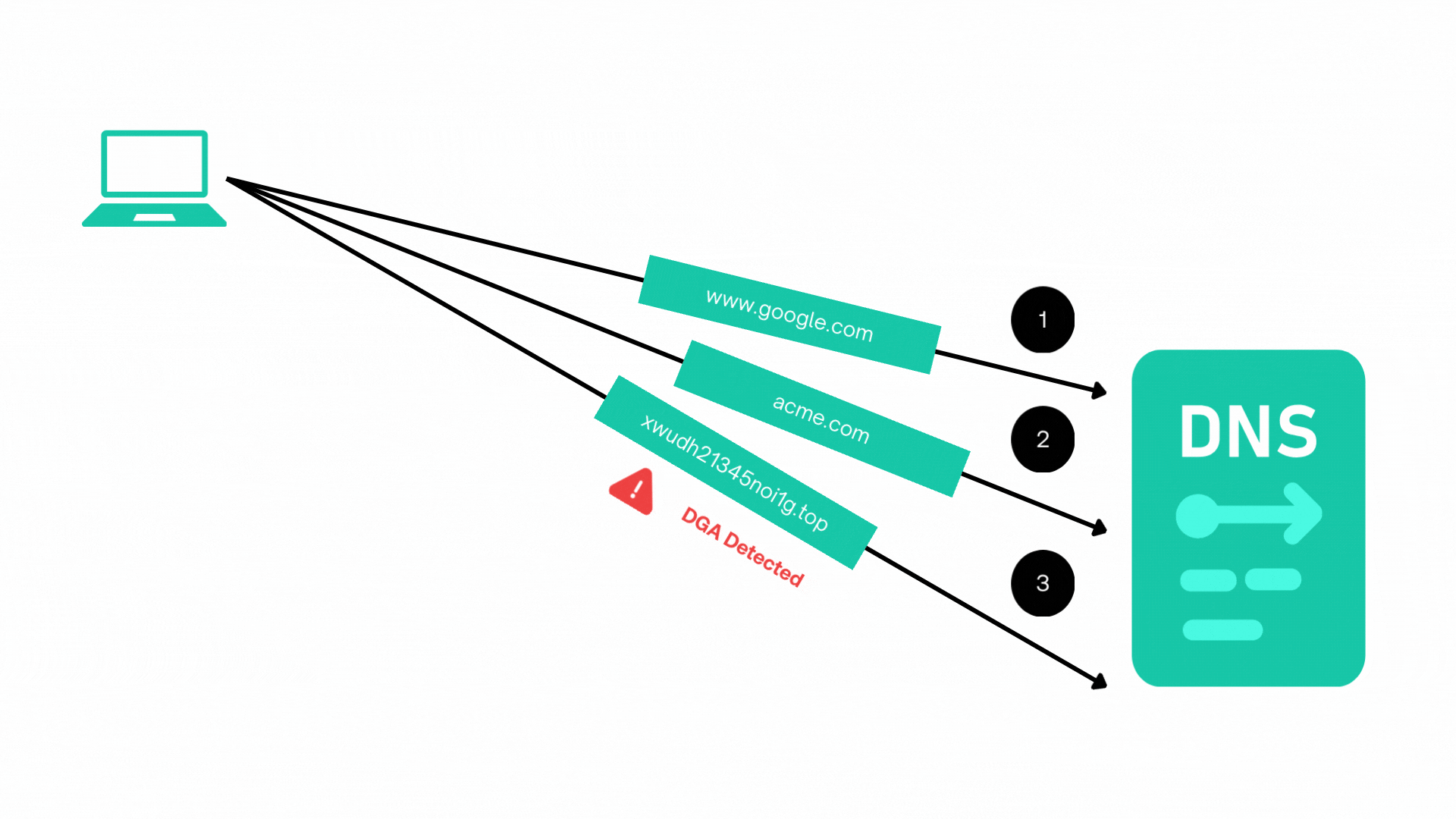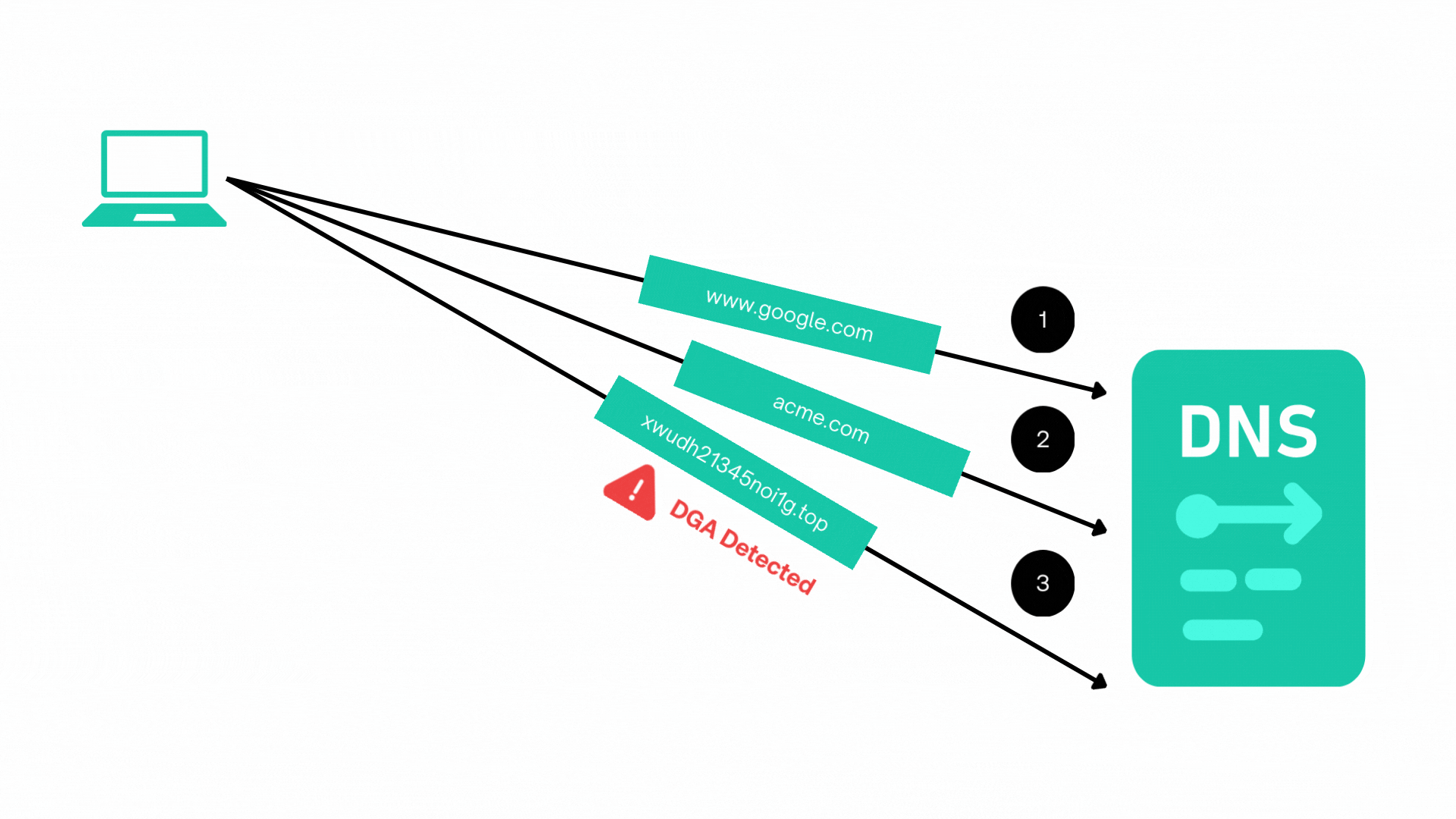
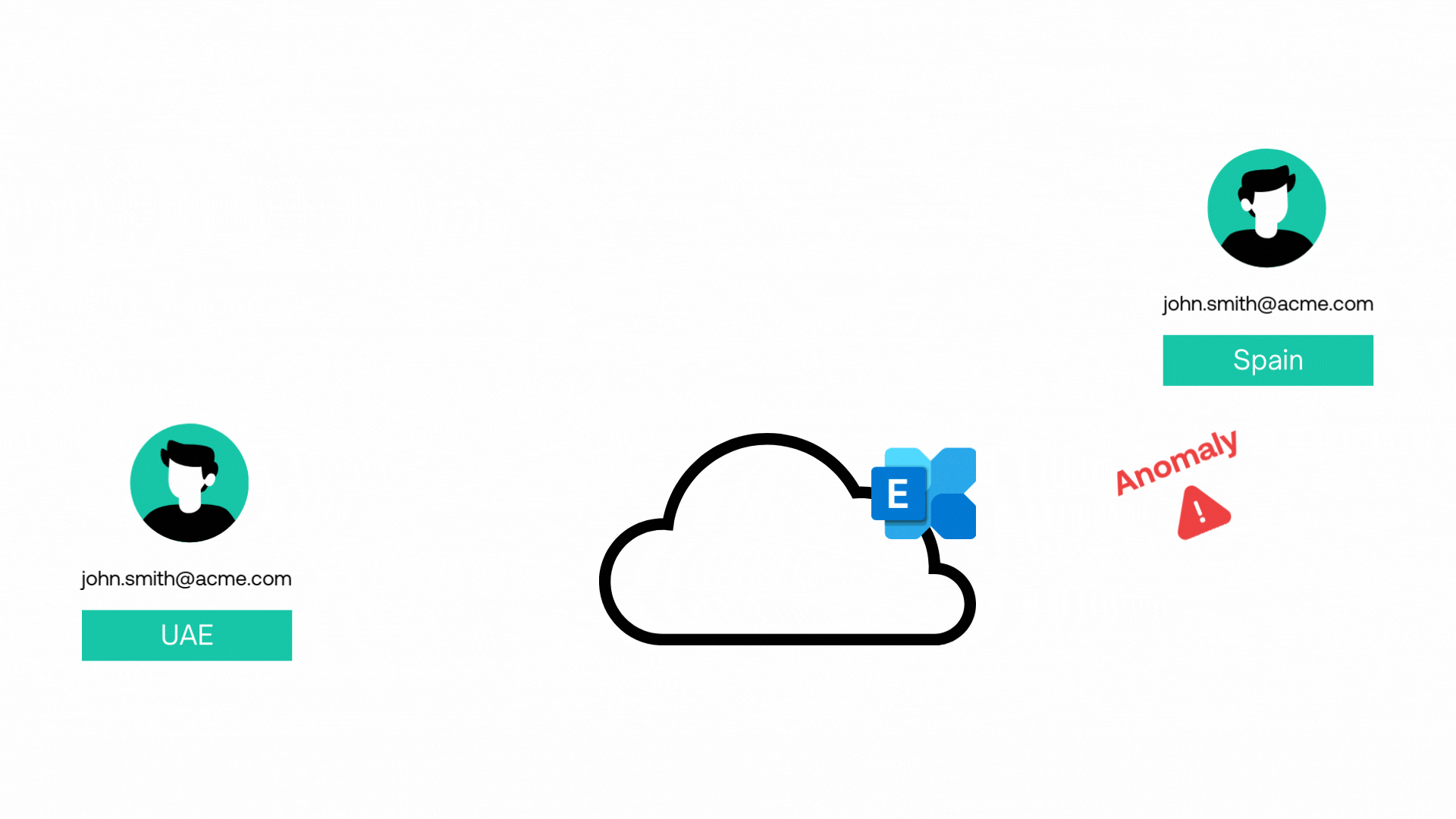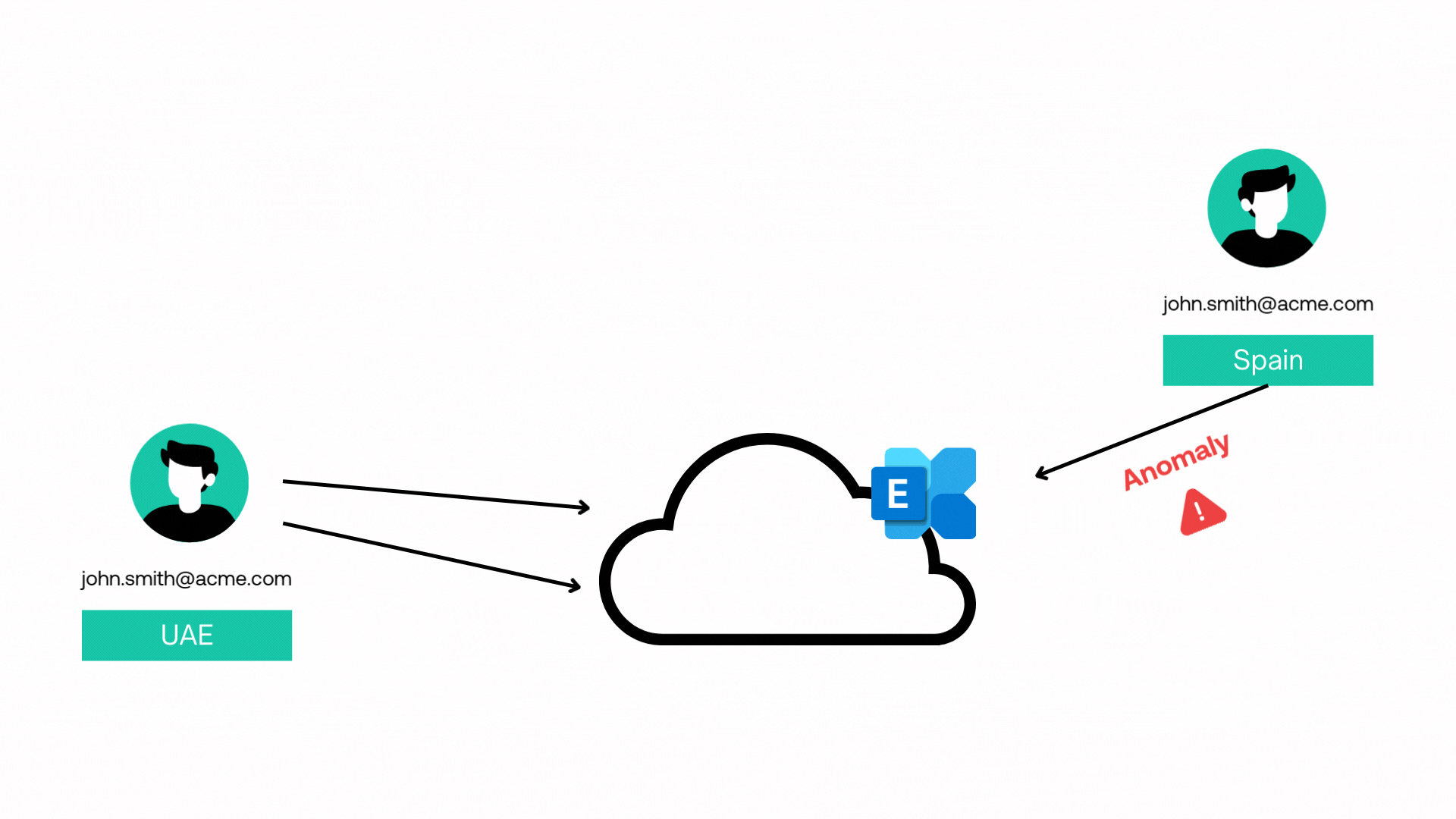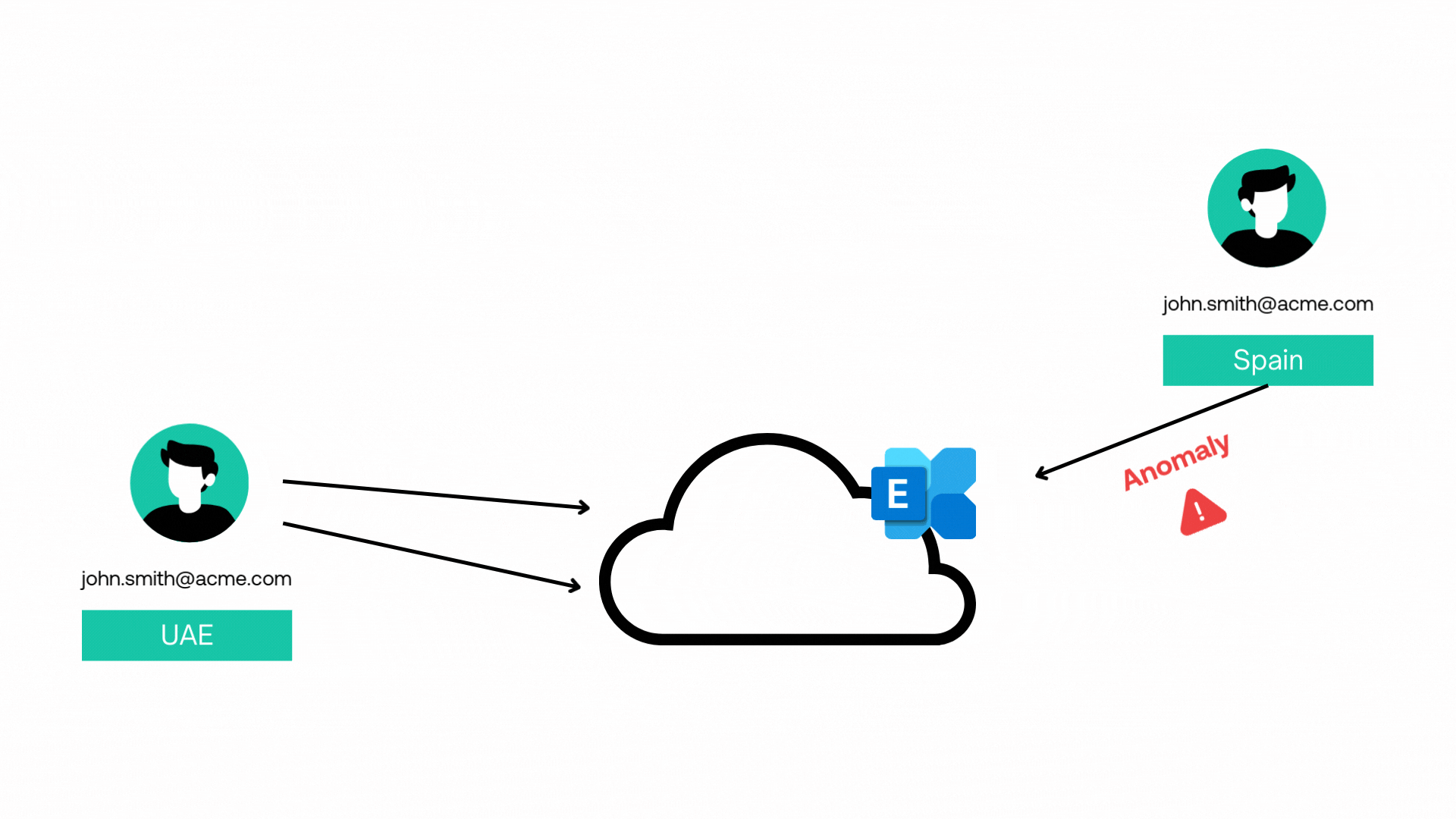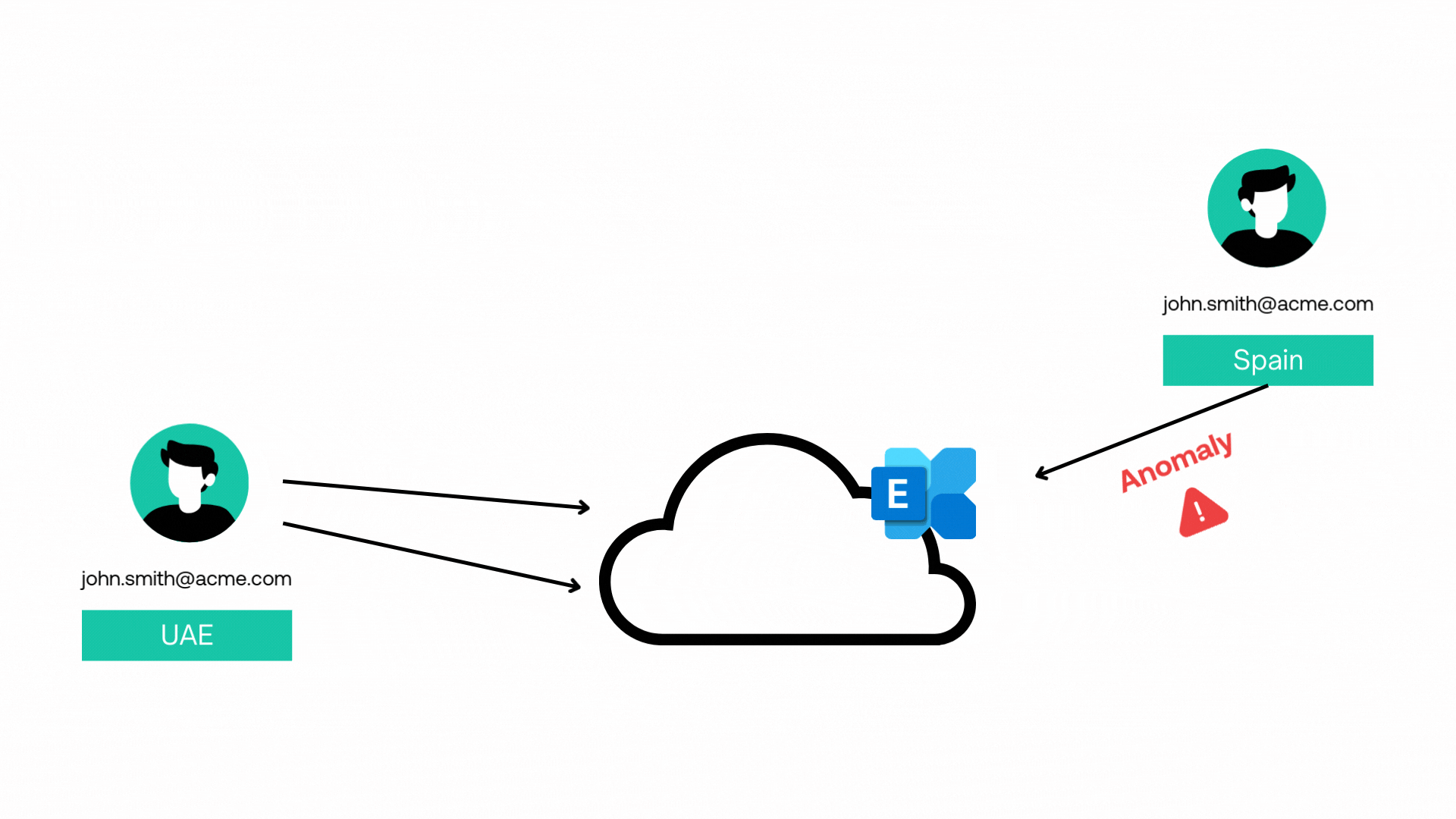
Entity Behaviour Analysis
AI-powered Entity Behavior Analysis helps us detect threats by monitoring and analyzing typical behavior patterns of users, devices, processes and systems what we refer to as entities.
When deviations from normal behavior are detected, such as unusual login locations or activity patterns, AI flags these anomalies for further investigation, allowing us to identify insider threats, compromised accounts, and advanced persistent threats with greater accuracy, precision and speed.
Anomaly and Outlier Detection
Anomaly and Outlier detection using AI enhances our capabilities by identifying deviations from established behavior baselines in network traffic, user activities, and system performance.
This AI-driven approach is highly effective in detecting unknown and unseen attacks and threats by flagging outliers in real-time, enabling us to proactively respond to emerging threats that traditional signature-based detection methods may miss.
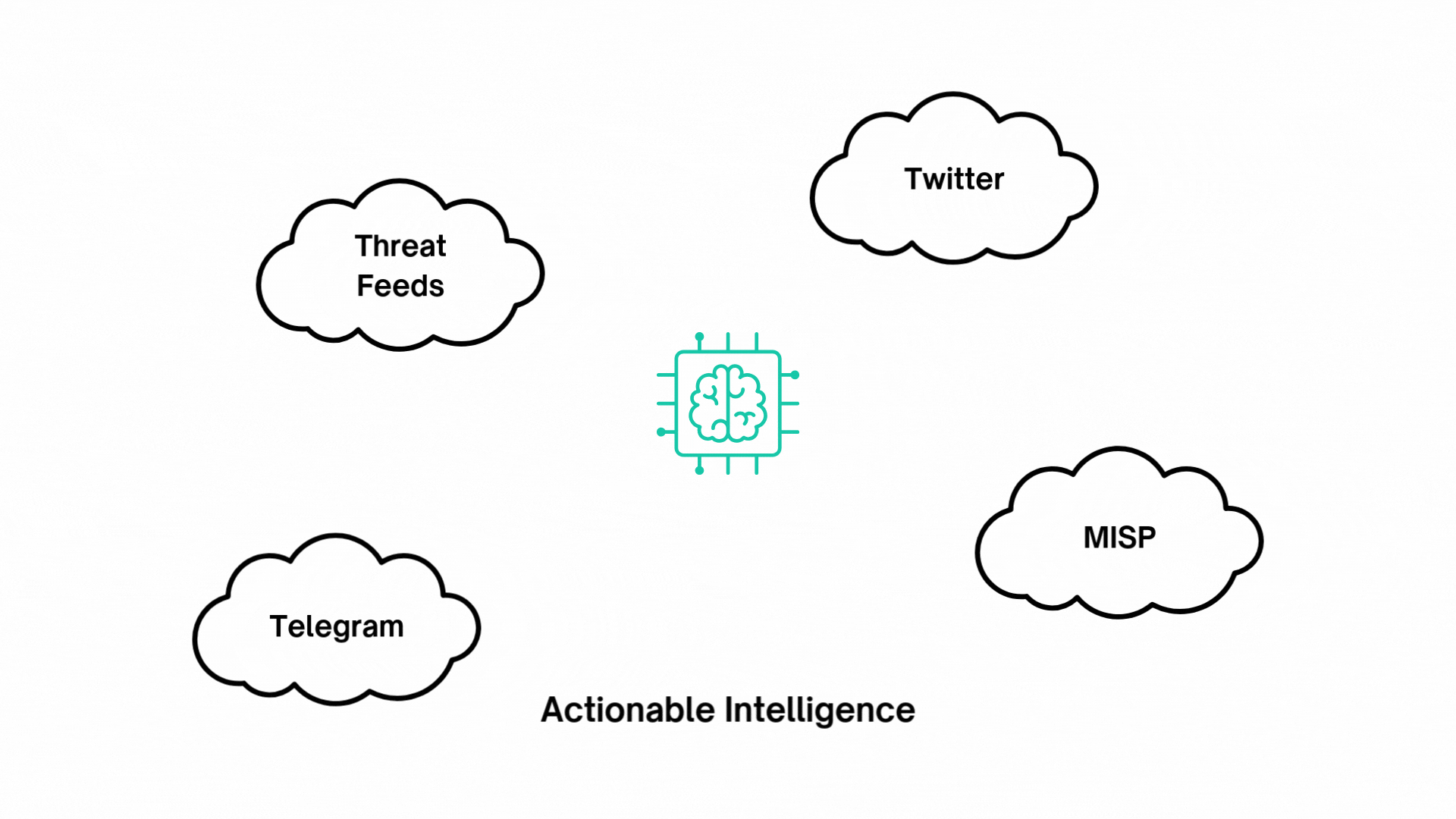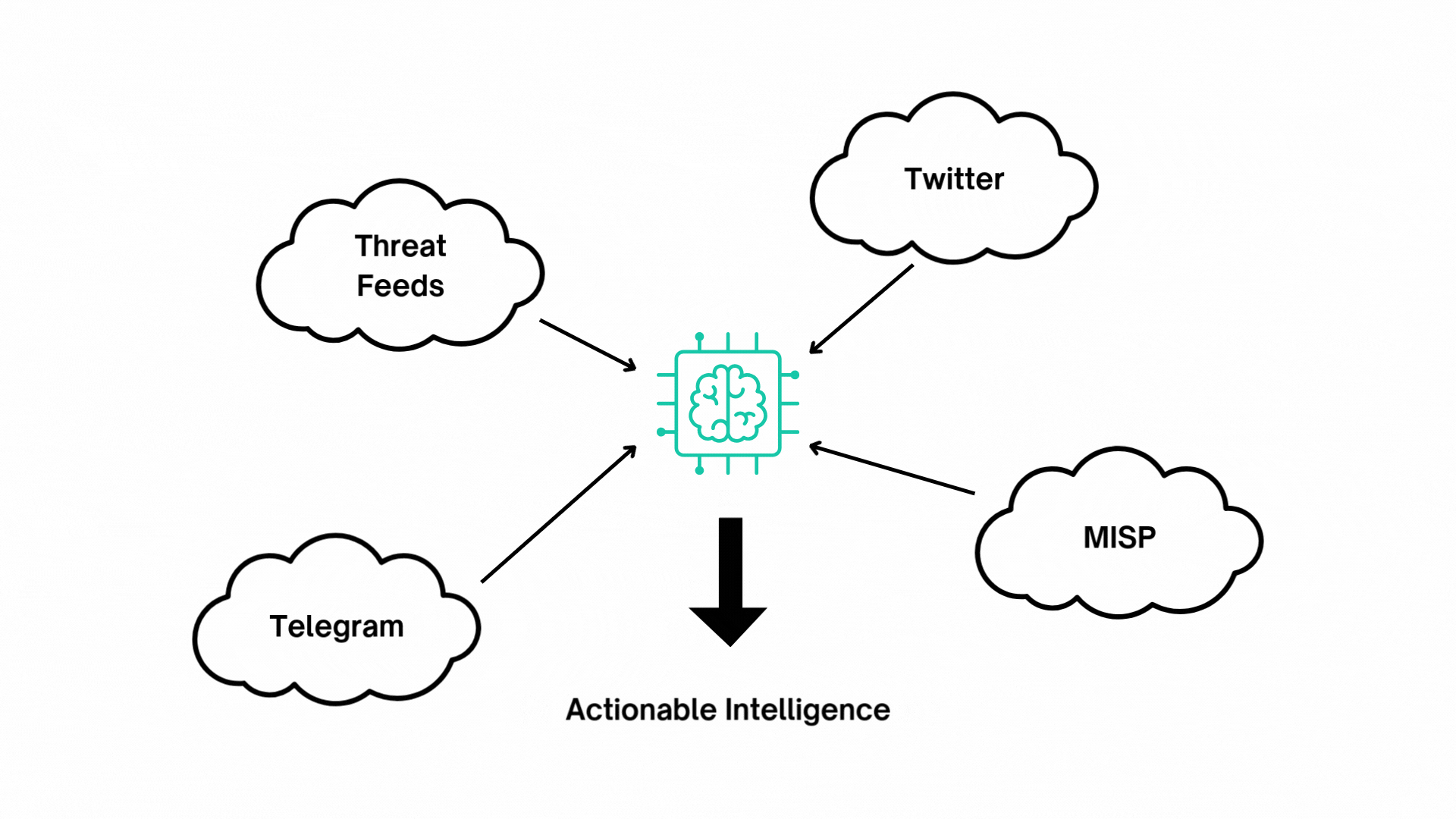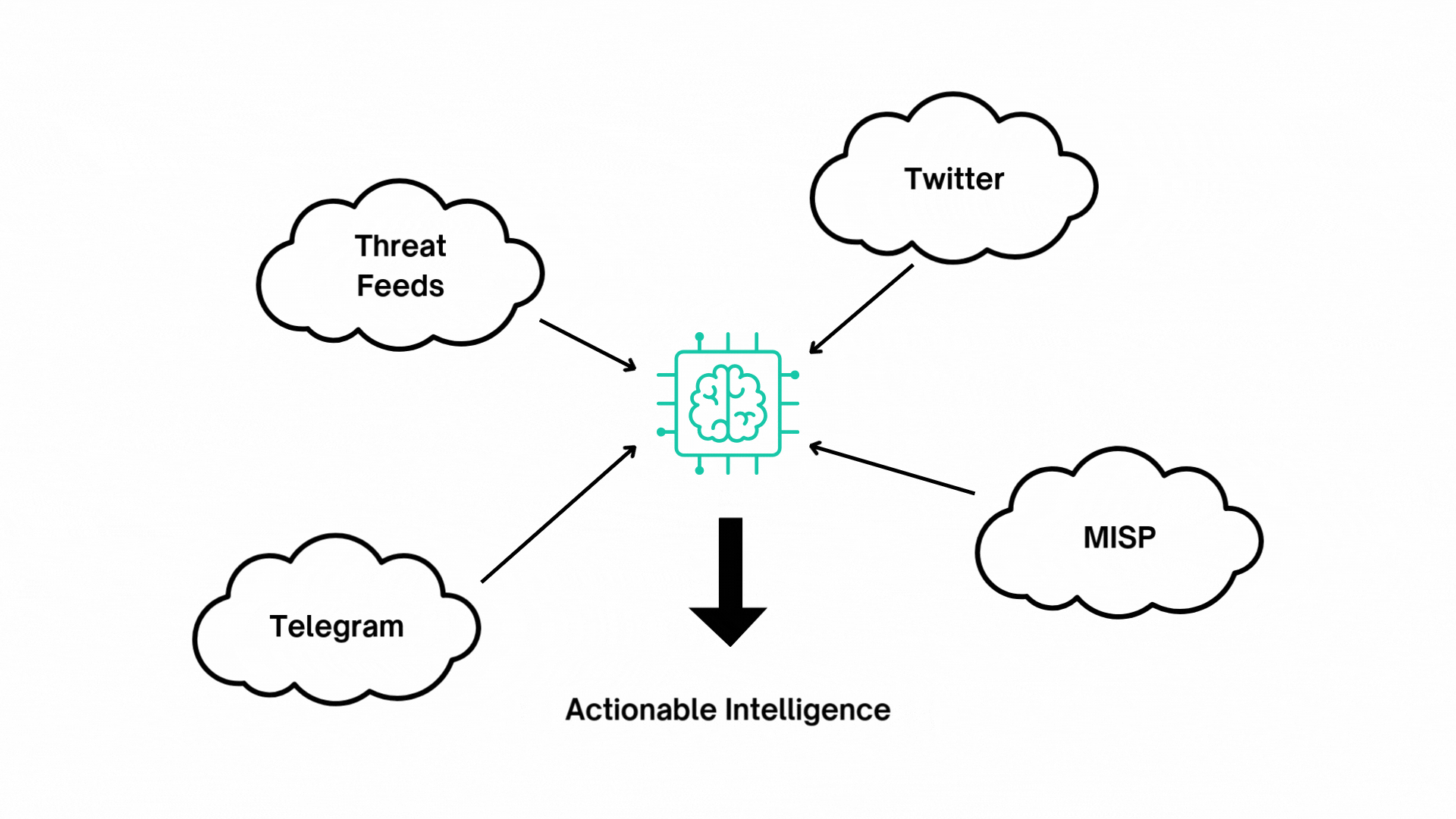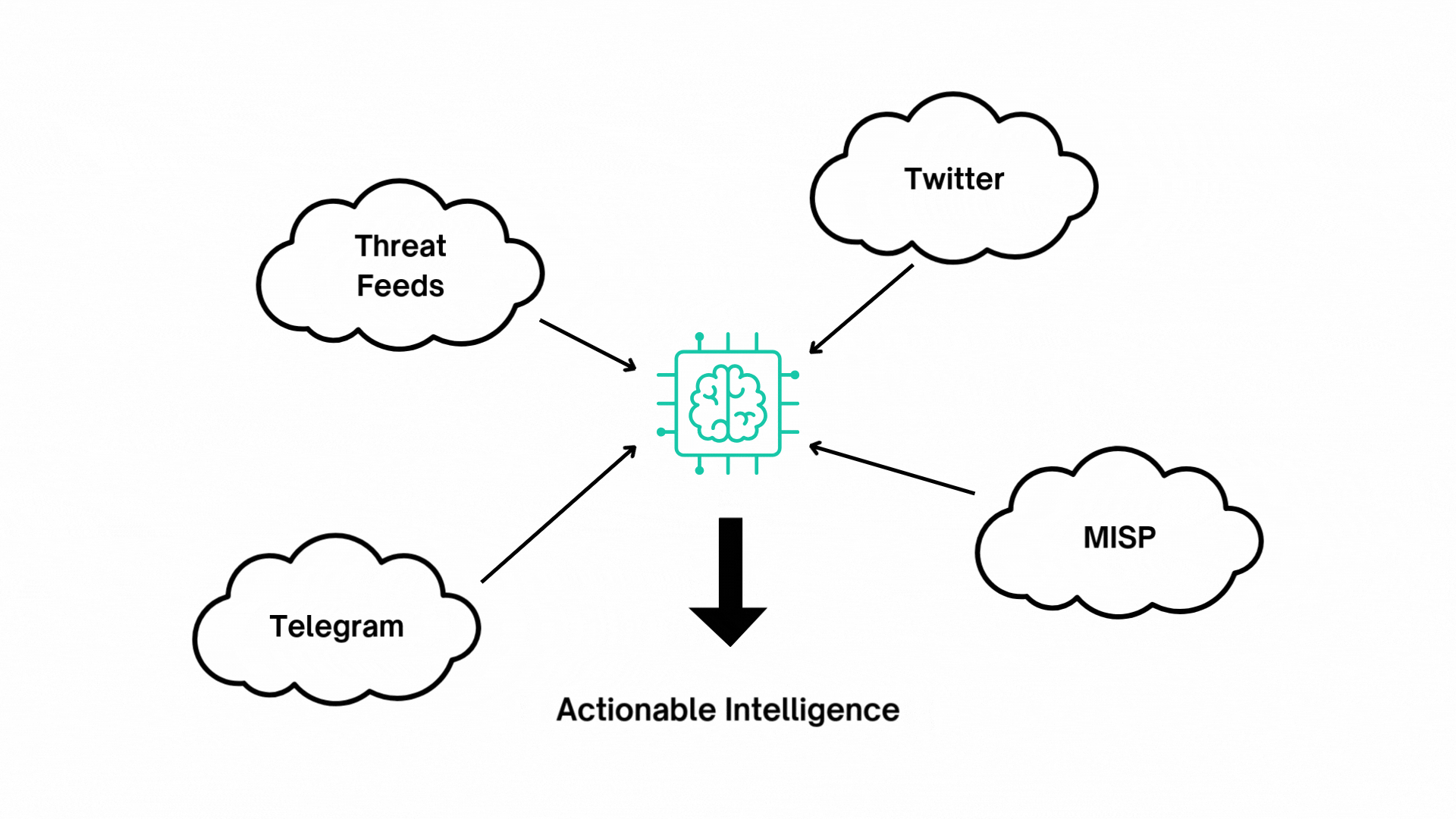
Generative AI in CTI
HawkEye AI utilizes Generative AI to enhance the processing of cyber threat intelligence collected from various sources such as Threat Feeds, Vulnerability Databases, Security Advisories, OSINT, RSS feeds, Tweets, and Telegram.
The AI analyzes this data to determine its relevance, ensuring it is pertinent to your deployed technologies, industries, and specific regions. It then enriches the data by categorizing threats, assessing their severity, and assigning the appropriate level of urgency. This automated process helps prioritize the most critical and relevant threats, enabling us to provide tailored, actionable insights.